Recently, on a Russian-language hacking site, a threat actor posted the whole source code for the Babuk ransomware.
Babuk Locker, also known as Babyk internally, is a ransomware enterprise that began targeting businesses in early 2021 to steal and encrypt their data in double-extortion assaults.
The ransomware gang claimed to have shut down their operation after attacking the Metropolitan Police Department (MPD) in Washington, DC, and feeling the pressure from US law enforcement.
Members of the same organization, however, split away and re-launched the ransomware as Babuk V2, which is still encrypting victims to this day.
Release of Babuk’s source code on a Hacking Forum
A suspected member of the Babuk group posted the whole source code for their ransomware on a famous Russian-language hacking forum, as first detected by security research firm vx-underground.
This member claimed to be dying of cancer and opted to release the source code while still having to “live a human life.”
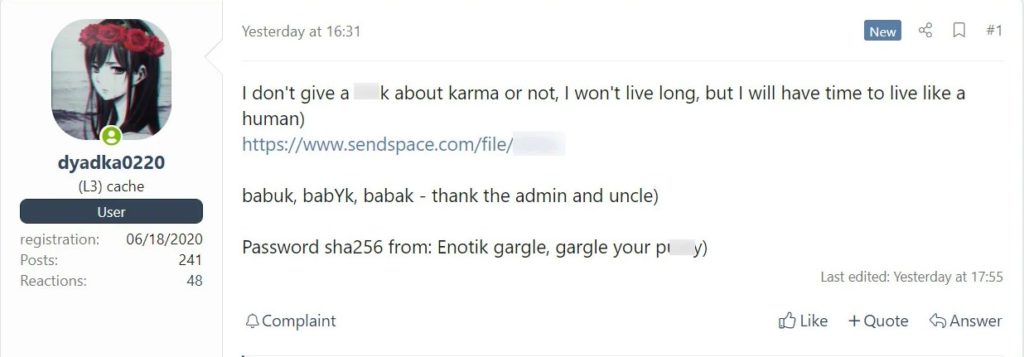
We redacted the links to the source code because the disclosure provides everything a threat actor needs to develop a working ransomware executable.
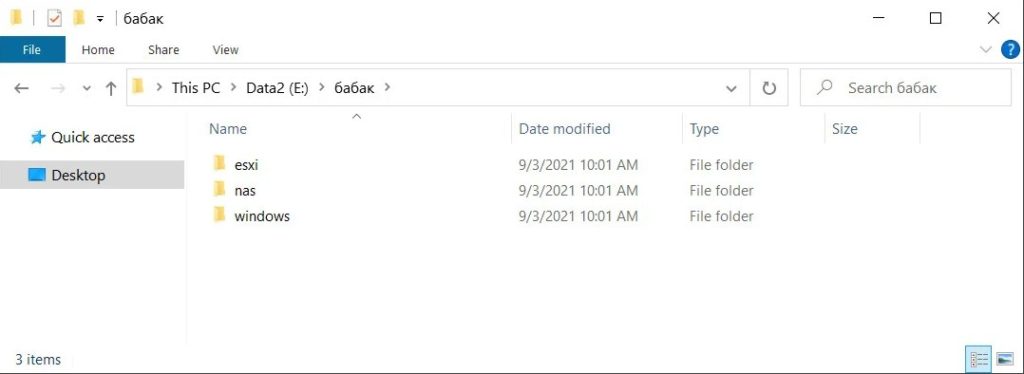
As illustrated below, the shared file comprises many Visual Studio Babuk ransomware projects for VMware ESXi, NAS, and Windows encryptors.
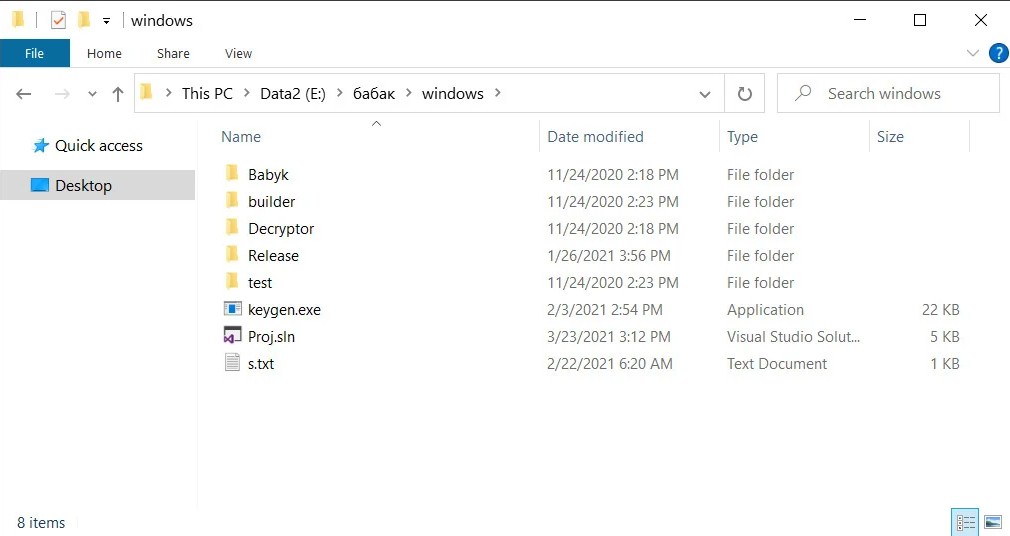
The whole source code for the Windows encryptor, decryptor, and what looks to be a private and public key generator can be found in the Windows folder.
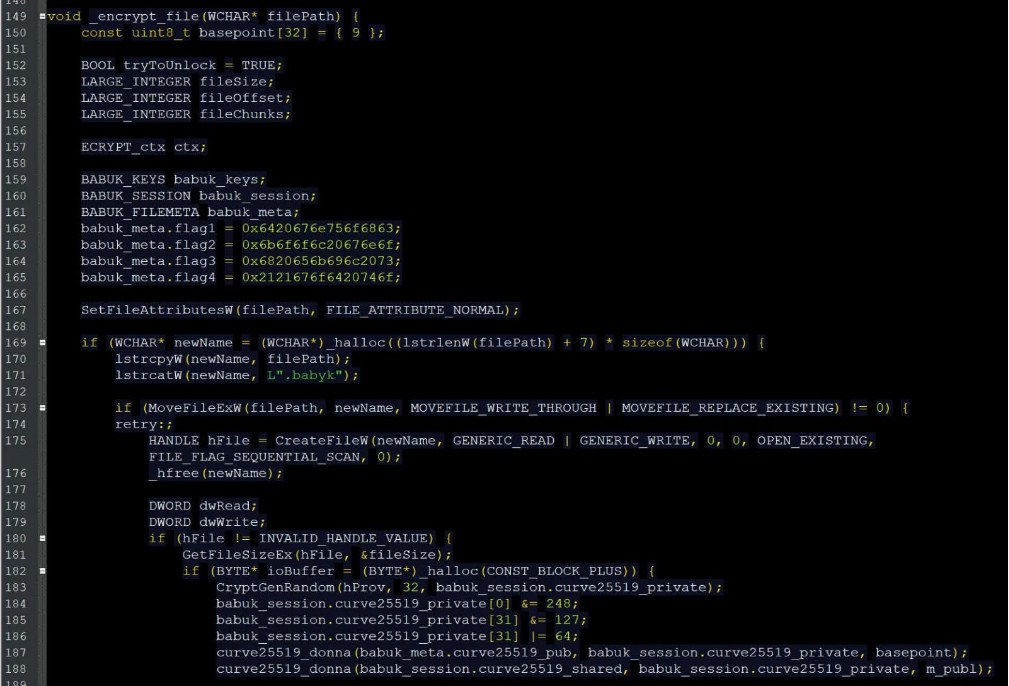
The source code for the encryption routine in the Windows encryptor, for example, can be found below.
The leak appears to be authentic, according to a leading ransomware expert and other researchers. According to the senior researcher, the leak could contain decryption keys for previous victims.
The encryption routine of the Babuk ransomware includes elliptic-curve cryptography (ECC). Folders containing encryptors and decryptors compiled for specific ransomware victims are included in the release.
These folders may possibly include curve files that could constitute the ECC decryption keys for these victims, according to the senior researcher, but this has yet to be validated.
A tale of treachery and betrayal
Babuk Locker had a tumultuous and public history of treachery and backstabbing, which resulted in the group’s disintegration.
According to one of the Babuk ransomware gang’s members, the group divided after the attack on the Metropolitan Police Department of Washington, DC (MPD).
The ‘Admin’ apparently planned to reveal MPD data for publicity after the incident, but the other gang members were against it.
The same member of the gang was quoted saying, “We’re not good guys, but even for us it was too much.”
Following the data breach, the group separated, with the original Admin founding the Ramp cybercrime forum and the remainder launching Babuk V2, a ransomware assault platform.
Soon after the Ramp cybercrime forum was launched, it was subjected to a series of DDoS attacks, rendering the new site inoperable. The Admin blamed his former partners for the attacks, but the Babuk V2 team denied responsibility.
A Babuk ransomware generator was leaked on a file-sharing site and was utilized by another organization to launch their own ransomware operation, adding to the group’s scandal.
Babuk appears to be far from alone in their tales of backstabbing and betrayal.
After the previously stated senior researcher set up a Jabber account for threat actors to contact him, he tweeted that he has gotten information from threat actors who feel “wronged” by their partners and have opted to leak information in retaliation.
According to an IT publication, the senior researcher has been able to exploit this information to avoid further ransomware attempts.
To read more, please check eScan Blog







