Yet another ransomware targeting corporate networks have been discovered. The Conti Ransomware is an upcoming threat armed with new features that allow it to perform quicker and more targeted attacks. While Conti’s distribution is increasing, it is suspected that this ransomware shares the same malware code as Ryuk, who has slowly been fading away into digital oblivion.
Distributed in isolated attacks the ransomware was first sighted in December 2019. However, until the end of June, the attacks slowly increased.
Like the other ransomware threats that we have covered in our blog, Conti operators can breach corporate networks and spread laterally until they gain domain admin credentials. The threat actors then deploy the ransomware to encrypt its devices once administrative privileges are achieved.
It is not known at this time if the Conti operators also steal files from their victims’ networks before encrypting, just like the WastedLocker Ransomware that we covered on our blog last week.
The Ryuk-Conti Connection
In August 2017, a Russian speaking threat actor was reported selling the Hermes Ransomware on the exploit.in hacking forum. It is believed that another threat actor purchased this ransomware and then transformed it into what we know today as the Ryuk Ransomware.
It appears that the threat actor behind Ryuk, rebranded the ransomware or decided to rename as Conti, since the ransomware seems to be based on the code from Ryuk version 2.
While exhibiting more similarities, a more descriptive Conti ransom note has been seen that use the same exact template used by Ryuk in earlier attacks.

Both Ryuk and the Conti threat actors as part of ransomware attacks have been using the same trickbot infrastructure, in addition to the similarities of the ransomware notes.
It is believed that Conti ransomware is linked to the same Ryuk ransomware developer group based on the code reuse and unique TrickBot distribution. The Ryuk deployment group widely uses the same distribution attack vector. This assessment is based on multiple incident response matters and current assessment of the two ransomware.
While it is not clear if Conti is a successor to Ryuk but researchers have clearly noticed the Conti attacks increasing and Ryuk diminishing.
Deep Dive into Conti Ransomware
Researchers have provided some insights into some of the features of the Conti Ransomware.
According to the researchers, Conti will prepare the computer for encryption by stopping 146 Windows services related to security, backup, database, and email solutions, when it is first started. It will then clear the Shadow Volume copies and begins to encrypt the computer.
The ransomware will append the .CONTI extension to encrypted files and drop a ransom note named CONTI_README.txt in each folder when encrypting a computer.
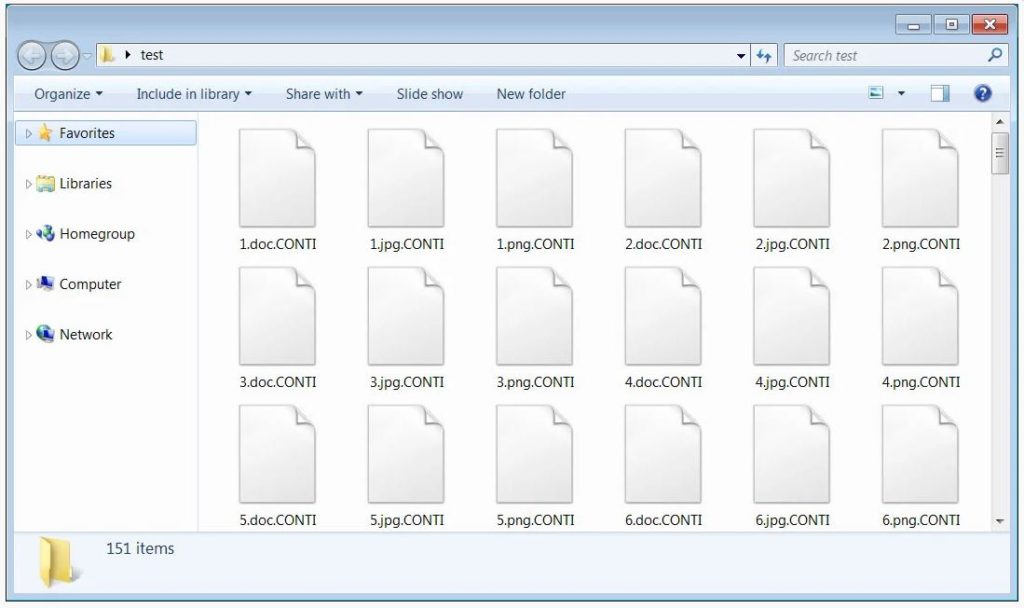
Researchers have further added that when encrypting data, the ransomware will use a unique AES-256 encryption key per file, which is then encrypted with a bundled RSA-4096 public encryption key.
Every victim has a unique RSA key.
similar to how Ryuk creates their ransom notes, Conti’s ransom note contains the barest amount of details regarding the attack and how to contact the attackers.

The average ransomware demand for this ransomware is relatively low compared to other similar ransomware infections.
To refine the encryption process, Conti supports an ‘–encrypt_mode’ argument that modifies the default behavior of the ransomware. When using ‘—encrypt_mode local,’ only the local drives are encrypted, and when using the ‘—encrypt_mode network,’ only the network shares are encrypted.
To specify a list of IP addresses to target for encryption, Conti also supports the ‘-h’ argument.
Some of the other features of the ransomware are described below.
Multiple thread encryption
Conti will use multiple threads to encrypt different files simultaneously. Its use of 32 threads stands out and allows the ransomware to encrypt a machine at very fast speeds. However, this speed comes with a trade-off, as a significant increase in CPU and disk utilization is noted that causes the machine to slow down and become sluggish.
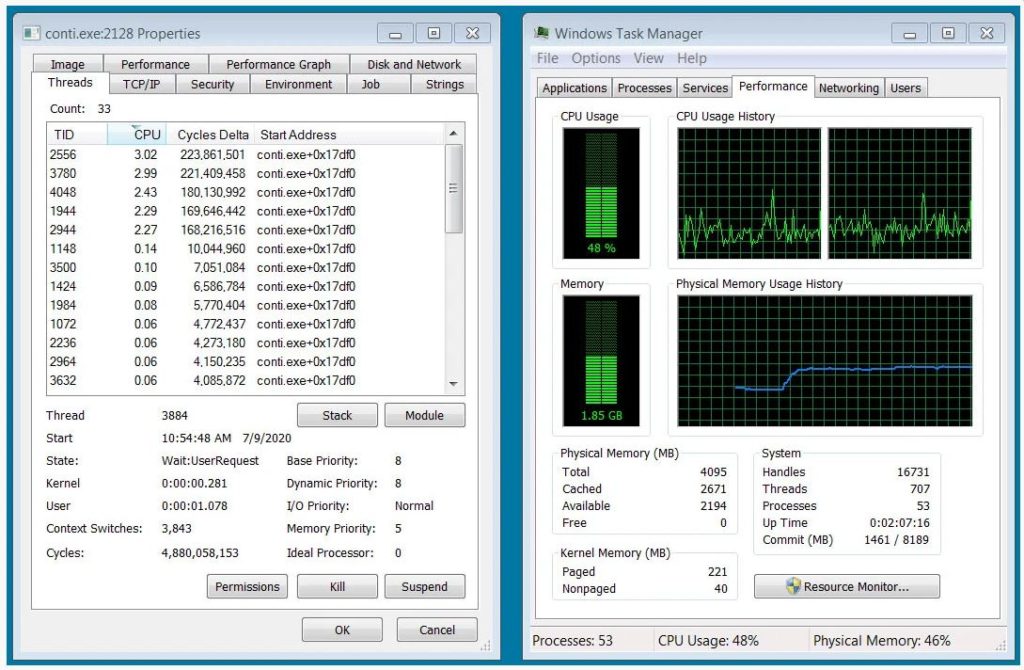
These symptoms can easily lead to the discovery of the ransomware.
This may not be much of a concern as the computers would not be used during the encryption process, as most of the ransomware attacks occur after hours.
Utilizes the Windows restart manager
Conti will use a Windows API called the ‘Windows Restart Manager’ that will terminate processes or Windows services that keep a file open during encryption.
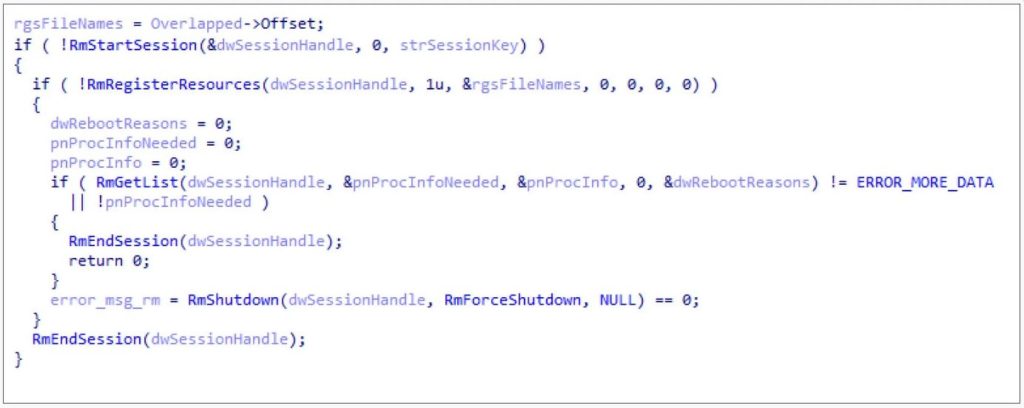
Ransomware infections are now starting to utilize this tool created by Microsoft to encrypt databases and other important files that are inaccessible while opened by another process.
The number of system restarts that are required to complete an installation or update can be reduced or eliminated with the Restart Manager API. Some of the files that are being updated are currently being used by a running application or service is the primary reason why software updates require a system restart during an installation or update. The Restart Manager enables all but the critical system services to be shut down and restart, freeing the files in use and allowing installation operations to complete.
Conti is not the first ransomware to utilize this API.
REvil (Sodinokibi), Medusa Locker, Sam Sam, and LockerGoga are also utilizing the Windows Restart Manager API during their encryption, and in some cases, the decryption process.
With Conti’s increased distribution and advanced features, this ransomware is one that we will need to keep an eye on.
IOC’s:
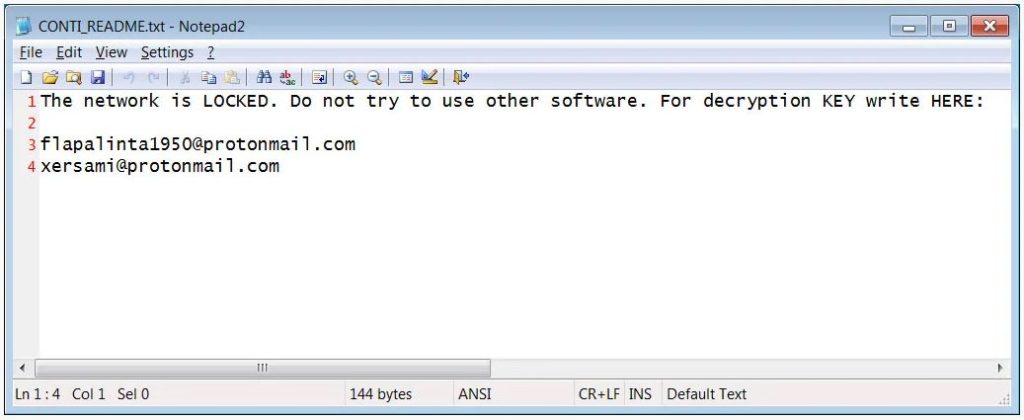
Associated File Names: CONTI_README.txt
Associated Emails: flapalinta1950@protonmail.com xersami@protonmail.com
Ransomware note –
The network is LOCKED. Do not try to use other software. For decryption KEY write HERE:
flapalinta1950@protonmail.com xersami@protonmail.com
To read more, please check eScan Blog







