The Babuk gang seems to have slipped back into its old habits of encrypting company networks after announcing its withdrawal from the world of Ransomware in favor of data-theft extraction.
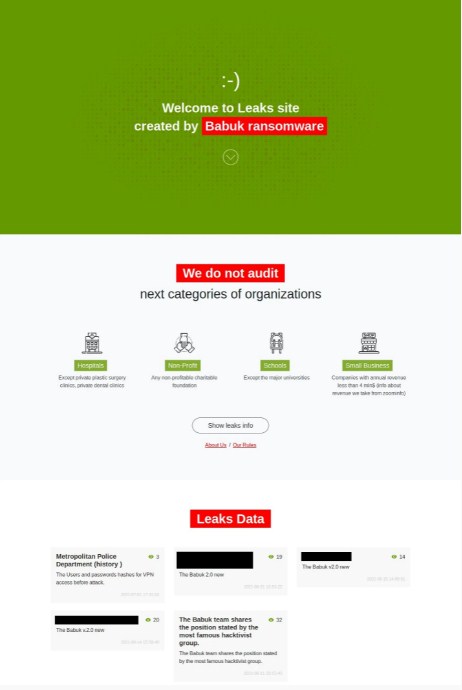
The cybercriminals behind Babuk are currently using a new version of their file encryption software and have relocated the operations to a new leak site, where a few victims are listed.
The Babuk group ransomware became known early this year, but the gang says its attacks began in the middle of October 2020, aiming at firms all over the world and normally asking for payments in Bitcoin cryptocurrency between $60,000 to $85,000. In certain cases, hundreds of thousands were demanded from the victims to decrypt data.
The Washington DC Metropolitan Police Department is among the most popular victims (MPD). This attack probably led the actor to declare his withdrawal from the ransomware business only to adopt a different extortion technique without encryption.
The Gang also stated plans to disclose their virus to let others establish an operation using ransomware as a service. The threat actor behind Babuk followed his word and disclosed its manufacturer, a tool that produces unique ransomware.
A security investigator published this information to further help the infosec community detect and decrypt it.
The gang took the name PayLoad Bin after shutdown in April, however, its leak site does not reveal much activity. Rather, a new leak website with the Babuk ransomware mark was launched across the dark web.
This site mentions less than five victims who refused to pay the ransom and who were targeted with a second malware variant.
The encryption-based extortion game does not appear to have been discarded by Babuk. They just published their old software and generated a new version for the ransomware business.
This was made clear by the gang in a comment on a tech-journalism website on the wave of ransomware assaults utilizing the leaked Babuk function and demanding approximately $200 bitcoins – proving clearly that it is not the original authors using it.
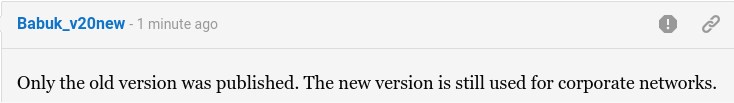
It seems that the Babuk gang is not prepared to stop encrypting files and continues to concentrate on the business networks for higher payouts.
What led the organization to return to their previous activities is unknown, however, given how empty the leak site of PayLoad Bin is, one may guess that extortion from data robbery was not doing very well.
It remains unknown at this time whether the same members that attacked Washinton D.C. Metropolitan Police are behind the new Babuk operations.
To read more, please check eScan Blog







