A Ransomware that not only encrypts your files but also delivers a message displaying its support towards the ongoing farmer’s protest in India, has been detected by researchers.
A new set of laws were passed by the Indian government last year, which is also known as Farm Bills or ‘Indian agriculture acts of 2020’, which the government says is necessary to modernize its agricultural industry.
According to the farmers, this new law will hurt their livelihoods and make it more challenging to generate revenue as the new laws removed restrictions on how farmers can sell goods and for how much.
Thousands of Indian farmers have been protesting these bills outside of New Delhi, since November 2020.
The Sarbloh Ransomware
As described by various researchers, a new malware is being distributed through malicious Word documents that contain a political message in support of Indian farmers. This ransomware is called Sarbloh.
At present, the method by which its sent is unknown but when opening it, users will be prompted to ‘Enable Content’ to view its content correctly.
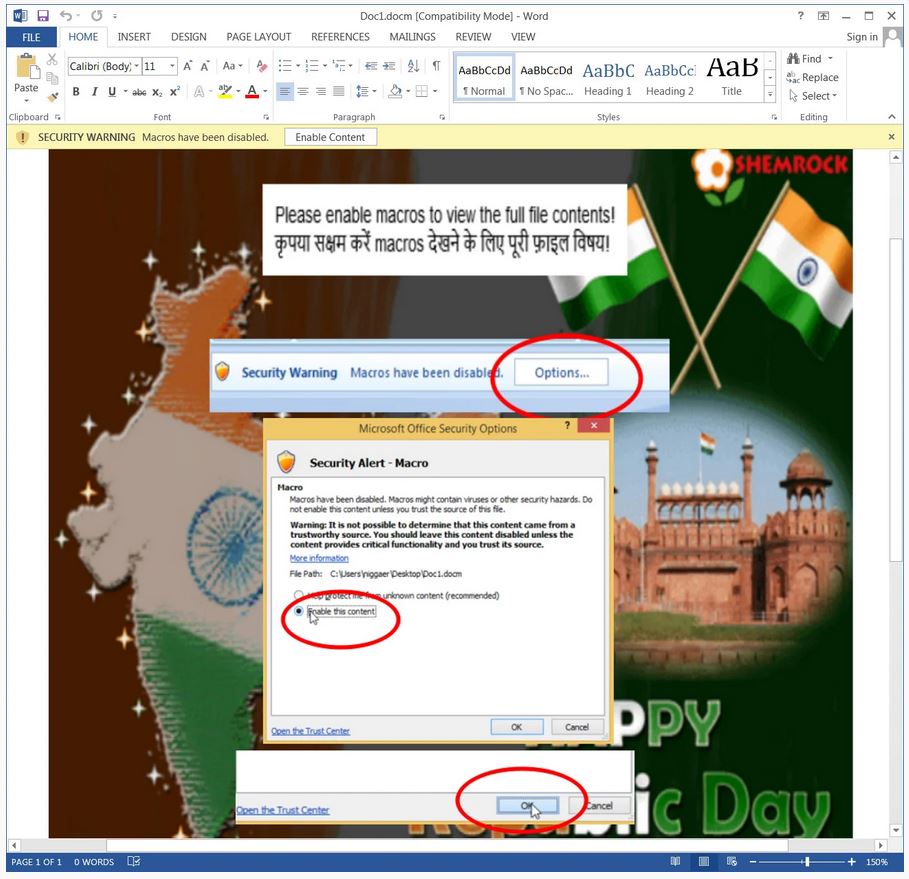
The payload is delivered using a DOCX file, which has macros, with autorun – auto-blocked by the eScan Compound Files engine. Furthermore, DOCX is distributed via mailspam to users gets blocked by MailScan at Gateway level, by default.
While the payload that is downloaded from amazon AWS, again gets blocked by eScan’s HTTP/HTTPS filter, owing to EXE file masquerading as PNG.
All eScan Enterprise Security Solutions, using PBAE, will proactively block this ransomware, even on air-gapped networks.
On its execution, the ransomware encrypts files on a given computer using AES-256 and appends the .sarbloh to the file’s name. For example, the file Hello.jpg would be encrypted and renamed to Hello.jpg.sarbloh.
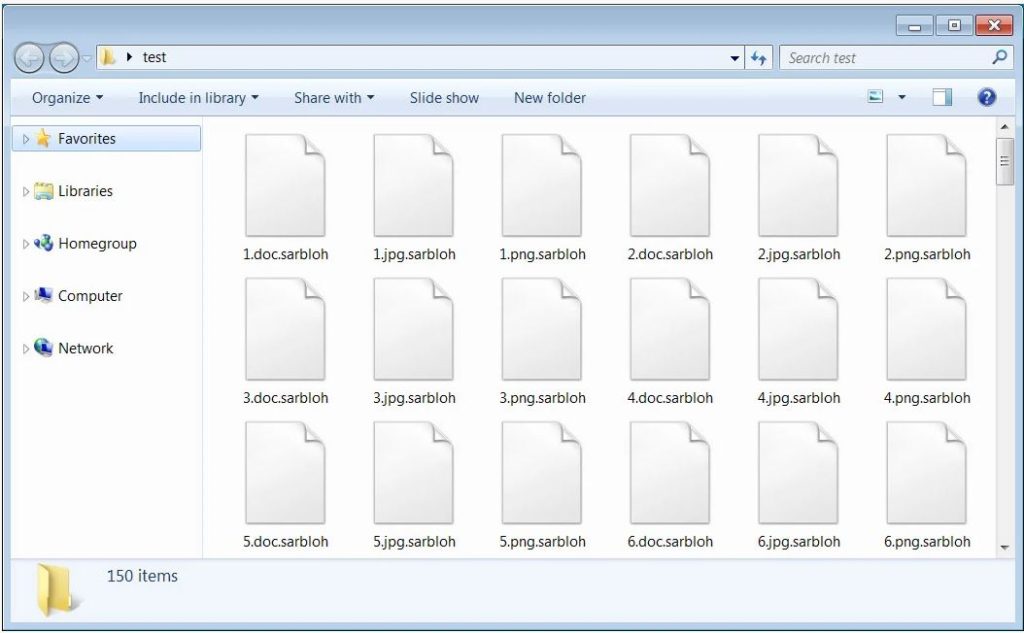
After the encryption process is complete, a ransom note will be created called README_SARBLOH.txt that contains a message supporting the farmers in India.
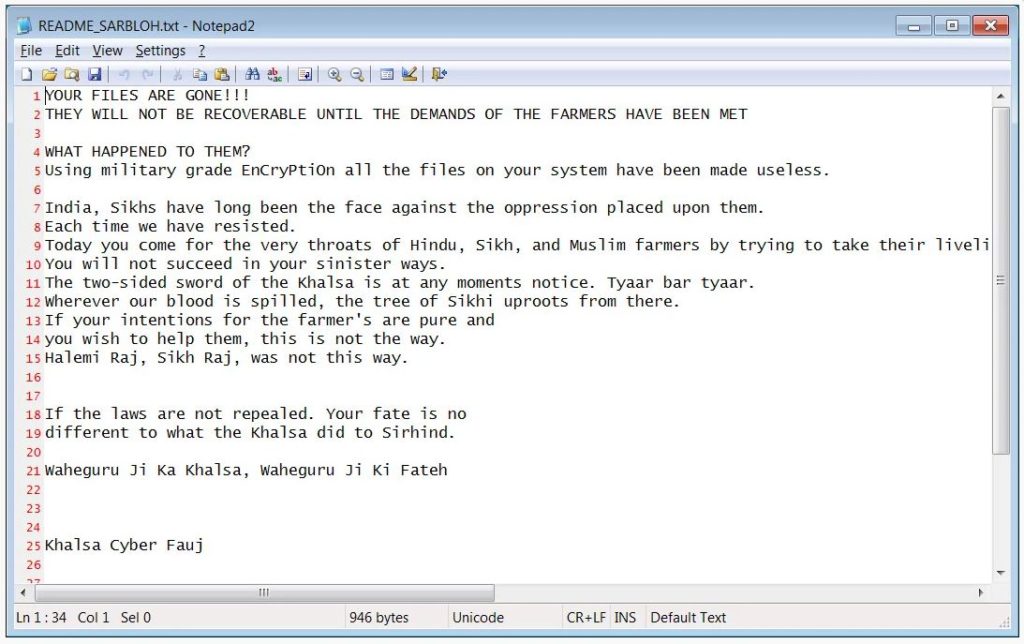
The contents of the Ransom note can be read below –
YOUR FILES ARE GONE!!!
THEY WILL NOT BE RECOVERABLE UNTIL THE DEMANDS OF THE FARMERS HAVE BEEN MET
WHAT HAPPENED TO THEM?
Using military-grade EnCryPtiOn all the files on your system have been made useless.
India, Sikhs have long been the face against the oppression placed upon them.
Each time we have resisted.
Today you come for the very throats of Hindu, Sikh, and Muslim farmers by trying to take their livelihood.
You will not succeed in your sinister ways.
The two-sided sword of the Khalsa is at any moments notice. Tyaar bar tyaar.
Wherever our blood is spilled, the tree of Sikhi uproots from there.
If your intentions for the farmers are pure and
you wish to help them, this is not the way.
Halemi Raj, Sikh Raj, was not this way.
If the laws are not repealed. Your fate is no
different to what the Khalsa did to Sirhind.
Waheguru Ji Ka Khalsa, Waheguru Ji Ki Fateh
Khalsa Cyber Fauj
Sarbloh is a standard malware, compiled using MAAS (Malware-as-a-service) tools available on the dark web. Even the mutant used is part of the “standard” code available on stackoverflow.com.
Public key is embedded within the code, with the same being:
—–BEGIN PUBLIC KEY—–MIIBITANBgkqhkiG9w0BAQEFAAOCAQ4AMIIBCQKCAQBvDXdHEUBJM6TYrpMkTxpk1nDRWw0HwIQjqTxVIhGTKZOOG15TUYDhGzY6i20UarvCE7r+65raJiOULaLNOK3GmhbfXdyvrm4uYFrKbepkChNm0XNrBkTxiHD0v4nylrYX02oe+BSf3deaLMyXa1m0FEe7miw/OCNirJ14BjvqdH/Yzka+5bTlpaELBbvja3Cm/2hPUTRDyvAtpv5hjuLb/iedu9W8IWjEX6b96/3NHmjryRnJtVQdWvpycQ8+ZPsiRkWW2wp8UBo35PPUq4ggicWGWvCjUBKxxlWg+Bw+sWWO5UsuCI288YA/xVwKpI16XdgLIiOHJd2PI6B0FHThAgMBAAE=
—–END PUBLIC KEY—–
It appears to be named after a book of scriptures related to Sikhism called the “Sarbloh Granth”.
Sarbloh, or wrought iron, is the metal used in the bowl used by Guru Gobind Singh Ji to make ‘amrit’ (Elixir) during the Khalsa initiation ceremony. Khanda, the double-edged knife or sword, is made of Sarbloh. To date, Amrit Sanchaars are conducted using a bowl and ‘Khanda’ made of ‘Sarbloh’.
Unlike other ransomware, Sarbloh does not remove shadow volume copies, so it may be possible to recover files through shadow volumes.
Hence our internal experts’ advise you to observe the following precautions to prevent your PC / laptop from getting infected with the Sarbloh ransomware –
- Given, the primary source of the malware is emails, you have to be extra cautious while handling your emails.
- Install reliable anti-virus software, from eScan’s family of cybersecurity solutions. The eScan Bot Toolkit has detections for Sarbloh Ransomware from 3rd March 2021 (first samples observed and reported). It is detected as GenericKD.
- In case you don’t recognize the sender of an email, don’t ever download attachments from such emails.
- Don’t make any payment or provide your OTP or any password to anyone for such information on email. Just mark such emails as spam. You won’t get them in your inbox anymore.
To read more, please check eScan Blog