While investigating an early attack in 2021, the French national cyber-security agency discovered a new variant of the Ryuk ransomware. This variant has worm-like capabilities that allow it to spread to other devices on victims’ local networks.
According to the cybersecurity agency, the malware propagates itself, machine to machine, through the use of scheduled tasks within the Windows domain.
Once launched the malware spreads itself on every reachable machine on which Windows RPC access is possible.
The new Ryuk variant lists all the IP addresses in the local ARP cache and sends what looks like Wake-on-LAN (WOL) packets to each of the discovered devices, to propagate itself over the network. All the sharing resources found for each device are then mounted so that the ransomware can encrypt its contents.
Ryuk’s ability to mount and encrypt drives of remote computers was previously noticed by researchers last year.
The ability to copy itself to other Windows devices on the victims’ local networks, makes this variant of Ryuk very different from its predecessors. The variant can also execute itself remotely using scheduled tasks created on each subsequently compromised network host with the help of the legitimate schtasks.exe Windows tool.
The Agence Nationale de la Sécurité des Systèmes d’Information (ANSSI) after analyzing the recent variant confirmed of its self-replication capabilities and its method of propagation.
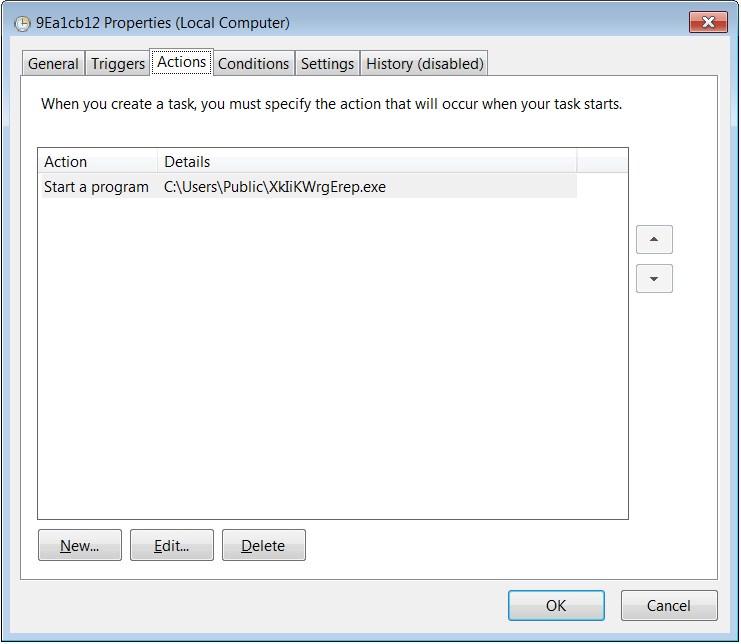
Even though the ransomware doesn’t include a mechanism that would prevent it from re-encrypting devices, ANSSI says that the new variant can still be blocked from infecting other hosts on the network by changing the password of the privileged domain account it uses for propagation to other hosts.
According to the ANSSI, one way of tackling the problem could be to change the password or disable the user account and then proceed to a double KRBTGT domain password change. Many disturbances would be induced by this on the domain – and would most likely require many reboots but would also immediately contain the propagation. Other propagation containment approaches, especially through the targeting of the malware execution environment could also be careful.
First discovered in the year 2018, The Ransomware-as-a-service (RaaS) group has a long list of victims against its name. Such groups are known for running private affiliate programs where affiliates can submit applications and resumes to apply for membership.
With its payloads being discovered in roughly one in three ransomware attacks throughout the last year, Ryuk is at the top of the RaaS rankings. As a part of its multi-stage attacks, the group delivers payloads using Emotet, BazarLoader, or TrickBot infection vectors for a quick way into their targets’ networks.
Starting from the November of 2020, Ryuk affiliates have been behind large-scale attacks on US healthcare systems. Having collected $34 million from one victim, it is evident that they demand a large sum of money.
After following the money trail from Ryuk ransomware victims, security researchers believe that the RaaS operation made at least $150 million.
On average, roughly 20 companies were hit every week by Ryuk Affiliates during the third quarter of 2020.
To read more, please check eScan Blog







