With technology evolving at a rapid pace the variations to threats and the advent of new trojan threats finding newer methods to infiltrate and hack their potential victims have grown at a rapid pace. One such trojan threat was detected in the year that passed by. A new malware called the Joker was discovered hiding behind the advertisement framework of various compromised applications. This malware signs up users for premium subscriptions and in the process siphon offs the user’s valuable data. The rise of the joker trojan was such that 24 apps from the play store including a few with over 100,000 downloads were found to be infected.
What is the Modus Operandi?
- A second stage component is downloaded by the Joker Trojan to the infected device. This component harvests sensitive data including texts and contacts by simulating automated interactions on advertisement sites.
- Since this Trojan has access to text messages, it extracts codes from authorization messages to subscribe to users for premium services.
All the harvested data is then sent to the command and control server in an encrypted format.
Areas of Infection:
Many of the Joker-infected applications have found their origins in the European and Asian countries. It is also been specifically noted that these applications have a further additional check to make sure that the payload does not execute if the application is downloaded and installed from locations like the US and Canada.
In a list included by a security firm, the following countries are mentioned.
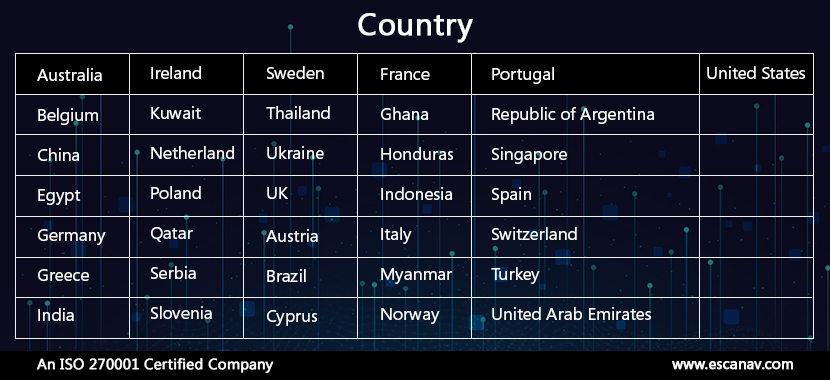
The country code is included in the compromised applications and the country code of the potential victim’s SIM card is compared with this list. If the number matches the list then the joker proceeds to the second stage and downloads the malicious component.
Even though Google is in the process of weeding out the infected applications from the play store, our experts suggest android users grant permission only after verifying the apps they download.
To read more, please check eScan Blog







