The REvil ransomware group is back in full force, digitally assaulting new victims and leaking stolen data to a data leak site.
The REvil ransomware operation, dubbed Sodinokibi, has been attacking organizations around the world since 2019, demanding million-dollar ransoms in exchange for a decryption key and preventing the leakage of stolen files.
The gang has been involved in a number of high-profile attacks, including those against JBS, Coop, Travelex, GSMLaw, Kenneth Cole, Grupo Fleury, and others.
The Disappearing Act
After their biggest heist yet, REvil shut down their infrastructure and vanished, encrypting 60 managed service providers and over 1,500 organizations exploiting a zero-day vulnerability in the Kaseya VSA remote management platform on July 2nd.
REvil then sought $50 million for a universal decryptor for all Kaseya victims, $5 million for a decryptor for a managed service provider, and $44,999 for individual file encryption extensions for affected organizations.
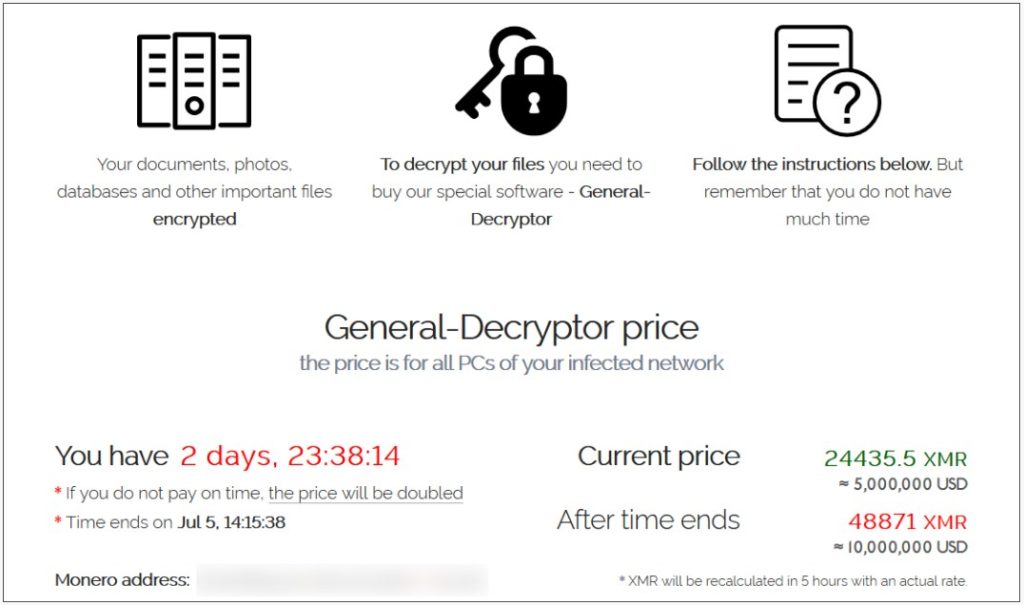
<REvil ransom demand for an encrypted MSP>
This attack had such far-reaching ramifications around the world that it drew the full focus of international law enforcement agencies towards the group.
The REvil gang abruptly ceased operations on July 13th, 2021, presumably due to pressure and fears of being captured, leaving many victims in the dark and unable to decrypt their files.
The last we heard of REvil, Kaseya had received a universal decryptor that victims could use for free to decrypt their files. Kaseya indicated that the decryptor came from a “trusted third party,” however it is unclear how they obtained it.
REvil returns with new attacks
Researchers and law enforcement suspected REvil would rebrand as a new ransomware operation after being shut down.
However, the REvil ransomware group resurfaced this week under the same moniker, much to everyone’s astonishment.
The Tor payment/negotiation and data leak sites abruptly went back on and became accessible on September 7th, over two months after their disappearance. It was feasible to log in to the Tor payment site and negotiate with the ransomware group again a day later.
There was no evidence of additional attacks until September 9th, when someone uploaded a new REvil ransomware sample to VirusTotal, which had been produced on September 4th.
The ransomware gang has published screenshots of stolen data for a new victim on its data leak site today, providing more proof of their continued operations.
Representatives of the new REvil are revealed
REvil’s public face in the past was a threat actor known as ‘Unknown’ or ‘UNKN,’ who frequented hacker forums to recruit new affiliates and announce ransomware-related news.
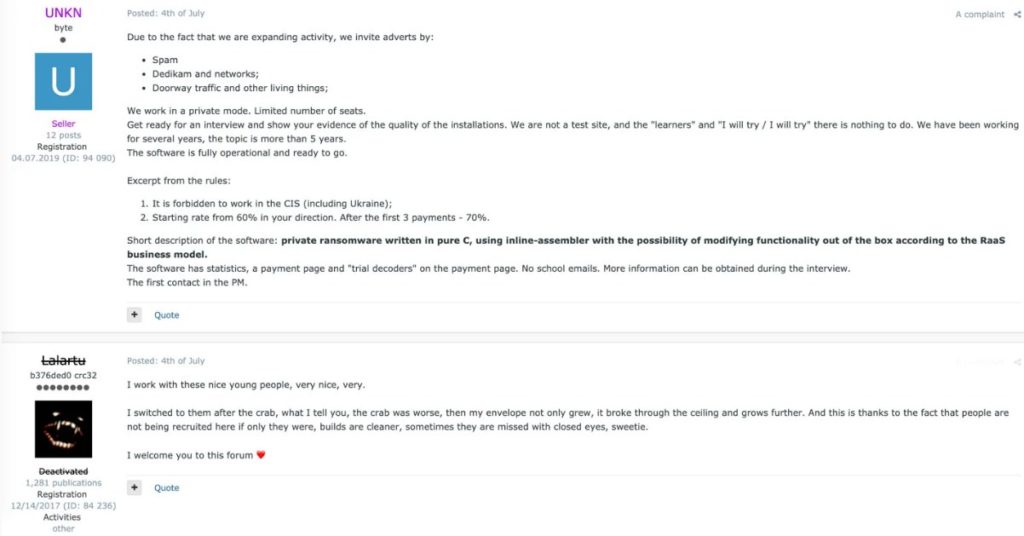
Following the restart of the ransomware operation on September 9th, a new representative merely identified as ‘REvil’ began posting on hacker sites, saying that the gang had temporarily halted down after the operator called as Unknown was jailed and systems were infiltrated.
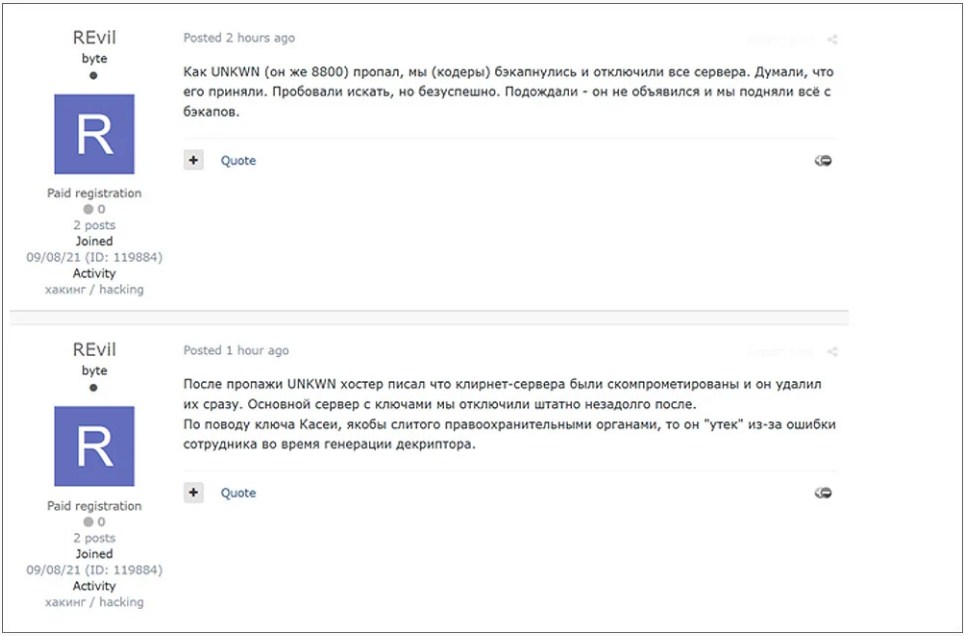
The following is a translation of the posts:
We (the coders) backed up and shut off all the servers as Unknown (aka 8800) vanished. I was under the impression that he had been arrested. We looked for a while but couldn’t find anything. We waited for him to arrive, but he did not, so we restored everything from backups.
After UNKWN vanished, the hoster notified us that the Clearnet servers had been hacked and that they had been erased immediately. Following that, we immediately shut down the primary server with the keys.
The Kaseya decryptor, which was supposedly disclosed by law enforcement, was actually leaked during the production of the decryptor by one of our operators. – REvil
According to these reports, law enforcement received Kaseya’s universal decryptor after gaining access to several of REvil’s servers.
A conversation between a security researcher and REvil, purportedly between the two, paints a different picture, with the REvil operator stating they just took a break.
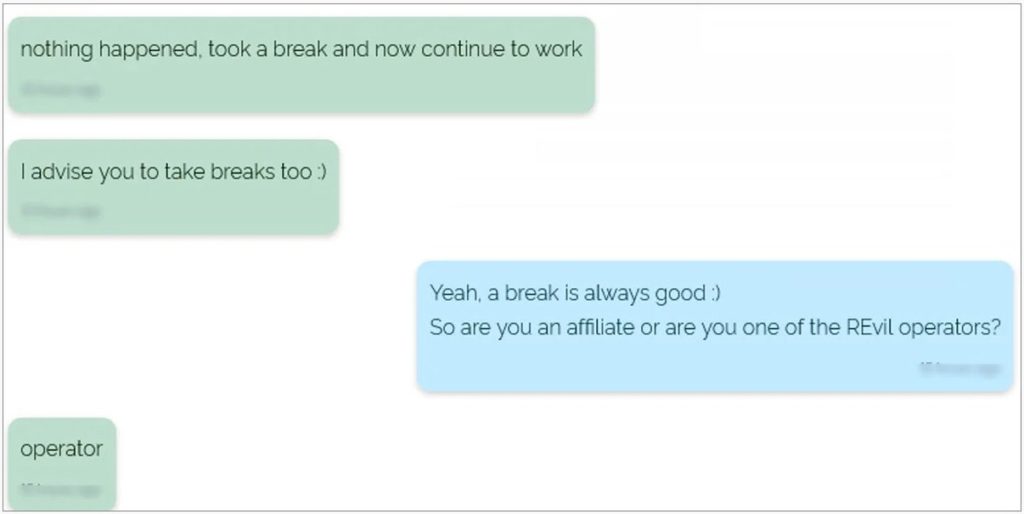
While we may never know the true cause for REvil’s disappearance or how Kaseya obtained the decryption key, the most essential thing to know is that REvil has returned to hunting corporations all over the world.
All network admins and security professionals must become familiar with their strategies and approaches due to their experienced affiliates and ability to undertake sophisticated attacks.
To read more, please check eScan Blog







