Node.js has published fixes for a high severity vulnerability that might be exploited by attackers to corrupt the process and cause unexpected behavior, such as application crashes and possibly remote code execution (RCE).
CVE-2021-22930 is a use-after-free issue that affects how HTTP2 streams are handled in the language.
Node.js releases an instant remedy for the issue in its code.
CVE-2021-22930, a high-severity use-after-free vulnerability, was patched by Node.js recently.
It’s possible for a software to access a resource after it’s been freed, leading to a use-after-free vulnerability.
There is a risk of data corruption, unanticipated behavior, program crashes, or even remote code execution (RCE) in some instances.
The changes were backported to Node.js versions 12.22.4 (LTS) and 14.17.4. (LTS).
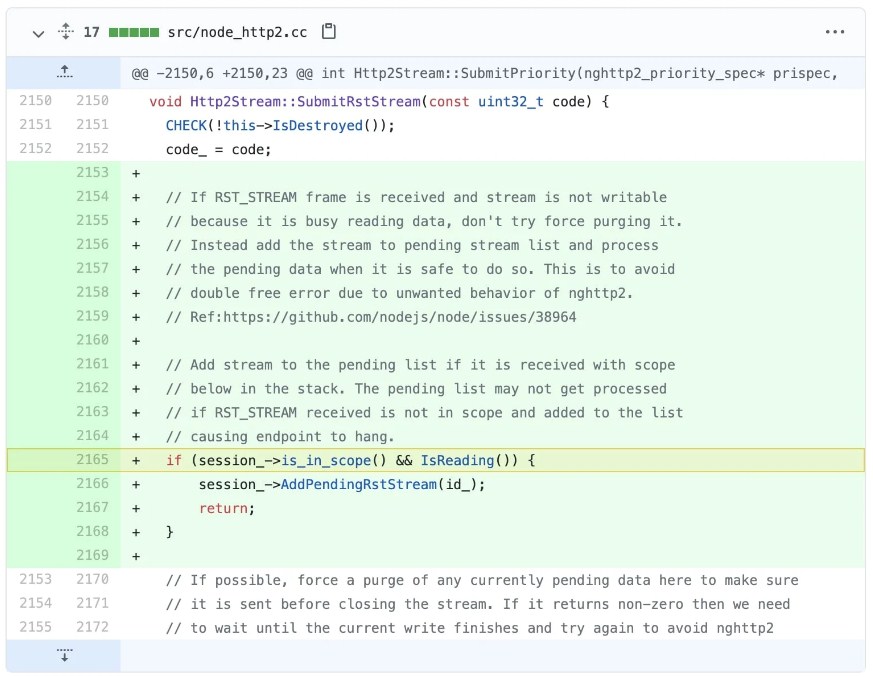
Node.js has been patched with the following fix, which has been applied to several branches –
A github contributor from Israel, named Eran Levin has been credited with the discovery of this vulnerability.
The fact that discussions around a high severity vulnerability were previously public explains the quick delivery of an update:
A Red Hat principal software engineer and NodeJS Technical Steering Committee (TSC) member said, “We normally like to give advance notice and provide releases in which the only changes are security fixes, but since this vulnerability was already public, we felt it was more important to get this fix out fast in releases that were already planned.”
When HTTP connections are terminated, a bug is triggered.
RST STREAM frames with no error code or cancel code were processed by Node.js, which then exploited the flaw.
Applications using the HTTP/2 protocol send the RST STREAM frame when they want to discontinue a connection.
In a client-server architecture, for example, a client program would send an RST STREAM frame to the server to terminate the connection.
When the server receives a frame, it will stop replying to the client, resulting in the termination of the connection. It was then possible to discard any “DATA” frames that the server was planning on sending to the client.
Node.js versions that are vulnerable will attempt to “force delete” any data they receive when they receive an RST STREAM frame with a “cancel” code (nghttp2 cancel) on the server.
This was followed by an automatic callback that attempted to free up the memory again after it had already been released in step 1.
A double-free error might cause the application to crash, or cause abnormal behavior.
As opposed to a vulnerability, this error—previously considered a “bug”—was reported on June 8th, 2021 in a public thread.
As a result of the bug being 100% reproducible on the researcher’s PC, application crashes occurred 100% of the time.
The researcher and Node.js contributors engaged in a lengthy conversation that lasted more than a month.
RST STREAM frames with no error code and cancels error codes appear to be the source of the problem.
According to GitHub user kumarak, “The node tries to force process it and cleanse any existing data for the stream, leading nghttp2 to shut the previously destroyed stream and produce the double-free error.”
RST STREAM frames are instead queued up and processed once it is safe. Any double-free or use-after-free mistakes would be prevented by this method.
Update to version 16.6.0 of Node.js or a fixed backported version for Node.js users
To read more, please check eScan Blog







