With the tax season coming closer and threat actors are gearing up to take advantage of this season. One of these happens to be the Mount Locker Ransomware operators who will be targeting TurboTax returns for encryption.
Relatively new ransomware, Mount Locker began infecting victims in July 2020. Mount Locker gang compromises networks, harvests unencrypted files to be used for blackmail, and then encrypts the devices on the network, just like other human-operated ransomware gangs.
Stolen data and the encrypted files are then used in a double-extortion scheme where the ransom is elicited from the victims with a threat that if they fail to pay, their data would be leaked over the internet.
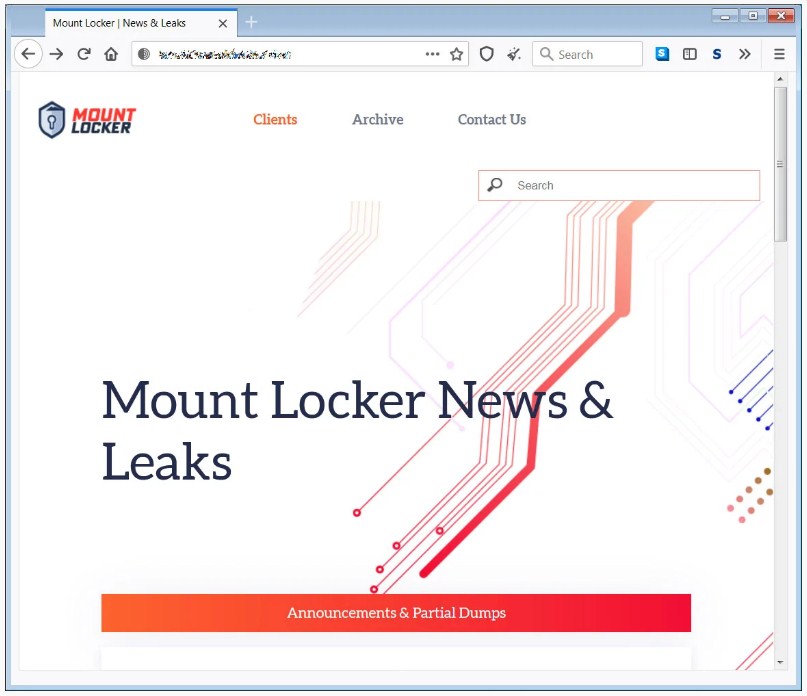
Like every tax season, people are gathering their tax information and inputting it into TurboTax to prepare for the tax deadline.
According to the newer version of the ransomware that was analyzed by researchers, Mount Locker is preparing to target users filing their tax information by the TurboTax tax software.
Mount Locker only encrypts files that have certain file extensions, when it is encrypting the computer. With its latest updated version, the ransomware developers are now targeting the .tax, .tax2009, .tax2013, and .tax2014 file extensions associated with the TurboTax tax preparation software.
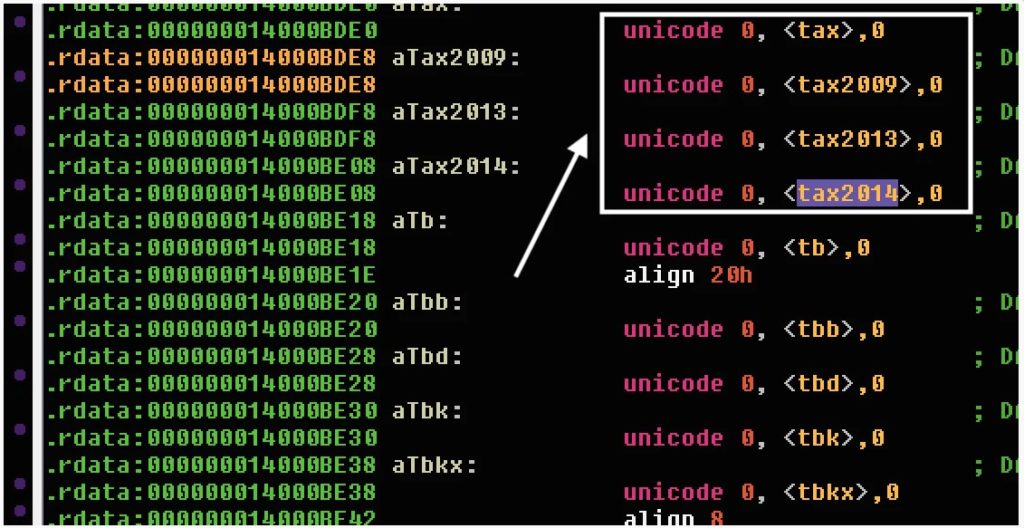
While Mount Locker is oddly targeting file extensions for specific tax year’s researchers believe that the ‘tax’ targeting would match all extensions that contain the string.
Our internal experts suggest for being safe from Mount Locker and other ransomware, be sure to make backups of your TurboTax files and other essential documents on detachable media after you make any changes.
Backing up highly important files on a removable storage device like a USB drive every night and then unplugging it will guarantee the safety of your files even if you suffer a ransomware attack.
To read more, please check eScan Blog