Cybercriminals are gradually recognizing that the REvil ransomware operators may have been hijacking ransom negotiations in order to avoid paying affiliates.
The operators left their partners out of the arrangement and took the whole ransom by employing a cryptographic scheme that allowed them to decode any systems encrypted by REvil malware.
Conversations about this approach began a while ago on underground forums, in posts from gang collaborators, and security researchers along with malware makers have recently confirmed it.
REvil ransomware, also known as Sodinokibi, first appeared in the first half of 2019 and quickly gained a reputation as the GandCrab ransomware-as-a-service (RaaS) operation’s successor.
A developer builds the ransomware malware and sets up the infrastructure, then affiliates are recruited to penetrate and encrypt victims in the RaaS cybercriminal business model. The proceedings are split between the two parties, with affiliates receiving a bigger portion of the proceeds (typically 70-80 percent).
The REvil gang, which was founded by veterans of underground forums, built a highly profitable private enterprise that only admitted experienced network hackers.
REvil’s moniker is obliterated.
If the REvil organization began as an “honest” cybercrime business, it quickly shifted its focus to defrauding affiliates of the promised 70% share of a ransom from paying victims.
Various players on underground forums reported that the RaaS operators were taking over talks with victims in covert chats, unbeknownst to affiliates, since at least 2020, according to the head of research at a loss prevention organization.
After the abrupt shutdown of DarkSide ransomware and Avaddon’s exit by releasing the decryption keys for their victims, the rumor gained traction.
Individuals who played a part in the REvil ransomware assaults were discussed, including partners who supplied network access, penetration-testing services, VPN specialists, and suspected affiliates.
REvil would take over when the conversations hit a stalemate by appearing as the victim and exiting the negotiations without paying the ransom, he stated further.
The gang would keep talking to the victim until the full ransom was paid, and the affiliate would be completely unaware.
Recently, an underground malware reverse engineer uncovered evidence of REvil’s double-dipping methods, giving credence to these assertions. In the REvil samples that RaaS operators supplied affiliates to deploy on victim networks, they mention a “cryptobackdoor.”
The author’s admission follows the introduction of a universal REvil decryption tool that works for all victims encrypted up until July 13, 2021.
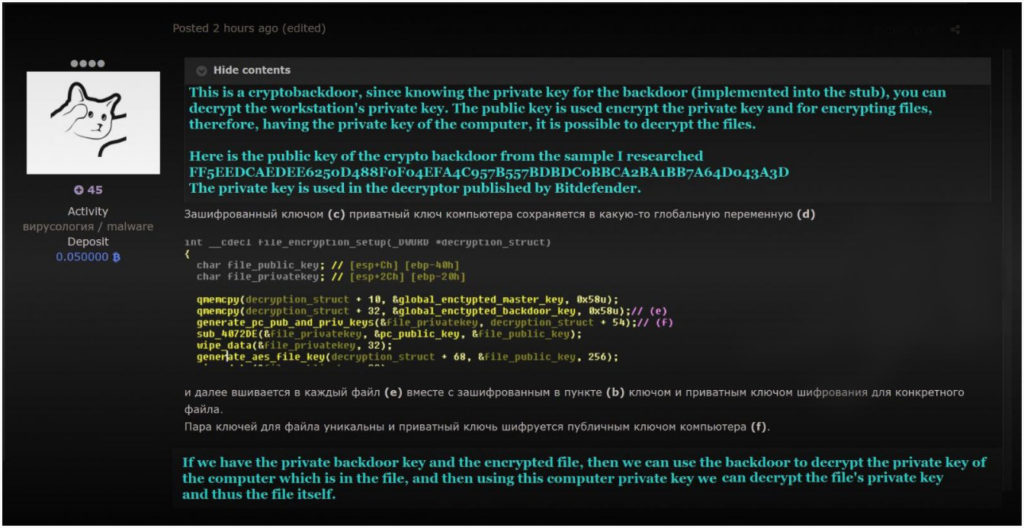
Public key in the image above:
FF5EEDCAEDEE6250D488F0F04EFA4C957B557BDBDC0BBCA2BA1BB7A64D043A3D
The author of the preceding post is implying that affiliates were not the only ones who were able to unlock the systems infected with the REvil ransomware strain.
REvil operators had access to a master key that could be used to decrypt files.
A researcher revealed the trick recently
In early July, a researcher known as ransomware slayer provided a detailed analysis of REvil’s encryption technique.
GandCrab’s successor uses four sets of public-private keys to perform encryption and decryption functions in their malware:
- All REvil samples have the public part hardcoded in an operator/master pair.
- A campaign pair, the public part of which is saved as a PK value in the malware’s configuration file.
- A pair is created when the machine is encrypted, with the private component encrypted using both the public master and campaign keys.
- For each encrypted file, a key pair is generated.
“The private file key and public system key are then utilized as inputs for ECDH using Curve25519 in order to generate the Salsa20 key (also known as a shared secret) that is used to actually encrypt the file content,” the researcher continues.
Because it is the sole key necessary to decrypt individual files, the system’s private key is required to unlock a machine. It may be recovered using either the master private key, which is only available to REvil operators, or the affiliate campaign key.
The master private key, according to the researcher, is REvil’s insurance against rogue affiliates, as it allows them to decode any victim. This is also what the cybersecurity firm used for its REvil decryption tool, which is most likely how Kaseya victims were able to recover their files for free.
The ransomware threat actor needs a blob of data from the ransom message to access the REvil payment interface. This string of seemingly incomprehensible characters contains information on the machine, the campaign, the malware version utilized, and the system private key.
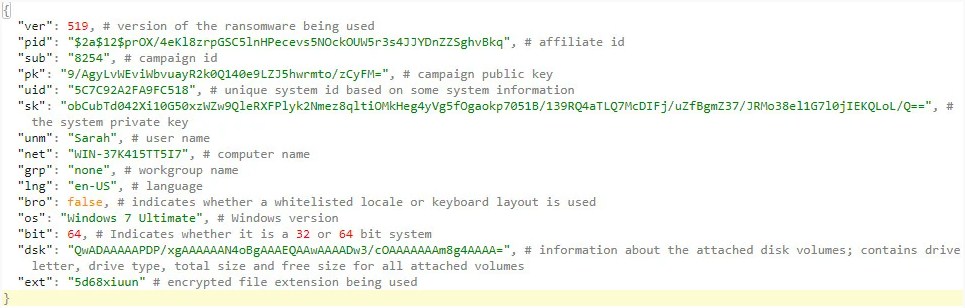
The DarkSide ransomware group was said to operate in a similar manner.
The actor was clear about this approach after rebranding as BlackMatter, letting everyone know that they reserved the right to take over the discussions at any time, without explanation.
According to reverse engineer Vitali Kremez, the newer REvil samples, which appeared after the gang resumed operations, no longer contain the master key that allows the decryption of any system infected with REvil ransomware.
To read more, please check eScan Blog







