As part of its malicious ransomware campaign, the RansomEXX gang has targeted Taiwanese motherboard maker Gigabyte.
However, Gigabyte also produces other computer components and hardware, such as laptops and displays.
A cyberattack on the corporation occurred late Tuesday night and into Wednesday, forcing it to shut down its systems in Taiwan. As well as the company’s help site and Taiwanese website, several other websites were also affected.
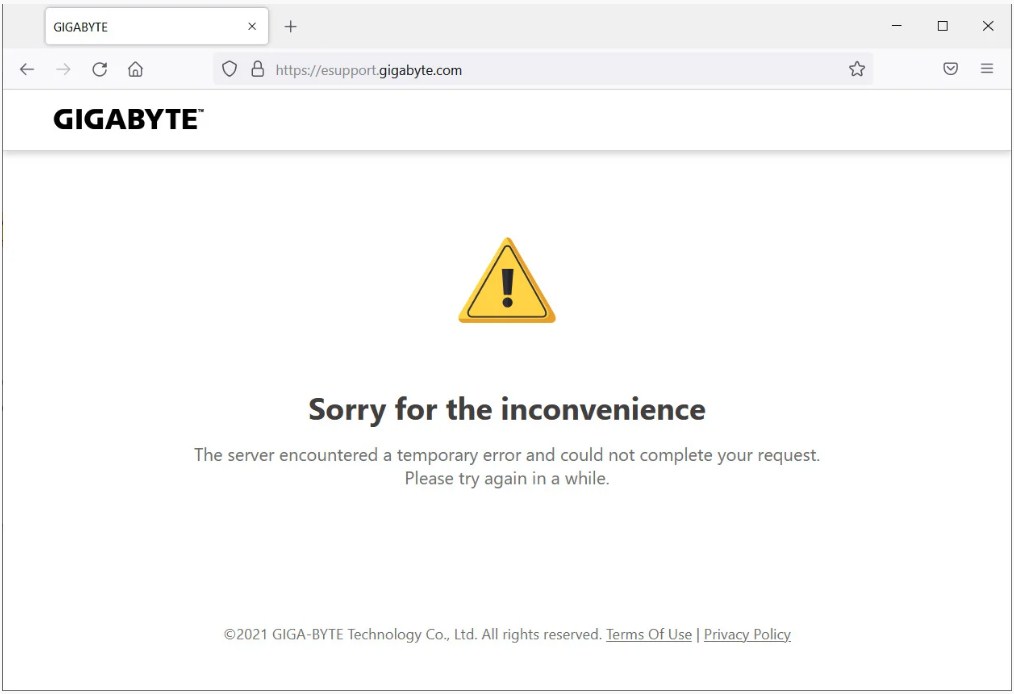
Due to the ransomware attack, customers have also reported difficulty accessing support documentation or receiving updated information about RMAs.
An attack on Gigabyte’s servers was confirmed, according to the Chinese news outlet United Daily News.
Once their IT systems were taken down, they notified law enforcement of the suspicious activity.
As an online publication has learned, the attack was carried out by the RansomEXX ransomware organization.
On each encrypted device, the RansomEXX operators will leave a note demanding payment.
There is a link on these ransom notes that takes the victim to a non-public web page where he or she can test out how to decrypt one file and provide an email address for negotiations.
RansomEXX leak website for Gigabytes Technologies, which is not publicly accessible, claims to have stolen 112GB of data during the attack, according to researchers.
This same link to the private leak website appears in a ransom note from the threat actors, which begins, “Hello, Gigabyte (gigbyte.com)!”
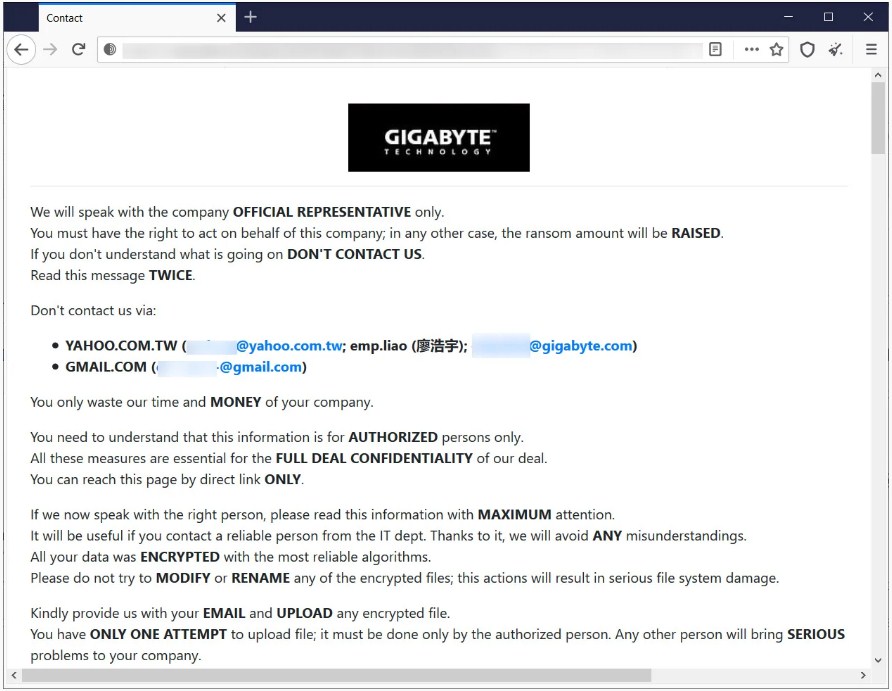
An internal Gigabyte network, as well as the American Megatrends Git Repository, was allegedly also breached.
We have downloaded 112
GB (120,971,743,713 bytes) of your files and we are ready to PUBLISH it.
Many of them are under NDA (Intel, AMD, American Megatrends).
Leak sources: newautobom.gigabyte.intra, git.ami.com.tw and some others.
Aside from four stolen NDA agreements, the threat actors posted screenshots of them on social media.
In addition to a debug paper from American Megatrends, an Intel “potential issues” document, an “Ice Lake D stack upgrade plan,” and an AMD revision guide is among the private materials.
RansomEXX
After becoming more active in June 2020, the RansomEXX ransomware operation changed its name to RansomEXX from Defray.
It will infect a network using Remote Desktop Protocol (RDP), exploits, or stolen credentials, just like other ransomware operations have in the past.
The attackers will collect more credentials when the Windows domain controller is slowly taken over once they have gained network access. Ransomware will take data from unencrypted devices used as leverage in ransom extortion during this lateral propagation.
There is a Linux encryptor for virtual machines running VMware ESXi servers that RansomEXX has produced as well.
Recent attacks on Italy’s Lazio area and Ecuador’s Corporación Nacional de Telecomunicaciones have increased RansomEXX’s activity in the past month (CNT).
Brazilian government networks, the Texas Department of Transportation (TxDOT), Konica Minolta, IPG Photonics, and Tyler Technologies have all been targeted by the ransomware gang.
To read more, please check eScan Blog