A fake Adobe Flash Player updater that installs other unwanted programs on unsuspecting users’ computers is being promoted by threat actors through the use of Google Alerts.
Fake stories are created by the threat actors with titles containing popular keywords that Google Search then indexes. Google Alerts will alert people who are following those keywords once they are indexed.
The visitors are redirected to the threat actor’s malicious site when they visit the fake stories using a Google redirect link, as shown below.
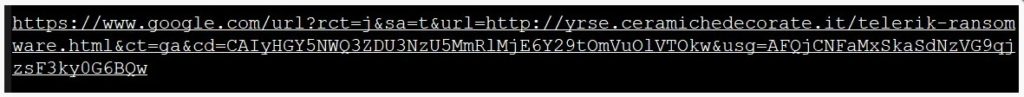
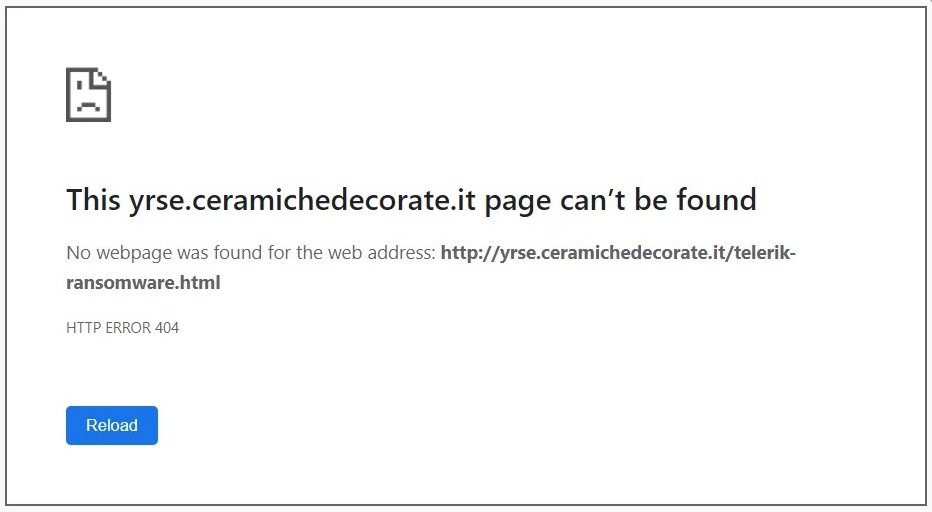
However, if the URL of the fake stories is visited directly, then the website will state that the page does not exist.
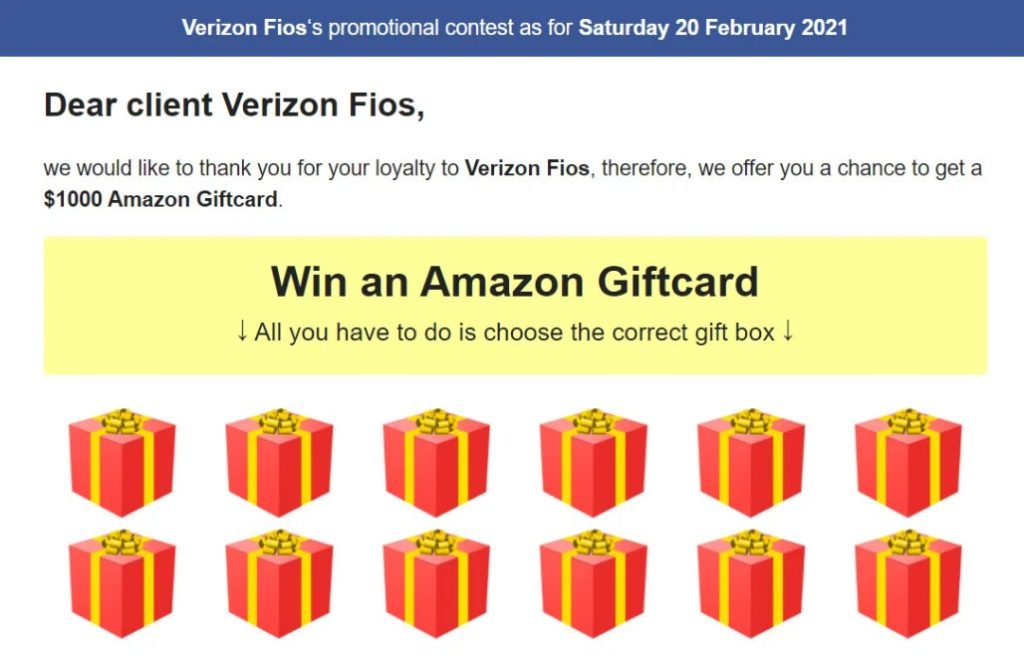
Researchers have been monitoring fake stories being indexed by Google and pushed out by Google Alerts. Just like the fake amazon giveaway scam below, these stories have been redirecting users to web pages pushing browser notification spam, unwanted extensions, or fake giveaways.
Threat Actors Launch A New Campaign
Recently researchers observed that the fake news stories are redirecting the users to a new campaign that states your Flash Player is outdated and then prompts you to install an updater.
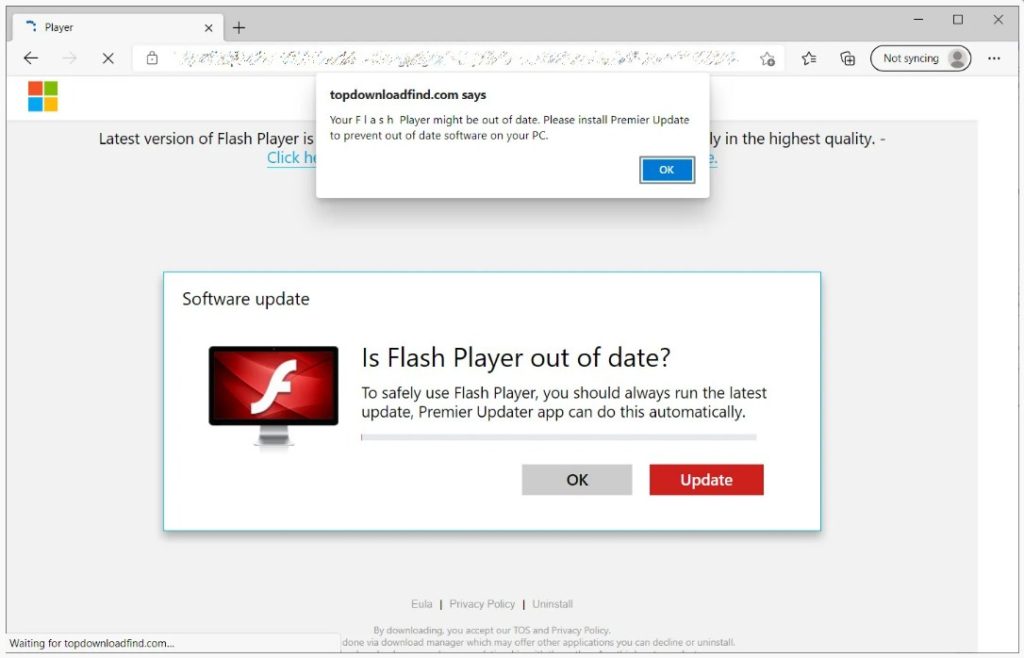
Many users don’t realize that Adobe Flash Player is no longer supported by any browsers and they end up clicking on the ‘Update’ button thinking they are installing the latest update.
A potentially unwanted program called ‘One Updater’ is installed after a setup.msi file is downloaded once the unsuspecting user clicks on the update button.
Over time, this unwanted program will display updates that should be installed and offer potentially unwanted programs.
From the time it is being observed by researchers One Updater hasn’t pushed anything that is malicious in nature. However, similar software in the past has installed password-stealing Trojans and cryptocurrency miners.
Our Internal experts suggest simply closing the browser if you are redirected to a website, whether via Google Alerts, Google Search, or any other means and are prompted to install an extension or program update.
Installing such programs usually lead to malicious activities that only benefits the threat actors.
To read more, please check eScan Blog







