MirrorBlast is a novel phishing effort that uses weaponized Excel documents that are particularly difficult to detect in order to infiltrate financial sector businesses.
MirrorBlast’s most prominent feature is the campaign’s malicious Excel documents’ low detection rates by the security software, placing organizations who rely primarily on detection technologies in danger.
Zero detections in a featherlight macro
The authors of these malicious papers have gone to great lengths to disguise harmful code, resulting in zero detection on VirusTotal.
These optimized papers, however, have downsides that the actors appear to be ready to accept as trade-offs. The macro code, in particular, can only be run on a 32-bit version of Office.
If the victim is duped into opening the infected document and clicking the “enable content” button in Microsoft Office, the macro runs a JScript script that downloads and installs an MSI package.”
Prior to that, the macro does a basic anti-sandboxing check to see if the computer name matches the user domain and if the username matches ‘admin’ or ‘administrator.’
According to experts who examined various samples of the fallen MSI package, it comes in two flavors: REBOL and KiXtart.
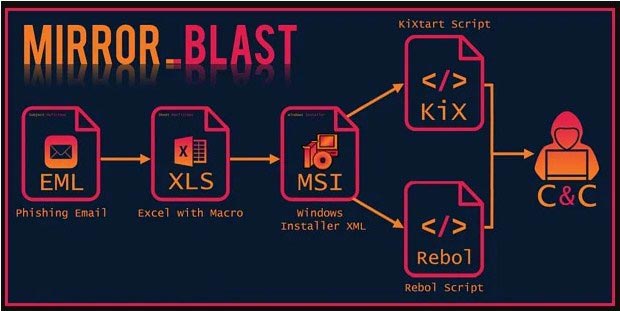
The base64 encoded REBOL variation begins by exfiltrating information such as the login, OS version, and architecture.
Following that, it waits for a C2 command to launch a PowerShell operation that will retrieve the second stage. However, the researchers were unable to retrieve that stage, therefore its activities are unknown.
The KiXtart payload is encrypted as well, and it attempts to exfiltrate basic machine information to the C2, such as the domain, computer name, user name, and process list.
A threat actor who is highly motivated
The campaign’s perpetrators appear to be ‘TA505,’ an active Russian threat group with a lengthy history of ingenuity in the way it incorporates Excel documents into malspam campaigns.
Researchers were able to connect the perpetrators to the MirrorBlast campaign due to infection chain similarities with previous operations, the usage of OneDrive, differences in domain name practices, and the presence of an MD5 checksum discrepancy pointing to a 2020 attack performed by TA505.
TA505 is a highly sophisticated threat actor that has been linked to a variety of destructive activities throughout the years.
<>
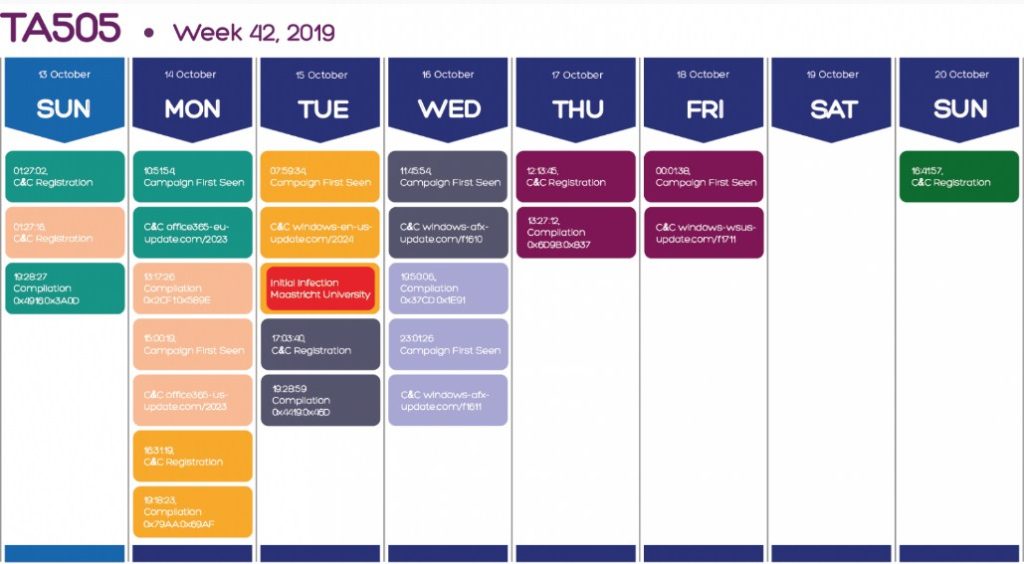
An examination of the actor’s work schedule reveals a well-organized and well-structured gang that employs zero-day vulnerabilities and a wide range of malware strains in its attacks. This involves using Clop ransomware in double-extortion assaults.
TA505 is also linked to a slew of attacks that steal data from enterprises by exploiting a zero-day vulnerability in Accellion FTA secure file sharing devices.
The threat actors then sought to extort the companies by seeking $10 million in ransom to keep the data from being publicly leaked on their Clop data leak site.
As a result, the IT teams at the financial institutions targeted by the MirrorBlast campaign cannot afford to let down their guard even for a second.
To read more, please check eScan Blog






