Every business should implement an endpoint security program, no matter how small or large. From traditional antivirus software to comprehensive protection against sophisticated malware and evolving zero-day threats, it has evolved into a comprehensive security solution. So what exactly is it, how does it work, and what should businesses know about it?
What is endpoint security?
A cybersecurity threat can take the form of malware, viruses, and other cybercriminals targeting endpoints, such as desktops, laptops, and mobile devices. Endpoints can be exploited by cybercriminals as entry points into an organization’s networks. Using endpoint security, these entry points can be protected from malicious attacks.
Why is endpoint security important?
Business endpoints have increased in recent years. Globally, remote working has become increasingly popular since the Covid-19 pandemic. Enterprise networks now have more endpoints than ever, as more employees work from home or connect to public Wi-Fi. There are a number of potential entry points for attacks on every endpoint.
Cyberattacks can affect businesses of all sizes. It is increasingly difficult to protect against attacks that enter through endpoints, such as laptops and mobile devices. It is possible for these devices to be hacked, resulting in data breaches. Endpoint devices are estimated to be the cause of 70% of successful data breaches.
Besides reputational damage, data breaches cost companies money. According to a report by Ponemon, commissioned by IBM, the average global cost of a data breach is $3.86 million. Companies place a high value on their data, and losing that data, or losing access to it, can have devastating effects on their business.
In addition to an increase in the number of endpoints — driven by remote working — businesses also have to deal with an increase in the types of endpoints produced as a result of the Internet of Things.
Cyber threats must be protected and businesses must ensure visibility into them. However, many small and mid-sized businesses lack the resources to continuously monitor network security and customer information and often only consider protecting their networks after a breach has already occurred. Businesses can focus on their network and infrastructure without protecting some of the most vulnerable elements – endpoint devices. Security is a continuous challenge due to the risks posed by endpoints and their sensitive data. As endpoints evolve, businesses – small, medium, and large – become targets for cyberattacks. The importance of understanding endpoint security and how it works lies in the fact that it’s a necessity.
How does endpoint security work?
Organizations use endpoint protection, endpoint security, and endpoint protection platforms interchangeably to refer to centrally managed security solutions. In endpoint security, files, processes, and systems are examined for suspicious or malicious activity.
Endpoint protection platforms – EPPs – can protect organizations’ devices from malicious actors’ attempts to infiltrate their systems using malware. With the help of an EPP, it can be possible to flag suspicious behavior and prevent breaches before they occur using other detection and monitoring tools.
Organizations are able to connect their networks to the centralized management console for endpoint protection. Administrators are able to monitor, investigate, and respond to potential cyber threats through the console. An on-premises, cloud, or hybrid approach can be used to accomplish this:
On-location: An on-premises solution involves hosting the management console in a local data center that acts as a hub. Security will be provided by an agent connecting to the endpoints. Because administrators can only manage endpoints within their perimeter, this approach is seen as a legacy model with drawbacks – including creating security silos.
Cloud: A centralized management console in the cloud provides administrators with the ability to monitor and manage endpoints remotely. By leveraging the advantages of the cloud, cloud solutions ensure security behind the traditional perimeter – eliminating silos and improving administrator access.
Hybrid: Hybrid approaches combine on-premises and cloud solutions. The pandemic has led to an increase in remote working since this approach has gained popularity. Cloud-enabled elements of legacy architecture are being adapted for the cloud, allowing organizations to gain some cloud capabilities as a result.
Cloud-based EPPs that store threat information free endpoints from the bloat associated with local storage and require less maintenance. Cloud-based approaches are also faster and more scalable. Regulatory requirements may require large organizations to have on-premises security. Cloud-based solutions are probably more suitable for small and midsized businesses.
These features are usually included in endpoint security software:
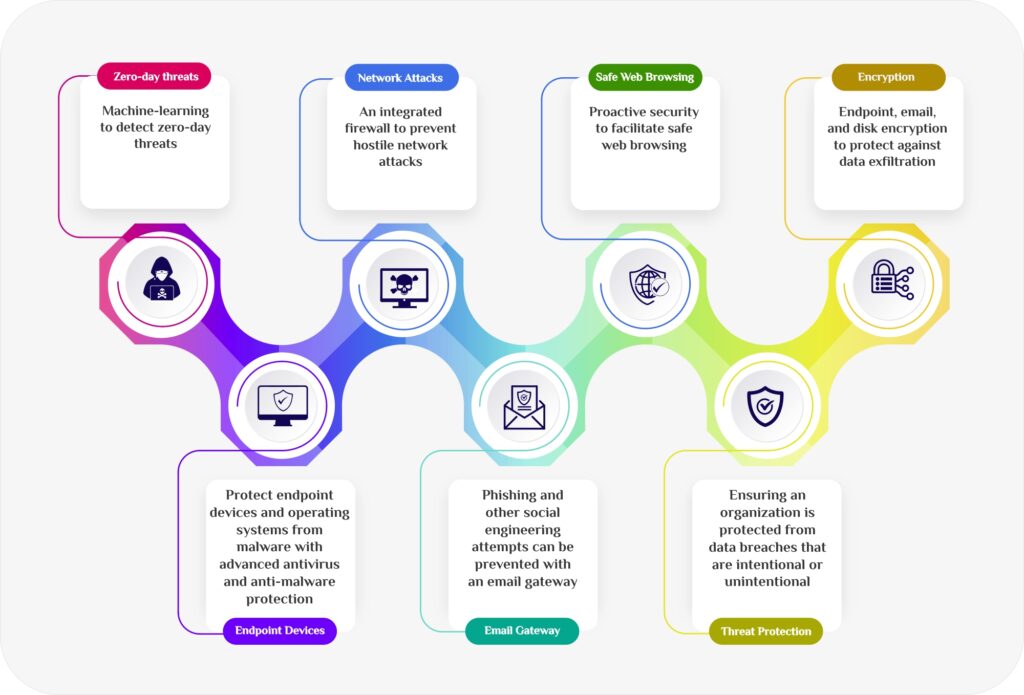
- Machine-learning to detect zero-day threats
- A built-in firewall to protect against hostile network attacks
- Phishing and other social engineering attempts can be prevented with an email gateway
- Ensuring an organization is protected from data breaches that are intentional or unintentional.
- Protect endpoint devices and operating systems from malware with advanced antivirus and anti-malware protection
- Proactive security to facilitate safe web browsing
- Protect against data exfiltration with endpoint, email, and disc encryption.
As a result, endpoint security provides administrators with a centralized platform that allows them to improve visibility and simplify operations as well as quickly identify and isolate threats. Endpoint security also includes the acronyms EPP and EDR. The term ‘endpoint detection and response’ refers to endpoint detection and response. A passive threat protection platform like an endpoint protection platform or an EPP, as opposed to an active threat protection platform like an endpoint detection and response platform or EDR, helps investigate and contain breaches that have already taken place. EPPs protect each endpoint by isolating it, while EDRs provide context and data for attacks that affect multiple endpoints at once. A modern endpoint security platform typically integrates both endpoint protection and endpoint detection
What is considered an endpoint?
An organization’s network endpoints are devices that connect to its network from outside its firewall. Endpoint devices include the following:
- Laptops
- Tablets
- Desktop computers
- Mobile devices
- Internet of Things devices
- Wearables
- Digital printers
- Scanners
- Point of sale (POS) systems
Endpoints are essentially any devices connected to a central network.
FAQs about endpoint security
Endpoint security, endpoint protection, and EDR security questions include the following:
What is EDR?
Endpoint detection and response are also known as EDR. Sometimes this is referred to as ‘endpoint threat detection and response’ or ETDR. Endpoint security solutions detect and respond to online threats such as malware and ransomware by continuously monitoring endpoint devices.
How does EDR work?
EDR technology analyzes user behaviors on your system once it is installed. Signals of suspicious behavior will be detected and flagged by these algorithms. When an alarm is raised, an investigation begins to determine whether the hit is genuine or a false positive. When malicious activity is detected, the algorithms trace the attack path back to its origin. End-users are notified of suggested actions and recommendations.
What is XDR vs EDR?
Extending detection and response is known as XDR. While EDR is focused on protecting endpoints, providing in-depth visibility, and preventing threats for a particular device, XDR security integrates security across endpoints, cloud computing, email, and more.
What is the difference between EDR and EPP?
Endpoint detection and response refers to EDR, while endpoint protection platform refers to EPP. Proactive solutions are offered by EPP, while reactive solutions are offered by EDR. Platforms that protect endpoints from security threats prevent threats to specific devices. Your EPP and other security tools might have missed threats detected by endpoint detection and response solutions. Platforms designed to secure endpoints today typically combine both approaches.
What is the difference between EDR and antivirus?
Antivirus programs scan, detect and remove cyber threats such as viruses and malware. Security systems that use EDR are capable of much more than just protecting data. To provide comprehensive online threat protection, EDR includes anti-virus and security features such as firewalls, whitelisting tools, and monitoring tools. EDR is responsible for protecting an organization’s digital network’s various endpoints. Hackers are constantly devising new ways to access and steal information, as well as trick employees into disclosing sensitive information. Businesses of all sizes should implement endpoint security because data breaches can result in reputation and financial damage. eScan offers a range of endpoint security solutions for businesses.







