In our hyper-connected world, data mishaps are the new normal. The threat of data breaches, leaks, and losses has become a major concern for organizations of all sizes. There are significant financial risks involved with these incidents, as well as reputational damage and legal consequences. Organizers must distinguish between data breaches, data leaks, and data losses to protect sensitive information and protect their customers’ trust. Additionally, data loss prevention (DLP) and accidental data exposure (ADE) strategies are important for maintaining a secure digital environment.
Data Breach
Data breaches occur when unauthorized individuals obtain sensitive information. Information such as personal identifiable information (PII), financial records, and trade secrets can be stolen from an organization’s network or environment when cybercriminals exploit security vulnerabilities. It is possible to gain financial gain through data breaches by selling stolen data on the dark web, or espionage or sabotage can be the motive behind data breaches.
There is no denying that data breaches are a common occurrence, and they have a substantial economic impact. It is increasingly important for organizations to take preventive measures to prevent data breaches due to the rising costs associated with them.
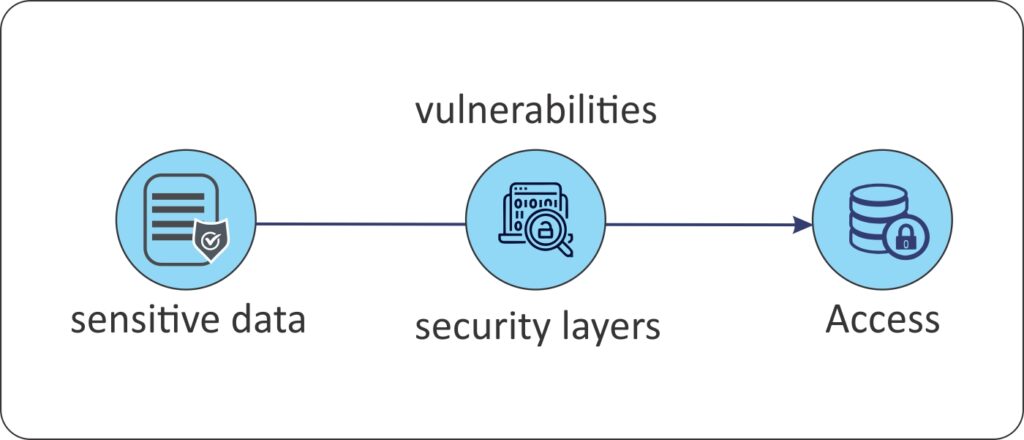
Data Leak
When sensitive information is accidentally exposed during transit or at rest, it is known as a data leak. A data leak can occur in a variety of ways, including unprotected databases, misconfigured servers, or human errors, such as sending an email with confidential information to the wrong recipient.
There are cases in which cybercriminals gain access to sensitive data through a data breach and publish it on the dark web. Data leaks are particularly difficult to detect and remediate promptly, posing a serious security threat to organizations.
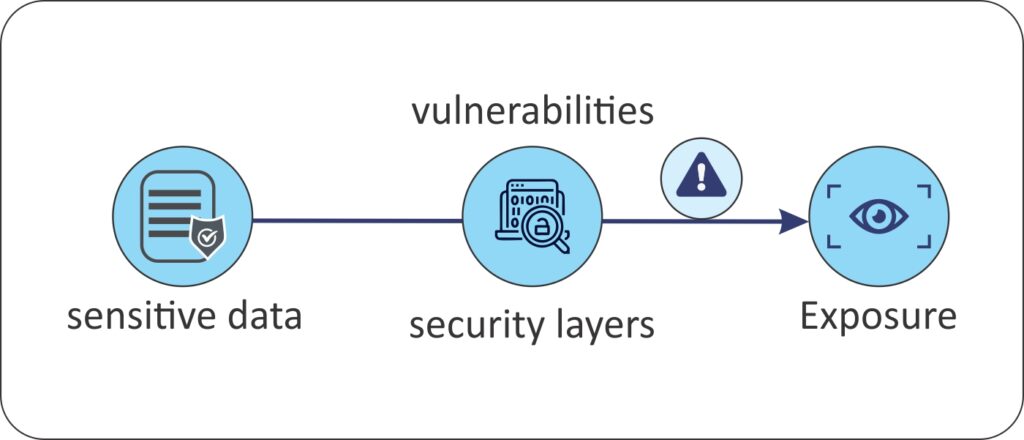
Data Loss
Cyberattacks and insider threats can result in data loss when sensitive data is unintentionally misplaced or stolen. In addition to data breaches, data loss also includes situations when information cannot be retrieved due to human or system error, or hardware failure.
An organization’s reputation may be damaged by data loss, which can lead to financial losses, operational disruptions, and reputational damages. Data loss incidents can have exorbitant downtime costs, emphasizing the importance of proactive data protection strategies.
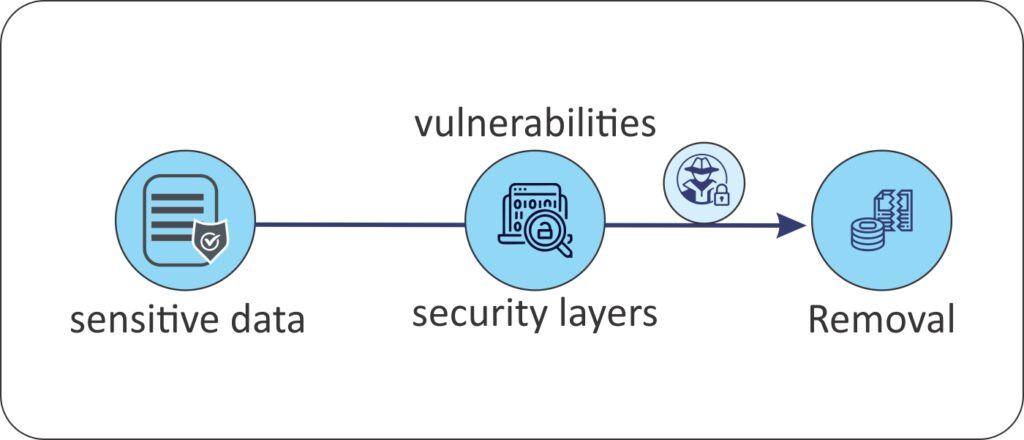
Distinguishing Data Breaches, Data Leaks, and Data Loss
While data breaches, data leaks, and data loss share similarities, they are distinct events:
1. Data Breach = Access —involves unauthorized access to sensitive information by cybercriminals through security vulnerabilities.
2. Data Leak = Exposure — involves the unintentional exposure of sensitive data, either through human error or overlooked vulnerabilities.
3. Data Loss = Removal — encompasses both accidental and intentional removal of sensitive data, often due to errors or theft.
Real-world Data Compromising Events
Data Breach: Equifax
One of the major credit reporting agencies, Equifax, experienced one of the most significant data breaches in history in 2017, exposing the personal information of over 147 million people. There was a breach involving sensitive data, such as names, Social Security numbers, birth dates, addresses, and in some cases, driver’s license numbers. This breach had severe fallout, resulting in congressional hearings and the largest-ever data breach settlement of up to $700 million to compensate affected individuals and strengthen data security measures. [1]
Data Leak: Panama Papers
Panama Papers, or the Panama Papers leak, exposed 11.5 million documents from the Panamanian law firm Mossack Fonseca. Several high-profile politicians, celebrities, and wealthy individuals were found to have engaged in offshore financial dealings and tax evasion. There were far-reaching consequences connected to the leak, such as the resignation of several politicians and the launch of investigations and reforms across a number of countries in response. [2]
Data Loss: RockYou and RockYou2021
As a result of exploiting a SQL injection vulnerability, RockYou, a social app website, suffered a significant data loss incident in 2009. There were over 32 million passwords stored in plain text exposed due to the breach. As of today, the RockYou list has grown into the RockYou2021 file, which contains an astounding 8.4 billion entries. According to recent studies, just 512,000 passwords accounted for nearly all credential-based attacks on two common types of servers between January and December of last year. The incident highlights not only the ongoing risk of using common passwords but also the importance of robust data protection measures, including proper encryption and vulnerability management. [3]
Preventing and Responding to Data Breaches, Data Leaks, and Data Loss
These security incidents can be prevented if organizations adopt proactive measures
Preventing Data Leaks:
1. Protection of outbound email from Accidental Data Exposure (ADE): An outbound email security solution helps protect sensitive information from being inadvertently exposed by proactively identifying and securing it.
2. Increase employee awareness of cyber threats like phishing and social engineering to reduce the risk of insider data leaks.
3. By using behavioural analytics, you can identify potential malicious activities and spot insider threats before they escalate.
4. Privileged Access Management (PAM): Limit access to sensitive information to those who need it, decreasing the likelihood of unauthorized data exposure. Consider regular audits to ensure compliance and identify vulnerabilities.
Preventing and Responding to Data Breaches:
1. A regular vulnerability scan and patching program is a good way to minimize the risk of a breach in the network and systems of an organization.
2. Monitoring network traffic and identifying suspicious activities indicative of a potential breach is the purpose of Intrusion Detection Systems (IDS).
3. Developing and practising an Incident Response Plan (IRP) in order to respond quickly to breaches and mitigate their impact is essential.
4. Cybercriminals can exploit software backdoors to bypass security measures by identifying and eliminating them.
Data Loss Prevention (DLP) Strategies:
1. Make use of robust encryption techniques to secure data both at rest and on the move, so that unauthorized parties can’t read it.
2. Secure endpoints with advanced agents that can detect and control network and user information transfers.
3. Data leak detection efforts should be extended to include monitoring data leaks from third-party vendors in order to ensure data security across the entire supply chain.
Conclusion
Cybersecurity challenges such as data breaches, leaks, and loss must be addressed comprehensively. Developing robust prevention strategies and understanding the differences between these incidents can help businesses protect their sensitive data and maintain customer trust. Comprehensive cybersecurity approaches help safeguard against evolving threats with proactive data loss prevention measures and a sound incident response plan. Contact Us.







