LetsEncrypt has been creating waves since it started providing SSL Certificates for free and has been applauded by many for this. Researchers and Enthusiasts have been providing support to this project by various means viz. integration of LetsEncrypt with various web-servers, automation of the certificate generation process including the renewal.
It is to be noted that although LetsEncrypt provides SSL for free the validity of the certificate is for only 90 Days. In this blog-post we shall be providing the process to integrating LetsEncrypt Certificate with Communigate Pro.
Communigate Pro is one of the leading email solution provider , however, when we wanted to implement these SSL certificates we couldn’t find any tangible information , which would allow us to do the same.
Requirements:
- 1: Communigate Pro Web-Console
- 2: Zero SSL or any of the ACME Clients.
- 3: OpenSSL
Steps
ZeroSSL
1: Generate the Private Key (Save this key to some place safe.)
Note: LetsEncrypt requires the Key-size to be atleast 2048
Generate Account Private Key
openssl genrsa 4096 > ZeroSSLAccount.key
Print your Private Key
openssl rsa -in ZeroSSLAccount.key –pubout
This Key is to be used as ZeroSSL Account-Key
Communigate Pro
- Generate Server Private Key
openssl genrsa 4096 > emailDomain.key
- Create the config file as shown, this file is for multiple domains.
File Name : extfile.conf
[req]
distinguished_name = req_distinguished_name
req_extensions = v3_req[req_distinguished_name]
countryName = IN
countryName_default = IN
stateOrProvinceName = Maharashtra
stateOrProvinceName_default = MH
localityName = Mumbai
localityName_default = Mumbai
organizationName = MWTI
organizationName_default = MWTI
organizationalUnitName = IT
organizationalUnitName_default = IT
commonName = mwti.net
commonName_max = 64
emailAddress = contact@escanav.com[ v3_req ]
# Extensions to add to a certificate request
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
subjectAltName = @alt_names[alt_names]
DNS.1 = escanav.com
DNS.2 = mail.escanav.com
- Generate the CSR
openssl req -new -key emailDomain.key -sha256 -nodes -config extfile.conf -subj “/C=IN/ST=Maharashtra/L=Mumbai/O=MWTI/OU=IT/CN=mwti.net/emailAddress=contact@escanav.com/subjectAltName=DNS.1:escanav.com,DNS.2:mail.escanav.com” -out emailDomain.csr
Note: Use certutil.exe -dump <cert/key/csr> to see/check certificate.
Now that we have generated the Keys for:
- ZeroSSL
- Communigate Pro
We logon to Communigate Pro Web-Console and traverse to the following section:
Users –> Domains
We select the configured domain and then traverse to the following section:
Security –> SSL/TLS
Under the Request Client Certificates we choose the following:
PKI Services –> Enabled
Issued by –> default()
Under the Private Key Section we choose:
Key Size –> Import and then Click on Generate Key button. An additional text-area is displayed with the heading Enter a Custom PEM-encoded Key.
Copy the contents of emailDomain.key, which was generated earlier and paste them in this Text-Area.
Click on Generate Key to submit the private key.
A New section will be presented Certificate Generator, provide the Contact and Click on Create Signing Request. Although this task will generate a CSR, however this cannot be used as a CSR for ZeroSSL, since Communigate Pro used MD5/RSA as the signing algorithm and the requirement is that of SHA256/RSA.
The text-area Certificate Signing Request (CSR) is populated with the MD5/RSA CSR, however we delete the contents in this text-area.
Copy the contents of emailDomain.csr, which was generated earlier and paste them in this Text-Area.
Zero SSL
Browse to https://zerossl.com/ and paste the contents of ZeroSSLAccount.key in the Account Key text-area and contents of emailDomain.csr in the CSR text-area. Select HTTP verification, ZeroSSL TOS and Let’s Encrypt SA and then click on Next.
This is an important step since, you will now be verifying your Domain Name. Make sure that the domain name used is pointing to a web-server in the global DNS Records and is listening on Port 80.
Create the directory structure as mentioned in ZeroSSL
https://domainname/.well-known/acme-challenge/
Note:
- While using IIS, use command prompt to create the directory structure in the directory which is hoisting the website. Create the file with the contents as mentioned by ZeroSSL.
- Open The IIS Manager and traverse to the hoisting site and select Mime-Type and add “.” “text/plain” , otherwise IIS will display an error.
- After the HTTP verification delete the added Mime-Type
- Multiple Domains when used during the creation of CSR would result in multiple verification requests.
Before clicking Next, browse to the location, so as to ensure that the contents of the challenge file are visible. After Clicking Next, the Certificate will be generated and will be made available for download.
Download and store these files in a safe location.
Convert the domain-crt.txt to PEM format, since this is the format which is accepted by Communigate Pro.
openssl x509 -inform PEM -in domain-crt.txt > domain.pem
Copy the contents of domain.pem and paste them into the Enter a PEM-encoded Certificate text-area box and then click Set Certificate button.
The final screen of the adding LetsEncrypt SSL Certificate shows the details of the certificate including the issuer and its expiry date.
Note: Save the Account Number for quick reference
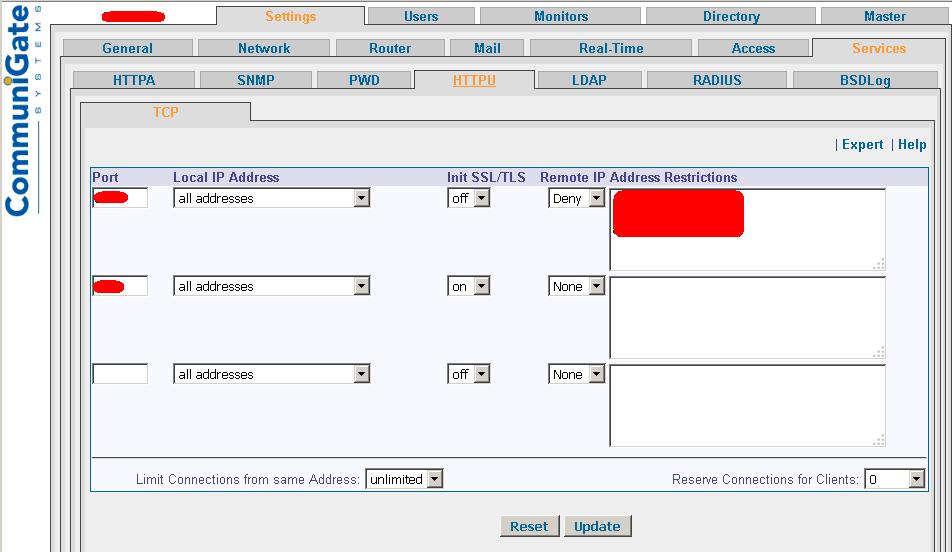
Enabling the HTTPS Listner
We logon to Communigate Pro Web-Console and traverse to the following section:
Settings –> Services –> HTTPU –> Init SSL/TLS –> On
Verifying the Certificates
- Authors : DeepakS and SachinR