An alert issued by the Department of Homeland Security warned of surreptitious activity by the Volgmer malware used by the “Hidden Cobra” hacker group, in the wild to target the government, financial, automotive and media industries. Volgmer is a backdoor Trojan designed to provide covert access to a compromised system.
According to CERT, it is suspected that spear phishing is the primary delivery mechanism for Volgmer infections; however, hidden cobra actors use a suite of custom tools, some of which could also be used to initially compromise a system. As a backdoor Trojan, Volgmer has several capabilities including: gathering system information, updating service registry keys, downloading and uploading files, executing commands, terminating processes, and listing directories.
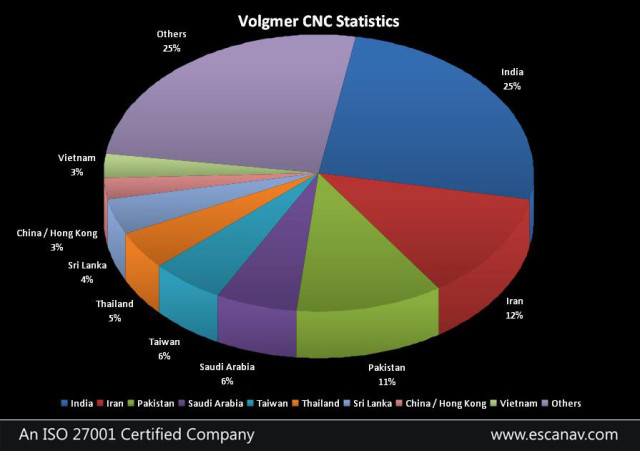
The U.S. Government has analyzed Volgmer’s infrastructure and have identified it on systems using both dynamic and static IP addresses. At least 94 static IP addresses were identified, as well as dynamic IP addresses registered across various countries. The greatest concentrations of dynamic IPs addresses are identified above by approximate percentage.
With 25%, India is hosting the largest concentration of Volgmer’s Infrastructure, which in itself is a worrying fact. The internet penetration in India is at all-time high; however it is quite evident from these statistics that Indian IT lacks strict compliance of security standards.
eScan’s Advisory:
- Application whitelisting allows only specified programs to run and blocks all malicious software and unapproved programs that run.
- Administrators should block all executable files from being transmitted via emails.
- Administrators should isolate the affected system in the Network.
- Administrator can restore the encrypted files from the backup or from system restore point (if enabled) for affected systems.
- Keep operating systems and software up-to-date with the latest patches.
- Users shouldn’t enable macros in documents.
- Organizations should deploy and maintain a backup solution.
- Most important, organizations should implement MailScan at the Gateway Level for mail servers, to contain the spread of suspicious attachments.