A new stealthy backdoor from the authors of TrickBot that is used to compromise and gain full access to corporate networks is being delivered through a new phishing campaign.
Gaining access in a quiet manner over a corporate network is a mandatory step in an advanced network attack such as enterprise-targeting ransomware, corporate espionage, or data exfiltration attacks.
In phishing attacks that were discovered over the past two weeks, a new malware called BazarBackDoor is being installed that deploys a network-compromising toolkit for the threat actors.
Due to the similarities in the code, executable crypters, and its infrastructure, it is believed that the developers of the infamous TrickBot trojan are behind this new backdoor.
Utilizing a wide array of lures, such as customer complaints, COVID-19 themed payroll reports, and employee termination lists that contain links to documents hosted on Google Docs, the initial attacks of the phishing campaign is executed.
The Sendgrid email marketing platform is utilized by the attackers when sending the phishing emails.
this campaign is putting a lot of thought into their creatives by stylizing their landing pages to correspond to the lures, or themes, of the emails, unlike many other phishing attacks
Examples of the same can be seen below where one landing page is a COVID-19 payroll report template while the other is a customer complaint from a corporate lawyer.
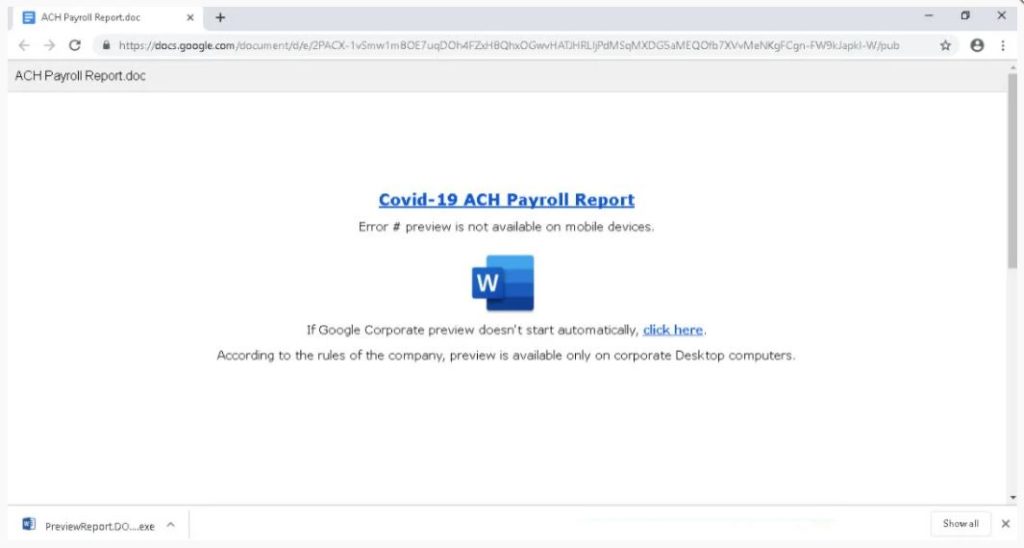
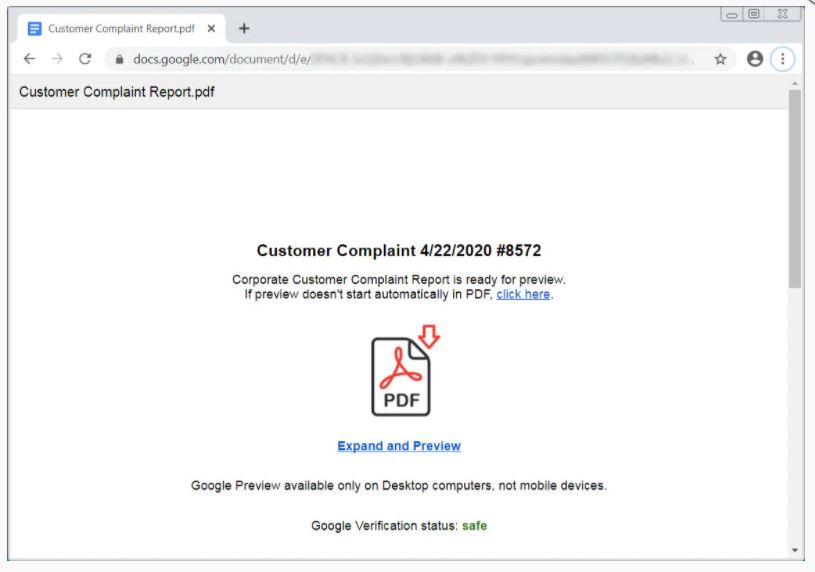
Both these landing pages pretend to be either a Word document, an Excel Spreadsheet, or a PDF document that cannot be viewed properly and prompts the user to click on a link to properly view the document.
An executable will be downloaded instead that uses an icon and name associated with the icon shown on the landing page when the given link is clicked.
Continuing the same example, the ‘COVID-19 ACH Payroll Report’ theme will download PreviewReport.DOC.exe, while the “Customer Complaint” theme will download Preview.PDF.exe.
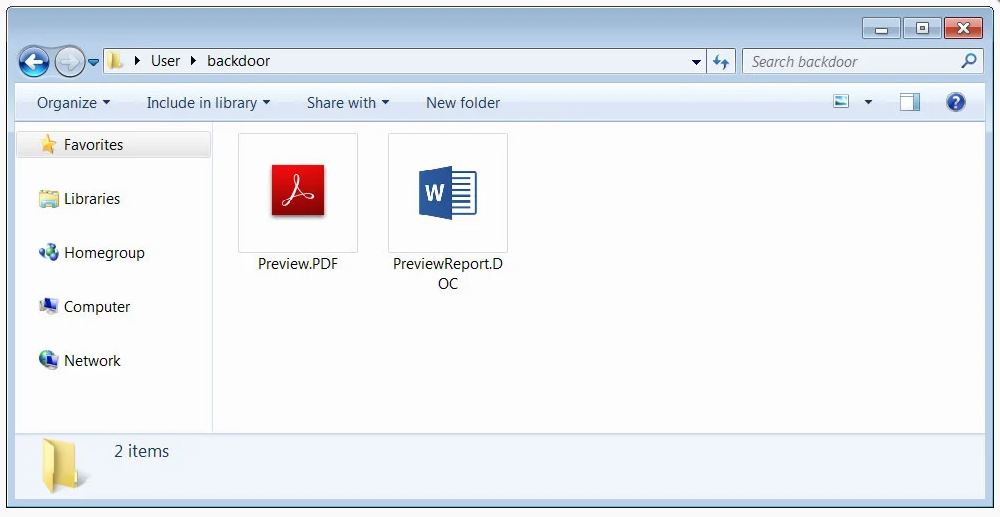
Users will be fooled into opening the extensions thinking they are legitimate Word and PDF documents since Windows does not display file extensions by default, most users will see “Preview.PDF” or “PreviewReport.DOC”
This executable is the loader for the backdoor and is being called “BazaLoader”.
The backdoor will be stealthily installed on the computer, once it is launched.
Loading the fileless backdoor
Once the victim launches the downloaded file, the loader will sleep for a short period of time and then connect to command and control servers to check-in and download the backdoor payload.
The BazarLoader will use the Emercoin decentralized DNS resolution service to resolve various hostnames that use the ‘bazar’ domain, to get the address of the command and control servers. The ‘bazar’ domain can only be utilized on Emercoin’s DNS servers, and as it is decentralized, it makes it difficult, if not impossible, for law enforcement to seize the hostname.
The hostnames used for the command and control servers are:
- forgame.bazar
- bestgame.bazar
- thegame.bazar
- newgame.bazar
- portgame.bazar
The loader will first connect to one C2 and perform a check-in once the IP address for the command and control server is resolved. In our tests, this request always returned a 404 HTTP error code.
The second C2 request, though, will download a XOR encrypted payload, which is the BazarBackdoor backdoor malware.
The payload will be injected post its download into the C:\Windows\system32\svchost.exe process. According to a researcher, this is done using the Process Hollowing and Process Doppelganging techniques.
An additional svchost process is not likely to arouse suspicion for most users, since they have grown used to svchost.exe processes running in Task Manager.
When a user logs into Windows, a scheduled task will also be configured to launch the loader, which will allow new versions of the backdoor to be routinely downloaded and injected into the svchost.exe process.
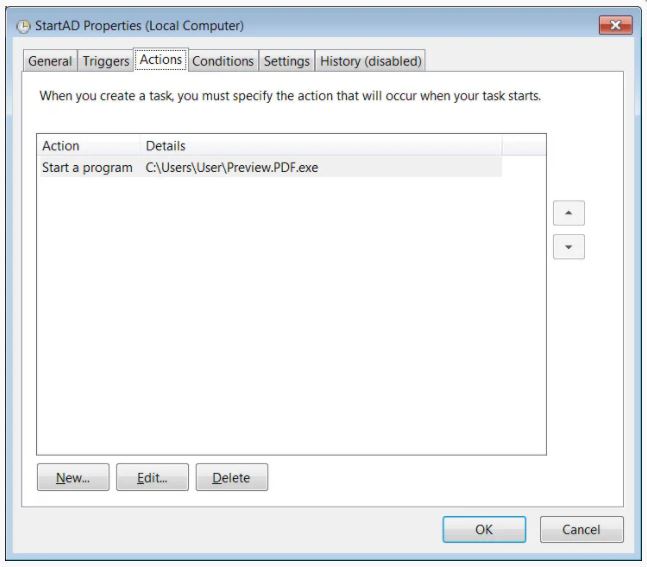
After a period of time, the backdoor will download and execute the Cobalt Strike penetration testing and post-exploitation toolkit on the victim’s machine. Cobalt Strike is a legitimate cybersecurity application that is promoted as an “adversary simulation platform” intended to perform network security assessments against a simulated advanced threat actor persisting in a network.
As part of their toolkit, attackers, though, commonly use cracked versions of Cobalt Strike, when spreading laterally throughout a network, stealing credentials, and deploying malware.
With the deployment of Cobalt Strike, it is evident that this stealthy backdoor is being used to gain footholds in corporate networks so that ransomware can be deployed, data can be stolen, or to sell network access to other threat actors.
Ties to the TrickBot
Researchers have further revealed that this malware is enterprise-grade and is likely developed by the same group behind the TrickBot trojan. Both the BazarBackdoor and Trickbot utilize the same crypter and email chain deliverables as previous TrickBot campaigns. TrickBot Anchor project also uses the Emercoin DNS resolution service for command & control server communication.
Further tying the two malware together the malware’s command and control server’s TLS communications had been seen using certificates created in the same manner that historic TrickBot certificates have been created.
Based on the volume of phishing emails being sent out using this new loader/backdoor, BazarBackdoor poses a grave threat to corporate networks that could easily be used to deploy ransomware or perform other attacks.
Organizations should be vigilant and warn employees of emails coming from sendgrid.net that contain links that download files to prevent their employees from being infected.
To read more, please check eScan Blog







