A legitimate penetration testing toolkit used by red teams called Cobalt Strike had its source code allegedly leaked online in a GitHub repository.
This tool enjoys rich popularity in the world of cybercrime as well. The cobalt strike toolkit allows attackers to deploy “beacons” on compromised devices to remotely create shells, execute PowerShell scripts, perform privilege escalation, or spawn a new session to create a listener on the victim system.
This tool is commonly seen used during ransomware attacks.
A few days ago, a repository containing what appears to be the source code for Cobalt Strike 4.0 was discovered.
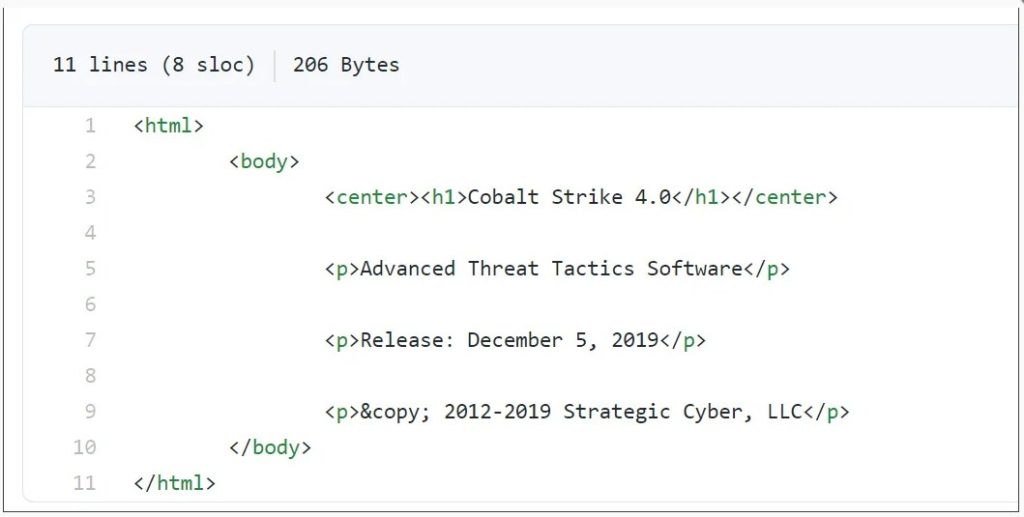
This source code is for Cobalt Strike 4.0 released on December 5th, 2019, based on the ‘src/main/resources/about.html’.
As seen below, the license check for Cobalt Strike has been commented out which means, the program is available in a cracked version for anyone who decides to compile it.
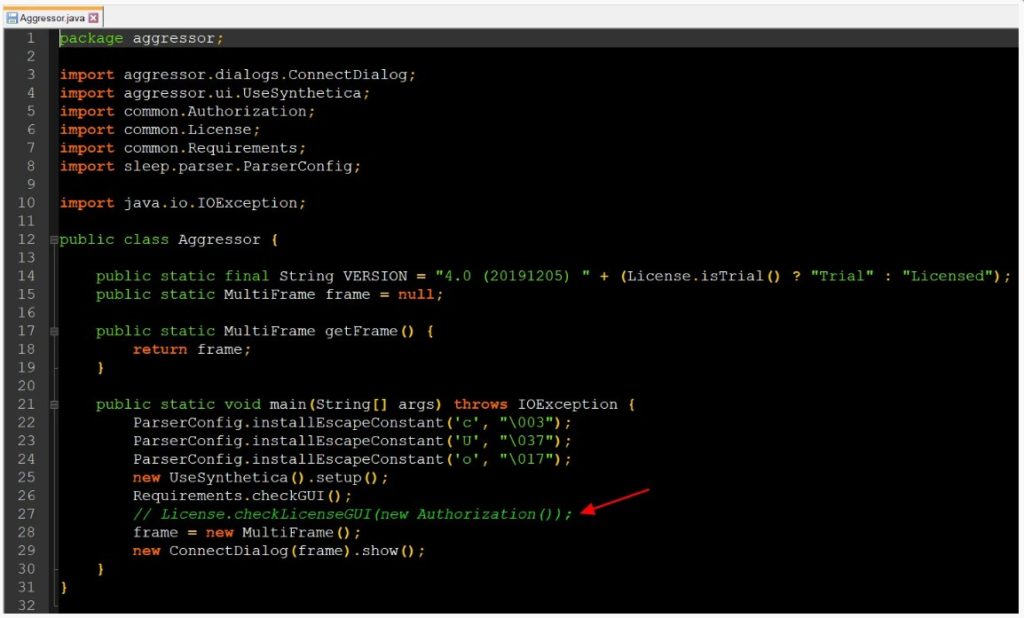
Researchers who have examined the source code believe that the Java code was manually decompiled, fixed any dependencies that were present, and then removed the license check so that it could be compiled.
The spread of this code has been hard to contain since the repository has been forked 172 times from the time it has been posted online. Even without being the original code, it is enough to give security professionals more than a few sleepless nights.
The allegedly recompiled source code of Cobalt strike 4.0, removes barriers of entry to obtain the tool and essentially makes it easy for the crime groups to procure and modify code as needed on the go, posing significant consequences for all defenders.
This leak can be considered as a foot in the door for the additional crime actor enhancement of the tooling as it happens with the many malware tool leaks as they are continuously re-used and updated by the various malicious groups.
Consequently, our internal experts suggest several precautionary activities, such as looking up for the open port on 50050/TCP or checking the default TLS certificate from the vendor. Limiting admin privileges to essential users can also add to the precautionary measure.
To read more, please check eScan Blog







