Following the efforts of the defenders of our sacred cyberspace that have been targeting the Trickbot’s command and control servers, the malware’s operations are on the brink of completely shutting down. Its operators were undaunted by the initial efforts of cybersecurity providers and were able to rebuild the infrastructure and the network of infected computers.
The collaboration headed by Microsoft’s Digital Crimes Unit (DCU) has had a serious impact which is evident from the latest score in the fight against Trickbot.
Last month, on the 12th of October Microsoft, announced that they had taken down some Trickbot C2s along with its partners.
Before executing this, the U.S. Cyber Command reportedly tried to cripple the botnet ahead of the presidential elections by pushing a configuration file to infected computers that cut them off from the controlling servers.
Among the partners, it was understood that this opening salvo would not bear fruit and described it as a work in progress, without a guarantee of bringing the downfall of the botnet.
Researchers later noticed that the Trickbot continued to infect new computers, helped by its long time partner, Emotet, which also spreads QBot.
To download and execute the Trickbot on the victim’s machines, the Emotet bots reach out to their controllers and received commands. This campaign was being observed by researchers for the last 6 months.
The Expected Fightback
Administrators of the Trickbot are constantly rotating the C2 IP addresses and changing the infected hosts, making disruption efforts a serious challenge. Two different servers are used to communicate with the bots and to deliver plugins dedicated to specific tasks like stealing of passwords, stealing of traffic, and propagation of the malware.
It was noticed, that later the Trickbots administrators updated the plugin server configuration file with 15 new IPs. Two older addresses were kept active along with the servers through the Tor anonymity network. Consequently, without any direct noticeable change, the Trickbot campaigns had switched to new C2 channels.
Turning of Tables
Microsoft then released an update stating that together with its partners across the world they worked to disable 94% of Trickbot’s critical infrastructure.
“As of October 18, we’ve worked with partners around the world to eliminate 94% of Trickbot’s critical operational infrastructure including both the command-and-control servers in use at the time our action began and new infrastructure Trickbot has attempted to bring online” – Microsoft
The core infrastructure of the Trickbot includes internet-of-things (IoT) devices for controlling the botnet, seven of them were identified by Microsoft and its partners and were in process of being disabled.
The unique architecture of the Trickbot requires constant action against it to minimize resurrection chances and the small win does not mean the war against the enemy is won.
Microsoft further stated “As we continue to cut off these new servers, our partners are also working to clean and remediate the compromised IoT devices, especially routers, that the Trickbot operators are using as non-traditional command-and-control infrastructure”
Microsoft is working with internet service providers (ISPs) to help fix the devices without interrupting legitimate traffic, as TrickBot is hosting command and control servers on customer and business routers.
For now, Trickbot administrators are busy setting up new infrastructure, which takes time and a toll on the frequency of fresh attacks.
According to Microsoft, they were able to identify new servers and o through the legal channels to disable them in less than three hours. In one case, a hosting provider took down a Trickbot server in less than six minutes since receiving the notification about the illegal activity.
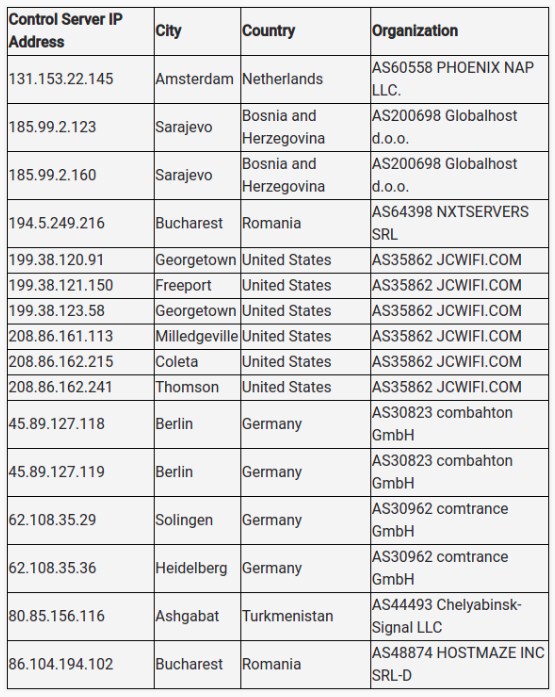
Researchers identified 16 new C2 botnet servers dispersed globally, none of them currently responding to requests from infected systems.
Hard to Kill
According to the same research team, Some Trickbot servers are still active in Brazil, Colombia, Indonesia, and Kyrgyzstan with the botnet’s administrators still having partners willing to spread their malware.
There is a possibility of the botnet dying on its own even if the collaborated efforts don’t end the botnet’s existence. However, that’s only because the threat actors are moving to BazarLoader to target high-value enterprises and deploy Ryuk ransomware on their networks.
To read more, please check eScan Blog