Cybersecurity in this era has taken a radical stage breaking its age-old limits of detecting threats such as worms and viruses. Earlier defense tactics were highly effective since the attacks were relatively simple. Since protection is not enough anymore, and quick and intelligent incident response needs to be warranted for the corporates and businesses.
Using malicious bots is one of the common modes of attack and businesses need to update their incident response plan in order to face these advance levels of threats. Fortunately, these Intelligent bots can be used for the good as well.
So What is Incident Response?
A schematic approach to managing cybersecurity breaches or cyber-attacks is called as Incident Response. To prevent a greater impact, businesses have an incident response plan in place to handle cyber-attacks effectively. An Incident response plan usually involves a step by step process that constitutes a company’s business continuity plan. An incident recovery team is responsible for implementing the firm’s incident response plan. The team could include responsible members from different departments like IT, HR, Legal Counsel, and even Communications.
In the event of a physical or digital security breach, losing functionality due to a data breach could be a colossal hindrance to any organization. Given the fact that no network is 100% safe or secure, in the event of an attack being prepared is crucial for saving time and having an incident response strategy helps in mitigating the risk.
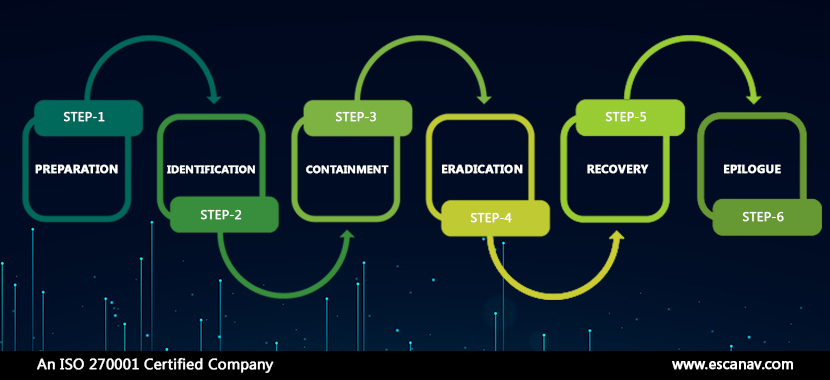
6 Crucial Steps of an Incident Response plan
Composing of a series of steps addressing the security incident in an organized way, every business should have an Incident Response Plan in place. The stages to stringing together a plan are as follows.
- Preparation – This step includes ensuring that incident response is in place, and people constituting the team need to be properly trained for their roles during a security incident. Part of the preparation should be establishing policies and procedures while testing them with mock drill scenarios.
- Identification – As a process, in this step, the team collects data from systems and various tools to identify any indication of compromise. The end goal is to identify what kind of cyber attack has been or is being carried out. The larger the information pool, the better the strategy would be to deal with it.
- Containment – The end goal of this step is to rebuild the operating system by carrying a coordinated shutdown and wiping of the infected devices or systems.
- Eradication – Once the threat has been discovered, it should be made sure that the malware is removed from the system, which is the root cause of the breach.
- Recovery – Through this stage, the affected systems are brought back to their operative state.
- Epilogue – Once the security incident is taken care of, the incident response team should ensure that any information that can help such an incident in the future is documented. This includes maintaining a complete incident report and carrying out a post-incident monitoring phase.
Incident response in today’s age is of paramount importance and with the advancement of technology, we can even use bots that are often used with a malicious purpose to aide incident response. To know more about it, keep reading the next installment of our blog.
To read more, please check eScan Blog