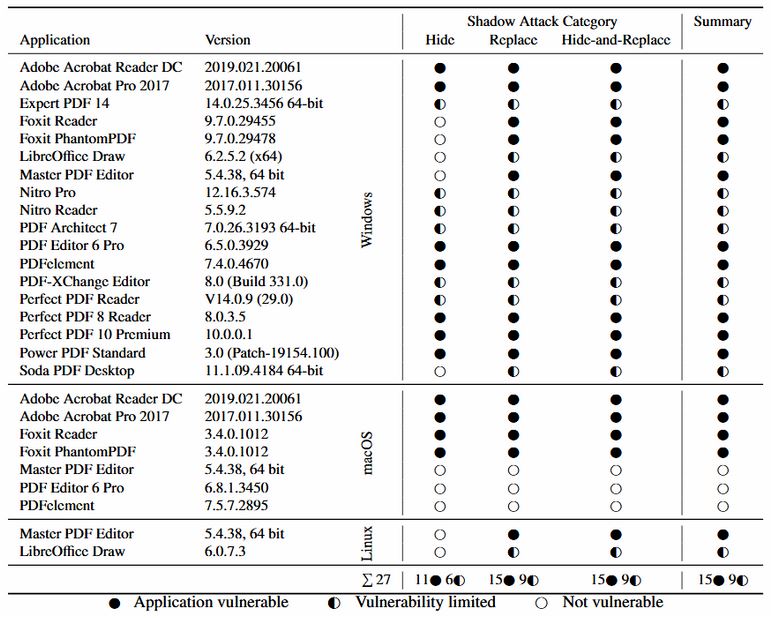
A new attack that lets malicious threat actors modify the content of digitally signed PDF documents have rendered Fifteen out of 28 desktop PDF viewer applications as vulnerable to exploitation. According to new research published by academics from the Ruhr-University Bochum in Germany, the list of vulnerable applications includes Adobe Acrobat Pro, Adobe Acrobat Reader, Perfect PDF, Foxit Reader, PDFelement, among others.
This technique of forging documents is named as a Shadow Attack by academics.
The concept of “view layers” is the main idea behind the Shadow Attack. According to this concept, different sets of content are overlaid on top of each other inside a PDF document.
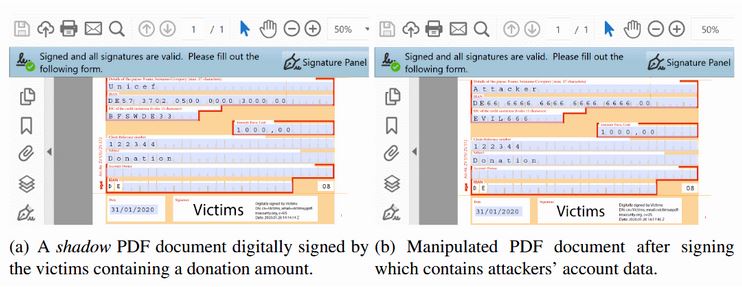
A Shadow Attack is when a threat actor prepares a document with different layers and sends it to a victim. With a benign layer on top, the victim digitally signs the document but the visible layer is changed to another once the attackers receive the document.
Since the layer was a part of the original document that the victim signed, changing the visibility of the layer doesn’t alter the cryptographic signature and still enables the attacker to use the legally binding document for heinous actions. These actions could include the payment receipt or sum in a PDF payment order or altering contract clauses.
Three different versions of Shadow Attack exists according to the researchers –
- Hide – When the PDF’s standard incremental update feature is used by the attackers to hide a layer without replacing it with anything else.
- Replace – When the PDF standard’s interactive form feature is used to replace the original content with a modified value.
- Hide-and-replace – This is when the attackers use a second PDF document in the original document to replace it altogether.
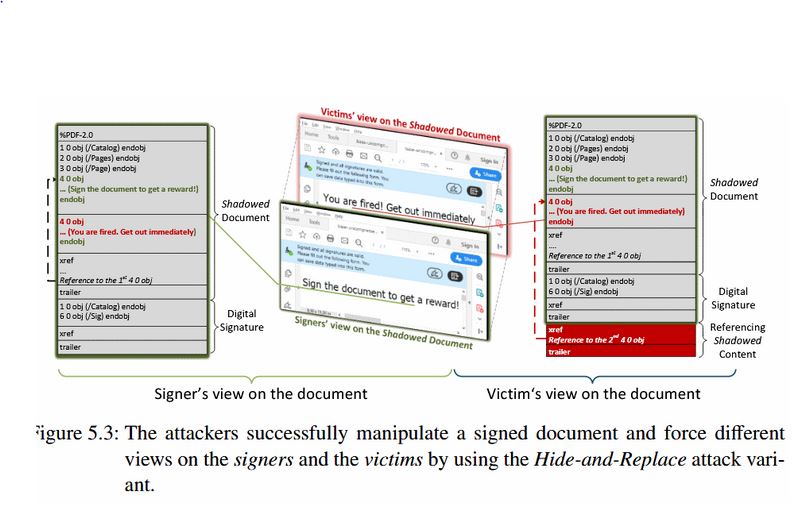
According to researchers the most powerful variant among the three is the Hide-and-Replace attack variant since the content of the entire document can be exchanged. Influencing the presentation of each page, or even the total number of pages, as well as each object contained therein the attacker can build a complete shadow document.
Researchers add further, PDF documents even when digitally signed, allow unused PDF objects to be present inside their content and hence, Shadow Attacks are possible. PDF viewer apps that remove unused PDF objects when signing a document are immune to Shadow Attacks.
Available Patches
The PDF app maker team was contacted by the researchers along with the Computer Emergency Response Team of Germany to report this new attack vector and have it patched before going public with their findings earlier this week.
The Shadow Attack is currently tracked with the CVE-2020-9592andCVE-2020-9596 identifiers
To make sure the PDF documents they sign can’t be tampered with via a Shadow Attack, our security experts advise organizations to update their PDF viewer apps.
This is the second time in two years that the same group of threat actors has broken digital signatures for PDF viewer applications. In February 2019, the same team broke the digital signing mechanism on 21 of 22 desktop PDF viewer apps and five of seven online PDF digital signing services to create documents with fake signatures.
Because it doesn’t tamper with the digital signature, as the first attack, but with the content of the PDF without breaking the signature, their new Shadow Attack is very different from their first attempt.
To read more, please check eScan Blog