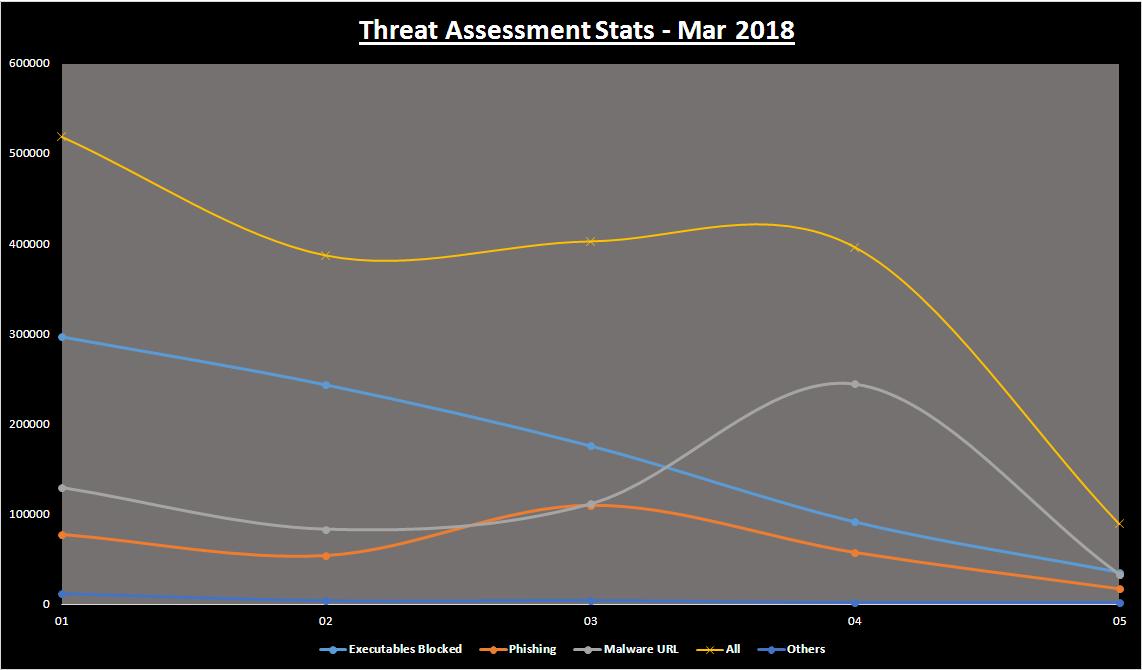
As we reach the end of the financial year, the analysis of the global threat stats show consistent numbers until the weekend. The weekend was an exception where we saw a slight rise followed by a dip on Monday across most of the threats analyzed. Recent reports say there are at least five sophisticated threat groups whose activities focus on industrial control systems (ICS). Unpatched vulnerabilities tend to be the major reason behind successful security attacks. It is advisable that all to adopt the DMARC, the Domain-based Message Authentication, Reporting & Conformance standard, introduced by email service providers to keep phishing and spam related to domain name spoofing at bay, and to provide greater visibility into email ecosystems at the same time. Also powerful new computer virus called Goner was seen is spreading through the Internet last week. It is an email attachment labeled “gone.scr. Therefore individuals are altered to keep away from such virus attacks.
Now, the analysis of the below report attempts to highlights ransomware invasions during the week. We have seen a great week as there has been an almost steep fall in the ransomware activity.

As Ransomware invasion generally strikes at unexpected instances it is important to keep a continuous watch on its trend. Below is the hourly record of ransomware attack in the past week. Our telemetry servers surprisingly recorded a maximum rise of Ransomware attack on the 1st of March. The chaos calmed down later on through the week. EScan researchers saw spikes at some point every day. Hence it proves that individuals and companies are never allowed to ease their security mechanisms at any cost as crooks are on persistent look out for vulnerable network areas to inject their malicious activities.

Solution:
- Always keep your antivirus software updated , this will protect your machine from all types of threats from the network
- Make sure you download any apps or updates from Google play store or official websites.
- If you have to download apps from elsewhere make sure it is from a trusted website, and do check the user ratings on it before you download it.
- Make sure all the basic Software like Oracle Java and Adobe on your system are up-to-date.
- In Organizations, follow the 3-D security policy :
- Understand Requirements to decide on a suitable security policy,
- Train your staff on the policy
- Finally implement the policy.
- Make sure you either implement MailScan at gateway level or enable Mail Anti-virus on the endpoint in order to block extensions such as *.EXE, *.SCR, *.JS, *.VBE etc. These attachments are the ones that could infect your system.
- Check an email only if you trust the source.
- eScanAV Anti-Virus Toolkit (MWAV) is a FREE utility that enables you to scan and clean Viruses, Spyware, Adware and any other Malware that may have infected your computer.
- Last but not the least, regularly backup all your important files.