The Haywood County School district in North Carolina suffered a data breach after having unencrypted files stolen during an attack by the SunCrypt Ransomware operators, on August 24th, 2020. This attack caused the district to shut down its network and hampered their remote learning process, which had started on August 17th.
The school apologized for the inconvenience caused to its students and the parents due to the security breach while assuring them about the resumption in services.
After a thorough investigation it was revealed that unencrypted data was stolen during a ransomware attack.
A few days later they announced that they had suffered a breach in security and were doing everything possible to eliminate any potential harm to staff, students, and affiliates. They also shared that forensic work had not determined the extent to which data theft was executed and hence, requested their staff, students, and parents to be vigilant and report any suspicious activity.
It was later disclosed that the SunCrypt Ransomware operators were behind the attack on the school district.
As part of their tactics, the SunCrypt operators steal unencrypted data before encrypting an organization’s devices and threatening to release the data if a ransom is not paid.
A 5GB data cache containing data stolen from the school district was published over the internet since the school opted not to pay the ransom.
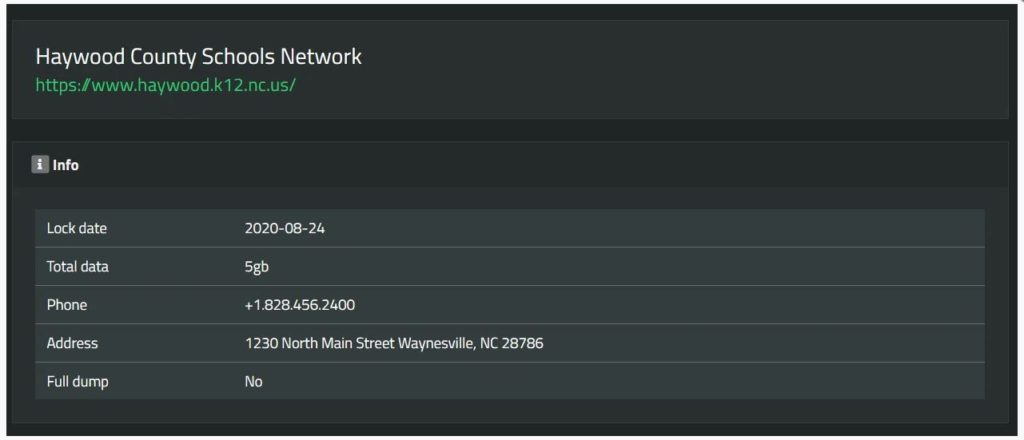
The data that was leaked consisted of various sensitive documents and personal information related to the school district, students, and teachers.
Analyzing the Ransomware Attack
A PowerShell script is created when the SunCrypt ransomware operators perform an attack and it is named after the victim while being stored on the network’s Windows domain controller.
When the Suncrypt powershell is executed on a device, it launches the ransomware and encrypts the files on the computer.
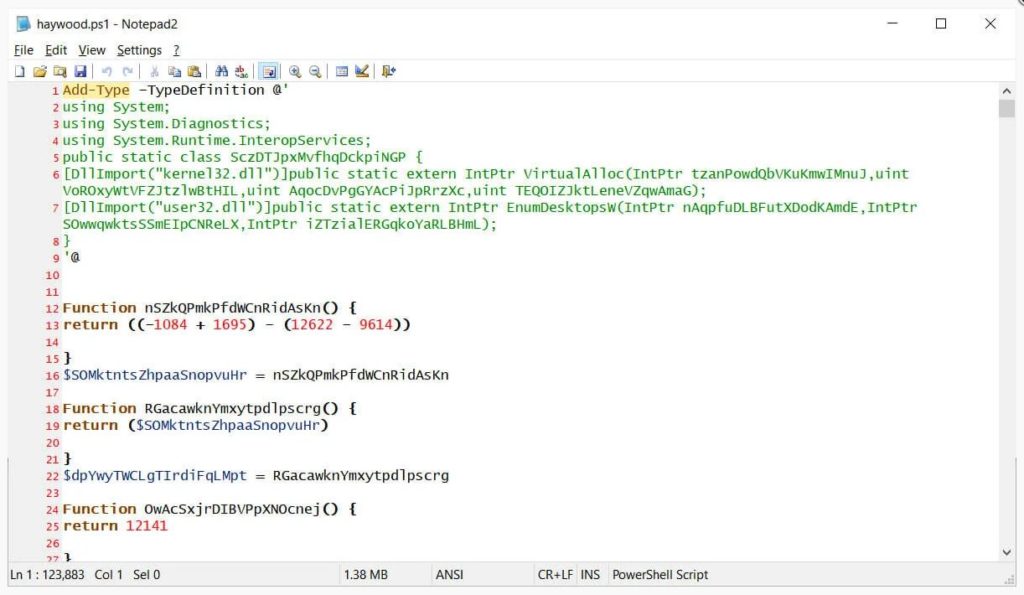
The attackers push a batch file to each Windows device on the network, in order to launch the powershell on every computer. When this batch file is executed it runs the haywood.ps1 script stored on the domain controller and encrypts the computer.
Attackers can compromise a network, by performing the attack in this way, quietly harvesting files to steal them, and then pushing out the ransomware to all of the devices simultaneously.
Without being detected this method allows the attackers to quickly encrypt all devices on the network.
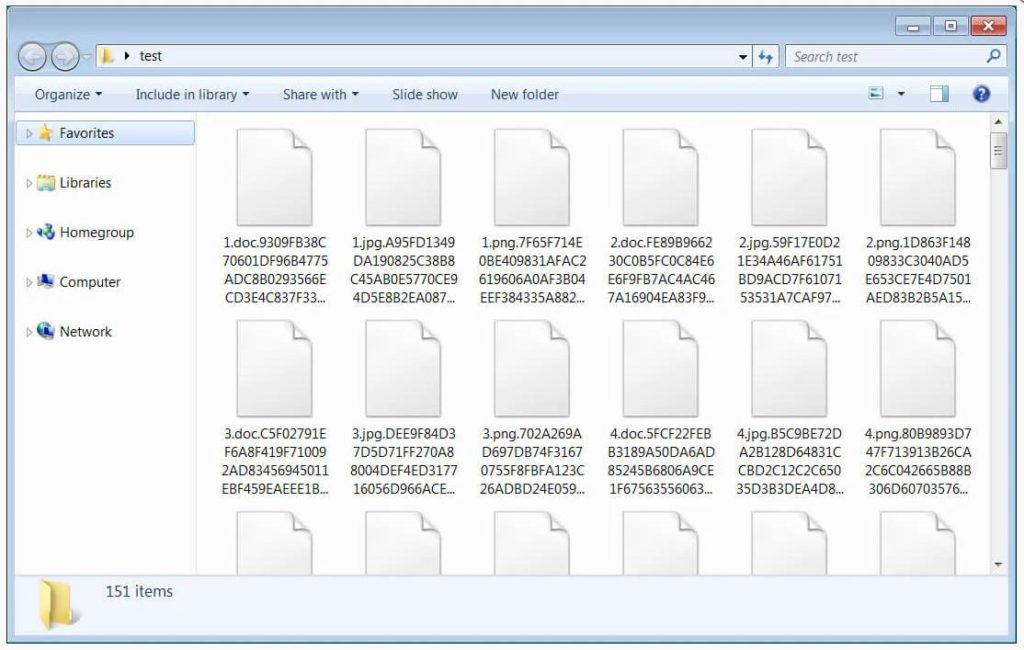
Once the ransomware has spread and encrypted files, the victim is left with files that have been locked and renamed.
A ransomware note named YOUR_FILES_ARE_ENCRYPTED.HTML is found in each folder and contains instructions on how to access the Tor payment site where a victim can negotiate with the ransomware operators.
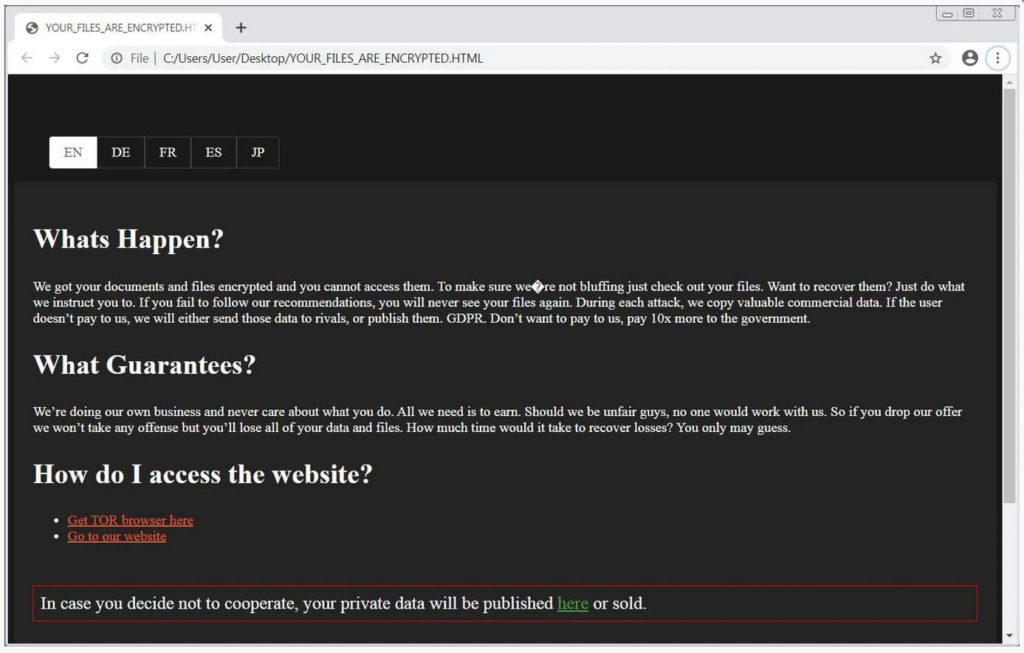
Unfortunately, SunCrypt appears to be secure, which means there is no way to currently recover files for free.
To read more, please check eScan Blog







