In my continuous effort to educate the administrators, on the nuances of WebSecurity, I will be writing about a few tools which makes life easy for the hacker and a nightmare for the administrator.
The first step towards any hack is the recon. Recon should be as perfect as possible and should be non-intrusive, the last thing you would ever want in life is to raise the suspicion of the administrator or trigger any of the alarms that might have been deployed.
A website or server may have hundreds of flaws just waiting to be exploited but never take the security for granted. Initially, you have to always think that the web-site in question is protected by IPS, IDS, SQL /RFI detecting analyzers, tripwires and the organzation has invested heavily into cyber security and has security administrators who are not over-worked. Sounds utopian? yup.
Anyway, this blog is for those administrators who are willing to walk that extra mile in securing their infrastructure.
The administrators, should always use these freely available tools to test out their servers and network infrastructure for which you are responsible, there are a few things which you will gain a: Satisfaction b: Knowledge c: and hopefully the respect of your peers.
Whenever there is a discovery of a new vulnerability in a particular application, we have observed that, within a few days all the implementations of the said application have either been hacked or the vulnerability has been successfully exploited. Either the admins have failed to patch up their servers or the vendor did not provide the patch. In either case, its the organization which suffers.
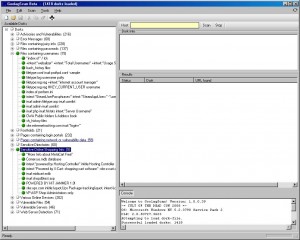
The first of the many tools is ‘Goolag Scan’, developed by CDC, creators of the infamous BackOrifice.
Goolag Scan, has has taken Google Dorks at a new level, which everyone from either side of the network (i.e. hackers and administrators) would love to use. GoolagScan offers you to scan your own server implementation for vulnerabilities which have been exposed to google search. Chose the category which you want to scan your server for , type in the hostname and, there you go, all the google dorks of that particular category are executed and results are shown. They have even added a proxy server feature, for those who are behind a firewall and can very well be used by those who want to hide their IP address.
FireCat is the second tool which again provides the same results but this time it uses the privacy services of scroogle.com. And what does scroogle does ?
An ad-free Google search proxy which prevents the searcher’s data being stored by Google, a Firefox plugin, and tools for webmasters.
Here is a small fictional story to entertain you thoroughly.
Now for a true recon tool FOCA. only one disclaimer: Use this tool on those domains for which you have authorization and this is for EDUCATIONAL purposes only. And I presume recon is done for educational purposes, right?
A small synopsis :
1: Google Dorks, Bing Dorks and other dorks, ie. numerous search engines.
2: Domain and Sub-Domain enumeration
3: Shodan search.
How to find these nifty little applications and where to download them from, how to use them ? Ahh, google comes to my rescue.
For those who want to spend their weekend on a PC doing nothing – Play Pac-Man and also read about it – the video game of the board game of the video game.