Recently launched malware called Avaddon has been actively recruiting hackers and malware distributors to spread the malware in a massive spam campaign targeting users worldwide.
In a campaign which circulated emails with a call for action subjects like, Your New Photo? Or Do you like my new photo?
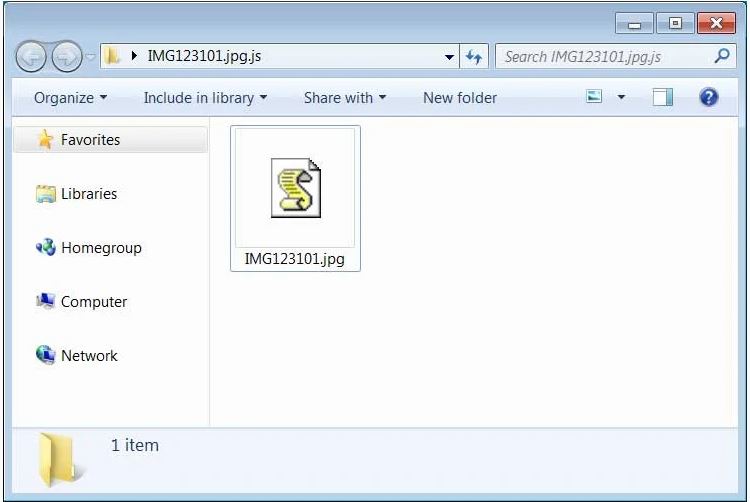
The Phorphiex/Trik Botnet is distributing these malicious emails that contain nothing but a winking smiley face and a JavaScript downloader for the Avaddon Ransomware. The Javascript attached to this email is masquerading as a .JPG file with names like IMG290620.jpg
It’s vital to understand that even though it’s a known security risk, Windows hides file extensions by default, and hence users were tricked into opening the JavaScript file.
This is how the JavaScript file would look to the recipient.
A PowerShell and Bitsadmin command both will be launched on the execution of the JavaScript attachment to download the Avaddon ransomware executable to the %Temp% folder and run it. Once executed, the ransomware will search the machine for data to encrypt and apply the .avdn extension to the encrypted files.
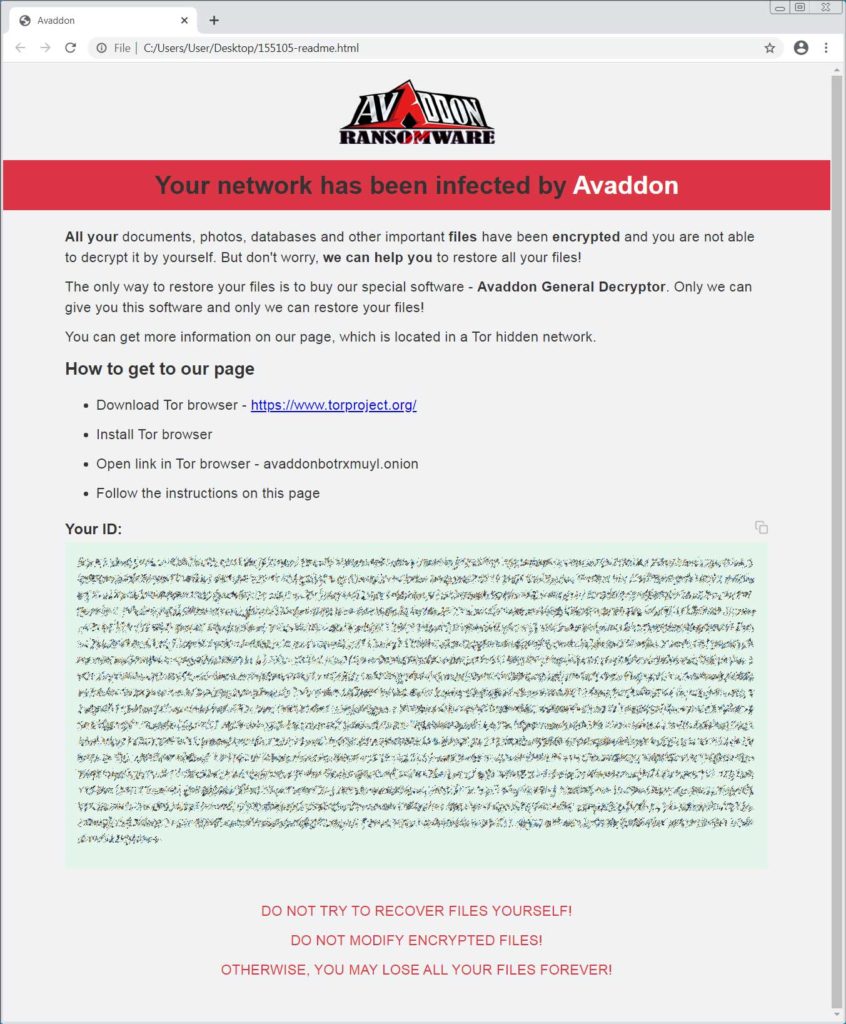
A ransom note named [id]-readme.html will be created in each folder. This note contains the link of a TOR site and very unique victim ID that is used by those specific victims to login to the site.
This payment site includes the ransomware amount, which may differ from victim to victim and instructions on how to pay for a decryptor to regain the encrypted data.
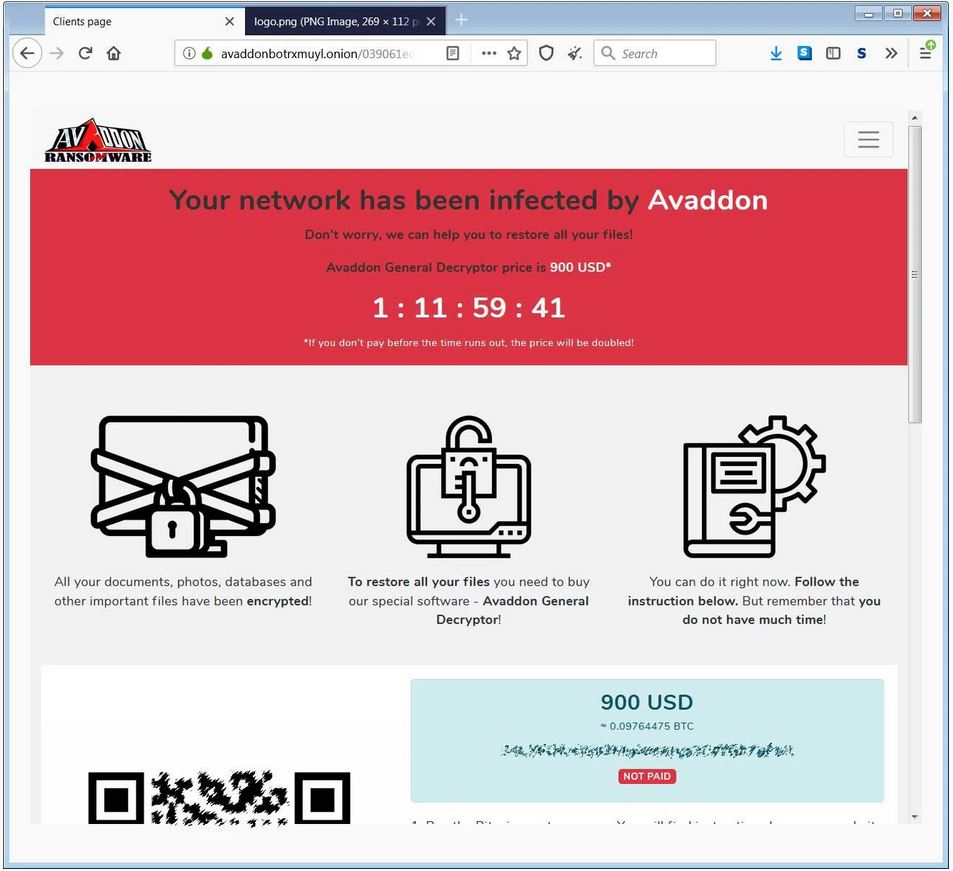
After an assessment, it has been found that the payment site is very secure and the data cannot be decrypted for free.
According to an advertisement post on a Russian hacking forum, Avvddon has been stated as a Ransomware-as-an-affiliate (RaaS) Program.
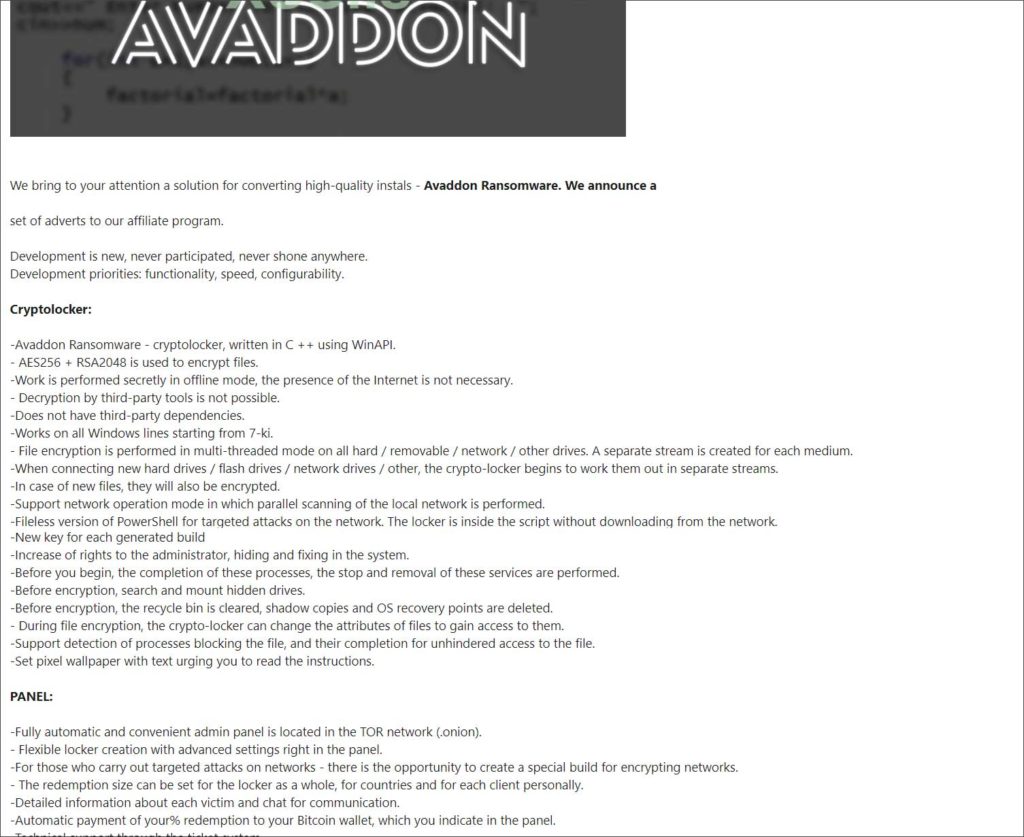
When the ransomware creator is responsible for the development of the malware and the operation of the TOR payment site, its called a RaaS Program. Any affiliates who chose to join the program are bound to spread the malware through, compromising network, exploit kits, or via spam. The affiliated would be paid 65% of the ransom payments that they bring in while the operators will receive 35%. Depending on the size of the attack, affiliates who have brought it a larger sum can negotiate a higher revenue share.
Affiliates are expected to follow a series of rules, laid out by Avaddon, the most common being that they cannot target victims in the Commonwealth of the Independent States.
The distribution of this malware is on the rise and hence our security experts suggest employing reliable cybersecurity solutions that are armed with features that can restrict the spread of this malicious ransomware.
To read more, please check eScan Blog







