To share their illicit plunder obtained from ransomware attacks targeting high profile public and private organizations Ransomware-as-a-service (RaaS) crews are actively looking for affiliates.
The stark reality of this plunder and earn lifecycle is that, the owest quality ransomware is rented, or sold, as Raas Service where the threat actors who breach the targets’ networks pay a fee to use the RaaS crew’s malware.
Private affiliate programs are run by well-known and established ransomware gangs, where affiliates can submit applications and resumes to apply for membership. The ransomware developers receive a 20-30% cut for affiliates that are accepted into the program and an affiliate gets 70-80% of the ransom payments they generate.
In order to encrypt the systems of the potential victims, affiliates will request the services of a hacker who gains access to the targets’ networks, gets domain admin privileges, harvests and exfiltrates files, and then passes all the info needed to gain access and encrypt data back to the affiliates.
The profits earned at the end of a successful ransomware campaign are then shared in equal shares between the RaaS crew, the hackers who breached the network (compromiser), and the ransomware affiliate.
Levels of Ransomware Gangs
In the present day, there are more than two dozen active ransomware-as-a-service gangs that are looking to extortion attacks to ransomware affiliates.
Furthermore, researchers have confirmed that known private gangs are operating in tight closed knit criminal circles with the use of direct and private communications channels. Based on their notoriety and the time they’ve been active, these ransomware gangs can be classified into three different tiers.
These tiers range from well-known groups that have their name tied with one or the other malicious ransomware, to newly formed variants that are inspired by old failed versions of ransomware, to completely new variants with the prowess to usurp the throne of the most malicious ransomware in the present era.
The gangs in Tier 1 – are groups who have successfully raked in hundreds of millions in ransoms over the last years. Additional extortion schemes are also used by a vast majority of them, which includes stealing sensitive information from their victims’ networks and threatening to leak it unless the ransom is paid.
The Tier 1 group includes the following RaaS crews DopplePaymer (used in attacks on Pemex, Bretagne Télécom, Newcastle University, Düsseldorf University), Egregor (Crytek, Ubisoft, Barnes & Noble), Netwalker/Mailto (Equinix, UCSF, Michigan State University, Toll Group), and REvil/Sodinokibi (Travelex, New York airport, Texas local govt).
With its payloads being detected in roughly one in three ransomware attacks during the last year, Ryuk stands at the top of the rankings.
As part of multi-stage attacks using Trickbot, Emotet, and BazarLoader infection vectors the group is also known for delivering their payloads for an easy way into their targets’ networks. Their affiliates have also been spreading malice from all quarters which is evident from the fact that they have collected a ransom of $34 million from a single victim earlier this year.
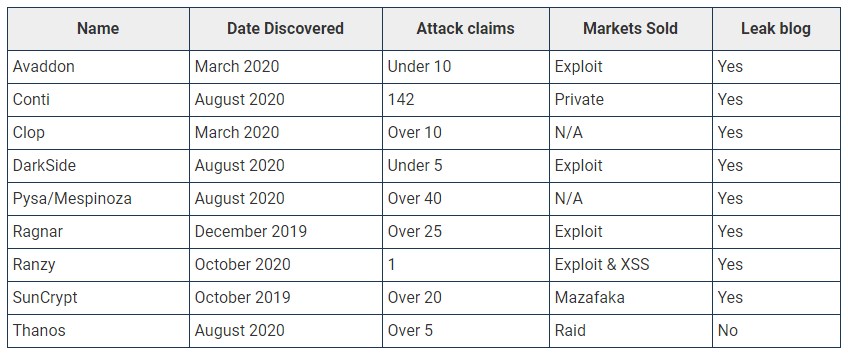
RaaS operations of Tier 2 gangs were involved in several confirmed attacks and have slowly grown to a larger number of affiliates during 2020.
Ransomware groups included in this tier are SunCrypt, Conti, Clop, Ragnar Locker, Pysa/Mespinoza, Avaddon, DarkSide (believed to be a splinter of REvil), and more.
Similar to the Tier 1 gang, data theft extortion tactic is also used by the Tier 2 gangs as a secondary extortion method.
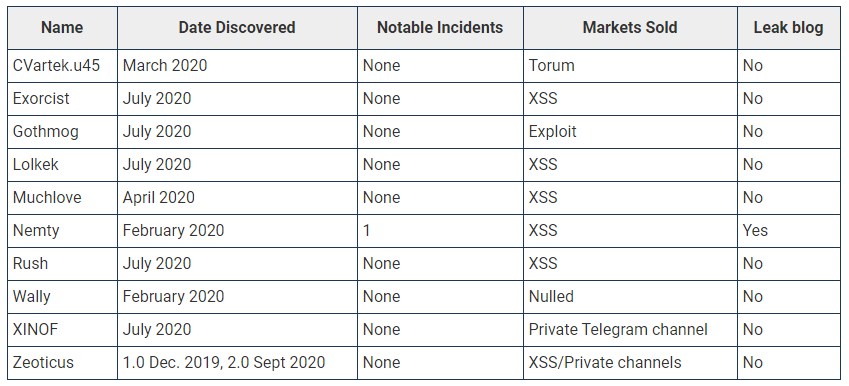
Tier 3 includes newly created affiliates of certain RaaS crews. This group includes Nemty, Wally, XINOF, Zeoticus, CVartek.u45, Muchlove, Rush, Lolkek, Gothmog, and Exorcist.
Other Groups –
Besides the above-mentioned groups, a few others are also indulging in similar activities. For example, Dharma is a long-running RaaS that has been around since 2017 and known as an offshoot of Crysis ransomware, which started operating in 2016. Dharma does not use data leak sites and there are not wide reports of data being stolen. The collection from their affiliates can range from thousands to hundreds of thousands of U.S. dollars.
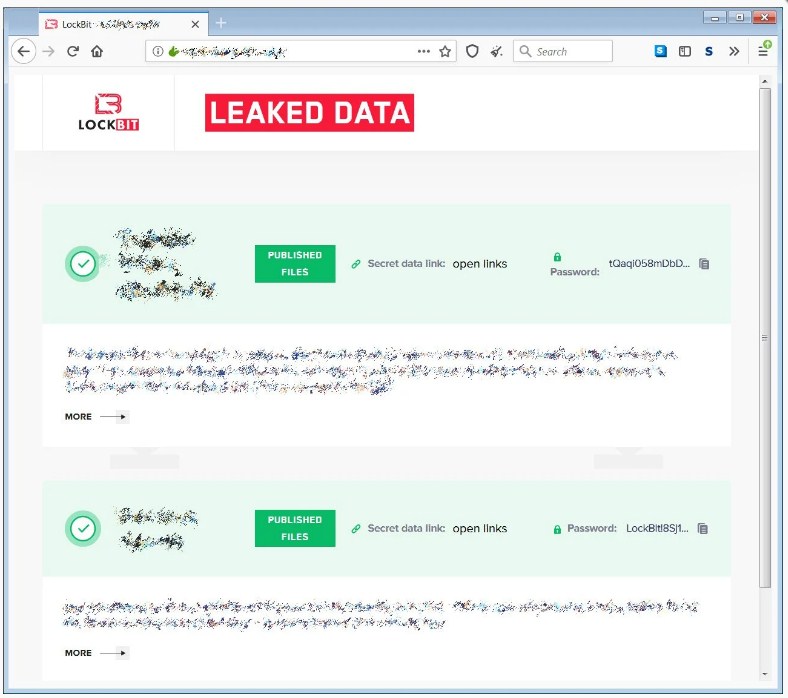
Another high-profile RaaS operation, LockBit that surfaced in September 2019 as a private operation targeting enterprises and later observed by Microsoft while used in attacks on healthcare and critical services. The LockBit gang partnered with Maze to create an extortion cartel to share the same data leak platform during attacks, as well as to exchange tactics and intelligence.
Operators of LockBit ransomware take as little as five minutes to deploy payloads after gaining access to the victim network.
Some other RaaS groups that have been recently active are Ragnarok, CryLock, ProLock, Nefilim, and Mount Locker
To read more, please check eScan Blog







