Today any enterprise, big or small, is vulnerable to ransomware attack. The possibility of a ransomware attack depends upon how attractive and important data your organization possess. Also, it is important how quickly you respond to any ransom demand. It is very critical on how vigorously enterprises keep their employees trained about phishing emails and other security factors.
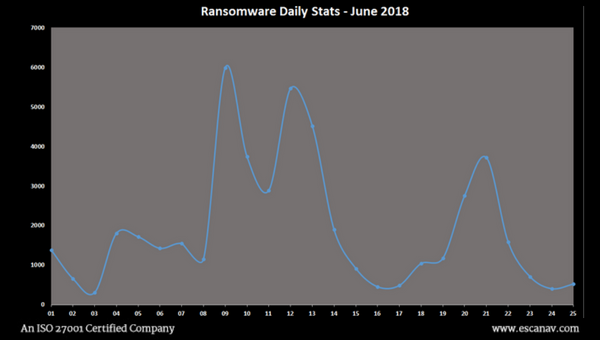
Ransomware are invading networks every now and then. The hourly and the daily record of ransomware attack gives knowledge of how frequent it is searching for vulnerable areas where it can enter for its encryption activities. There is a huge fluctuation in the entire week. This proves that any special occasion/festival does not always accelerate the possibilities and forces the organizations to take extra preventive measures round the clock to avoid any major loss.

The current threat report highlights the entire details of the kind of attacks happened in the month of June 2018. It not only gives the details of ransomware threat figures but also informs us of phishing attacks, malware URLs, and other dangerous executables. The threat parameters varied from period to period and eScan has successfully tracked it with the help of server hits.

With most of the security organizations stating that ransomware is the “biggest threat of our time,” it’s been very important to protect the organizations. What seems to be the conventional industry area of ransomware targets can surprise you with an attack in an unconventional or unexpected way. Thus taking serious means to protect data should be the best practice for any organization irrespective of size and industry.
Solutions
- Update your antivirus software on a regular basis, which will protect your system from all kinds of Malware attacks.
- Always download apps from their official website or Google Play Store instead of unknown sources because many apps store is still offering the app.
- Download applications of a reliable app developer. In addition, check the user ratings and reviews of the app before download.
- Ensure that all the software installed in your system is updated frequently, including Oracle Java and Adobe.
- Implement a three-dimensional security policy in your organization, i.e. firstly understand your requirement based on which IT Security policy would be prepared accordingly. Secondly, educate your staff about the policy and finally enforce the policy.
- Make sure you either implement MailScan at gateway level or enable Mail Anti-virus on the endpoint in order to block extensions such as *.EXE, *.SCR, *.JS, *.VBE etc. These attachments would infect your system.
- Open emails only if you are positive about the source.
- Regularly create the backup of your important files.
Be updated on our latest blog here