As businesses transform into data-driven enterprises, data technologies and strategies need to start delivering value. Here are four data analytics trends to watch in the months ahead. Together with social, mobile and cloud, analytics and associ... Read more
Web Protection: Browsing control and content filters are nothing new these days. For employers concerned with cyber security as well as employee productivity and efficiency web protection and content filters are a great idea. eScan Total Securit... Read more
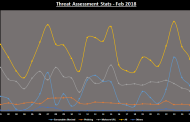
As we come to the end of the month the global statics show that it has been an unstable month with the overall threat report showing continues fluctuations. Among various threats the phishing readings have been most stable and the executable hav... Read more
A Particular Telugu character can crash any Apple iPhone, iPad Or Mac An Italian Blog Mobile World Identified a possibly severe bug that affects not only iPhone, but also a wide range of Apple devices, including iPads, Macs and Watch OS devices... Read more
Phishing also known as identity theft is a form of attack over the internet where an attacker tricks an unsuspecting individual through an email or other communication channels. The fraudster uses phishing emails to send out malicious links or a... Read more