Github Website Is Hit by the Biggest DDoS Attack (1.35 Tbs) The largest DDoS attack seen to date, occurred on Wednesday, the 28th of Feb, 2018 which was about double the magnitude of the September 2016 attack according to. Akamai, a cloud comput... Read more
DLP (Data Loss Prevention) When any media comprising sensitive data is missing and is accessed by an unauthorized person we call that a data loss. Nevertheless, a data leak is also possible without the loss of data from the source. The technolog... Read more
As businesses transform into data-driven enterprises, data technologies and strategies need to start delivering value. Here are four data analytics trends to watch in the months ahead. Together with social, mobile and cloud, analytics and associ... Read more
Web Protection: Browsing control and content filters are nothing new these days. For employers concerned with cyber security as well as employee productivity and efficiency web protection and content filters are a great idea. eScan Total Securit... Read more
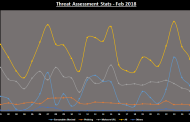
As we come to the end of the month the global statics show that it has been an unstable month with the overall threat report showing continues fluctuations. Among various threats the phishing readings have been most stable and the executable hav... Read more