Researchers have discovered the malware that was to inject backdoors in Orion platform builds during the supply-chain attack that led to the compromise of several companies and government agencies by the SolarWinds hackers.
Attackers dropped the malware in the development environment of SolarWinds’ Orion IT management software.
The malware monitors and automatically injects a Sunburst backdoor by replacing the company’s legitimate source code with malicious code, once it is executed.
From the malware’s design, it is apparent that its developers put a lot of effort to ensure the code was properly inserted and remained undetected, and prioritized operational security to avoid revealing their presence in the built environment to the developers of SolarWind.
The researchers also reveal that this is the third malware strain that has been found while investigating the SolarWinds supply-chain attack. The attack is associated and credited to the threat actor tracked as StellarParticle, UNC2452, and DarkHalo.
The second being the Sunburst backdoor malware, deployed by the same group of threat actors on the systems of organizations who installed trojanized Orion builds via the platform’s built-in automatic update mechanism.
Teardrop, the third malware was found by researchers is a previously unknown memory-only dropper and a post-exploitation tool used to deploy customized Cobalt Strike beacons.
A fourth malware called, SuperNova was also found which is not linked to the developers of the SolarWinds hackers by a different set of researchers while investigating the attacks. This malware was deployed as a DLL file that allowed attackers to remotely send, compile, and execute C# code on compromised machines.
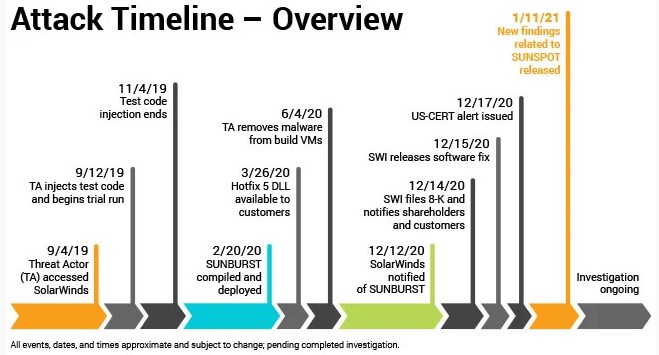
The world first learned about SolarWinds cyberattacks and its consequences by the 8th of December. It was also revealed that the attack was carried out by a nation-state hacking group.
The hackers gained access to the SolarWinds Orion build system and injected the sunburst backdoor into a legitimate DLL used by the SolarWinds Orion IT management software as a part of the attack.
Even though the identity of the hackers behind the SolarWinds attack remains to be unknown connections between the SolarWinds hackers and a previously known cyber-espionage group have been found after it was revealed that the Sunburst backdoor has feature overlaps with Kazuar, a .NET backdoor tentatively linked to the Russian Turla hacking group.
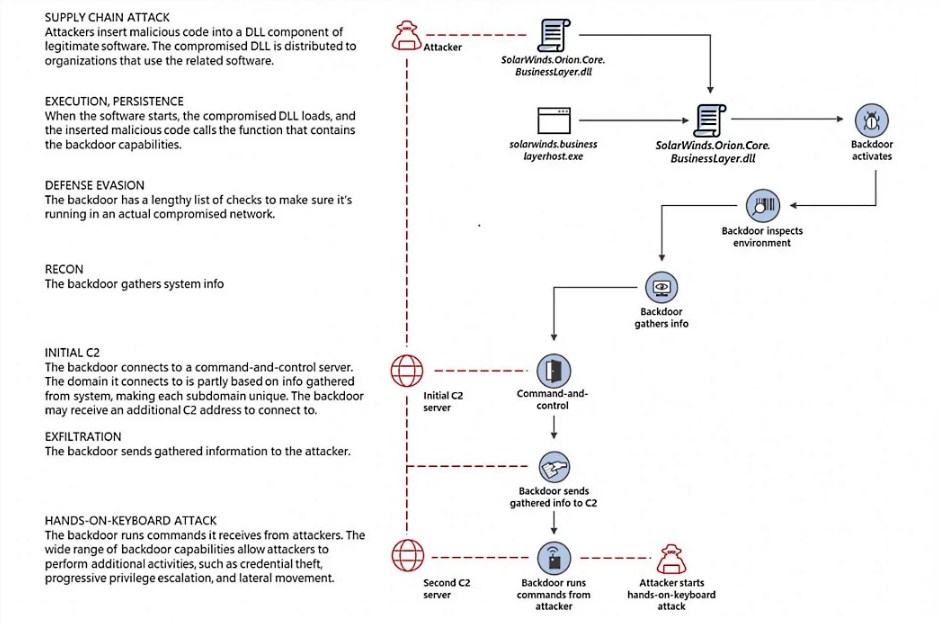
Later, a joint statement was issued by the FBI, CISA, and the NSA stating that a Russian-backed Advanced Persistent Threat (APT) group is likely behind the SolarWind Attack.
To read more, please check eScan Blog







