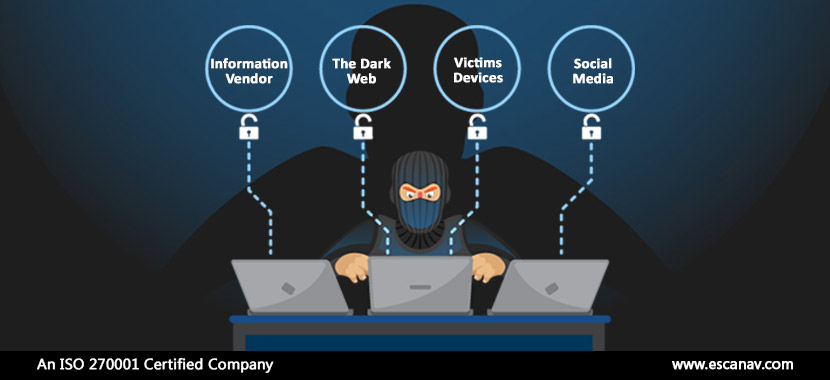
Since the advent of the Internet, Hackers and criminals have been terrorizing online users and various businesses in some or the other way. Since times immemorial, hackers have taken advantage of the digitally challenged people and businesses. For financial gains, they usually target anyone whom they perceive to be weak. Most of the times, they target the non-technical masses and while sometimes multinational companies also end up in their traps. So how do hackers target potential victims?
Information Vendors
Information vendors have become a very important cog in the marketing wheel as they collate a lot of personal information from various sources and then sell it for a stipulated sum, which is usually on the higher end of the economic spectrum. However, this source of information is not only useful for Marketers but for Hackers as well. With access to such rich data pools, cybercriminals can decide on where they want to strike next. For example, one’s banking records could help the hacker decide on how much he can profit? Should he decide to infect one’s computer via some ransomware?
The Dark Web
The Dark web is an online space that exists within plain sight and gets millions of visitors from across the globe, every single day. The dark web consists of pages that are not readable by modern-day search engines while allowing hackers to purchase stolen goods and data while still maintaining their anonymous status. Stolen data from the dark web consist of sensitive information such as credit card information and more. With such information easily accessible to hackers, they can go online and either starts draining one’s bank account or commits identity theft.
Social Media
One of the uncontrollable demerits of social media is that users tend to share so much more personal information that they are expected to, disregarding their own privacy. With merely the use of hashtags, on certain social media platforms, hackers can get information like what car one drives, where does one reside and where they travel for a holiday. This would help the hackers to segregate the list of their victims according to the ransom they can afford to pay. Gathering attention on social media can turn to be backbiting as it’s the number one place for hackers to go fishing these days.
Solution
Knowing such sensitive information about their potential victims from the above-mentioned sources makes it easy for hackers to carry out a cyber-attack successfully. However, what hackers despise the most is a user who has ample knowledge on how to strengthen the security of his systems, with a potent antivirus program. Having a highly equipped & trusted antivirus like eScan, installed on one’s interconnected devices not only gives an extra layer of protection but also acts as a repellent to cybercriminals. Given the increased protection a hacker tends to opt for a weaker user than one who is protected with an antivirus.
To read more, please check eScan Blog