To stay one step ahead of the security companies who have been the eternal nemesis of the threat actors from cyberspace, they chose to evolve their tactics. With a new variation to each tactic they use, they become less predictable. An exhibition to this pernicious prowess of the hackers was seen when they hid malicious credit card stealing scripts in the EXIF (Exchangeable Image File Format) data of a favicon image to avoid exposure.
The most common method of attack is to hack a website and inject malevolent JavaScripts that are capable of stealing any payment information submitted by users while making an online purchase.
This information is sent back to a server that is controlled by the threat actor where it is accumulated to be used by the threat actors themselves or to sell on the dark web criminal markets.
Such attacks have been executed against well-known organizations like Tupperware and British Airways. This type of attack is called a Magecart.
In a recent discovery, researchers found that an online store using the WordPress woo-commerce plugin was infected with Magecart script in an attempt to steal their customer’s credit card information. The reason that this attack stood out, was because the malicious scripts that were used to execute this attack were not hidden within the site rather in the EXIF data for a remote site’s favicon image.
This mode of attack is surely not new but this was the first time it was used alongside a credit card skimmer.
As we know, a lot of information gets stored on an image when it is created. The creator of these images can choose to embed information like who created the image, information about the camera, copyrights of the picture, and even the location where the picture was clicked within the image. This stored data is called the EXIF – Exchangeable Image File Format data.
In such an attack, the threat actors add a simple script to the website that inserts a remote favicon image and does some minute processing. After further analysis, it was discovered that a malicious JavaScript was hidden in favicon that appeared to be harmless. The EXIF data of the favicon is displayed below.
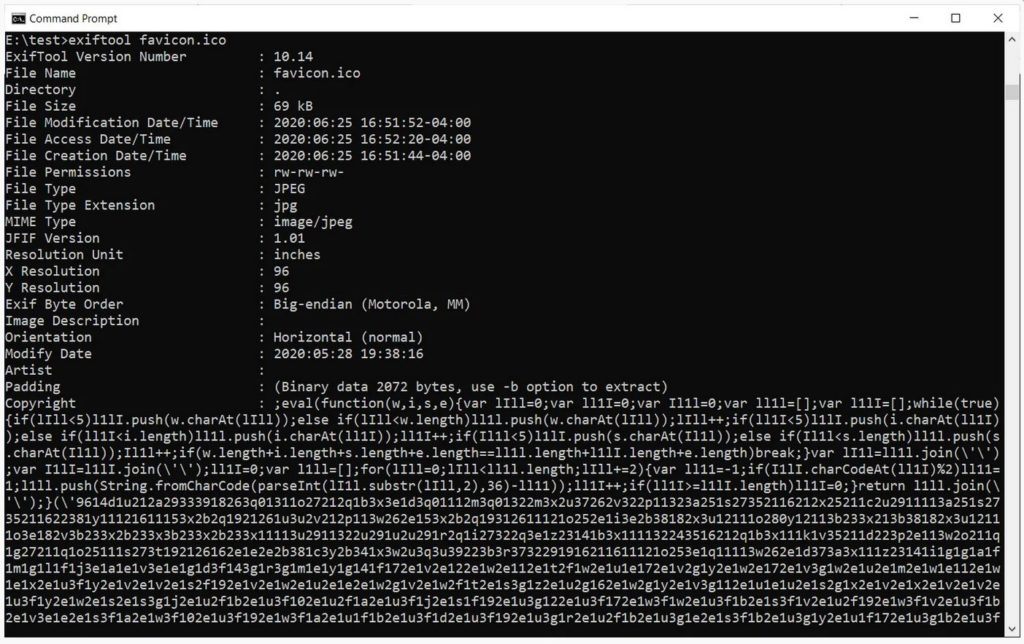
Once these malevolent scripts were loaded, any information that a user would submit during the payment process would be reported back to the threat actors where they would collect it at their leisure.
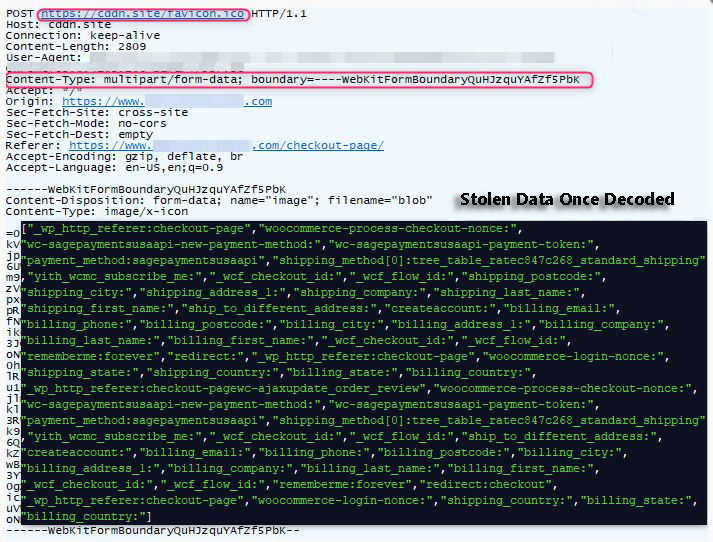
It is highly difficult for some security software or various developers to notice that something might be amiss since these malicious card stealing scripts are not located on the hacked site itself.
These attacks were linked to a threat actor group known as Magecart 9. This group has been credited with other techniques such as the use of web sockets to evade detection.
To read more, please check eScan Blog







