By creating new ransomware called WastedLocker, the notorious Evil Corp has ended its brief hiatus and is back to torment the enterprise arena with targeted ransomware attacks. The group is also credited with the creation of BitPaymer ransomware, which was delivered through the Dridex malware in targeted attacks against the corporate world. The operators of this ransomware is also known as Indrik Spider had started as an affiliate for the Zeus Botnet.
After two of its members were indicted, Evil Corp reconstructed its tactics and as a part of it, they have been distributing the WastedLocker ransomware.
To attack an organization, threat actors hack into websites and inserts malicious code that displays a fake software update from the SocGholish fake update framework. The Cobalt Strike penetration testing and post-exploitation toolkit are one of the payloads used in these attacks to gain access to the infected device. The ransomware operators utilize this access to further compromise the network and deploy the ransomware. So far, these attacks do not appear to be stealing the data before encrypting files.
The Wasted locker ransomware picks up a random EXE or DLL when launched from the C:\Windows\System32 and uses that file to create a new file altogether without an extension under the %AppData% folder
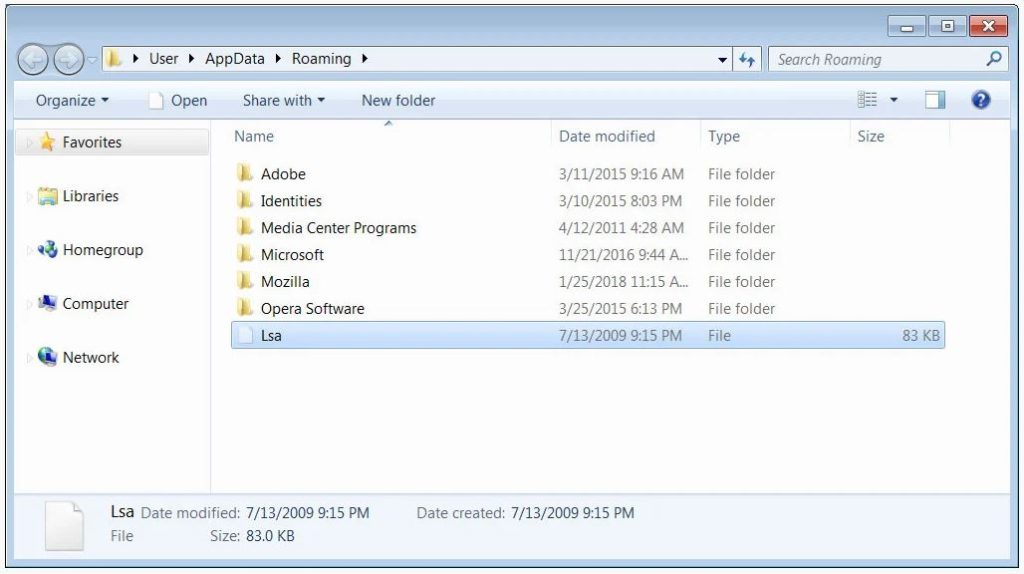
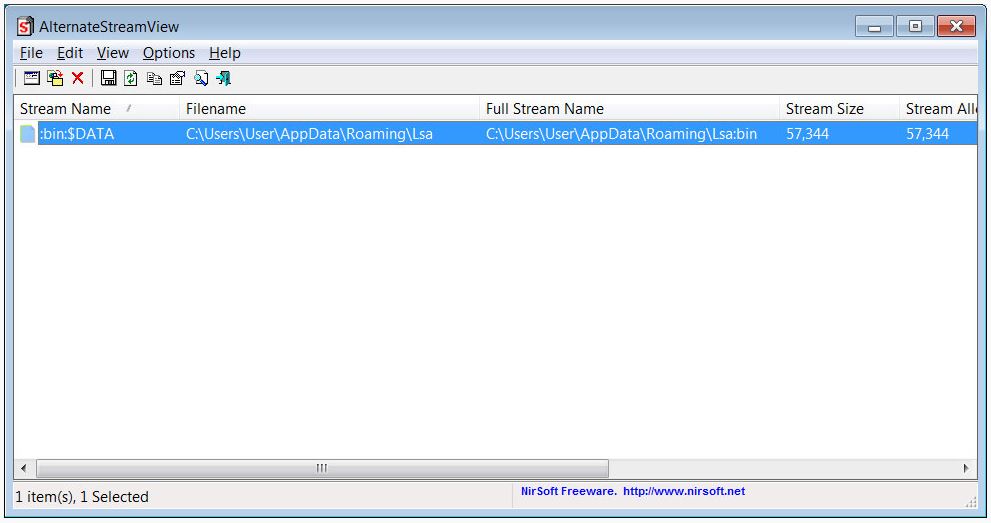
An alternative data stream named “Bin” is attached to this file, which will then be executed.
Apart from some files in specific folders or containing certain extensions, the ransomware attempts to encrypt all drives on an infected computer. Given these attacks are targeted, the ransomware is built to target a specific organization. As a part of this customization, the ransomware combines the “wasted” string and the initials of the company to generate a new and unique extension that is appended to the victim’s encrypted data.
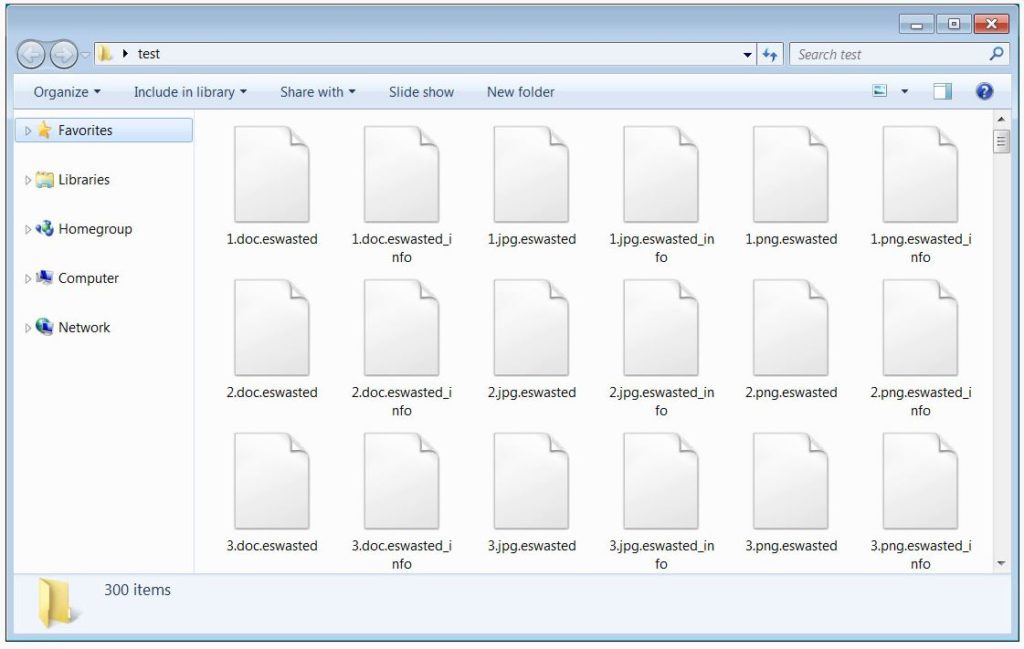
The WastedLocker ransomware also creates an accompanying ransomware note ending with _info, for every file that gets encrypted.
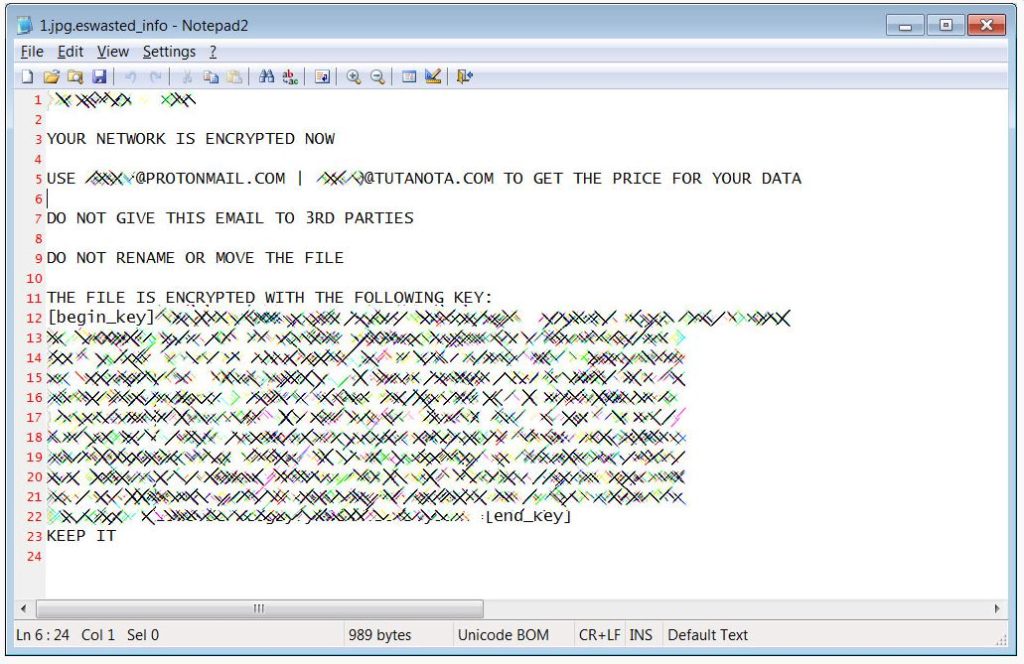
This tactic stands out for being very strange as no program can open it by default as compared to the ransom note using the .txt extension. This ransom note contains instructions to contact its operators via both their protonmail.com and tutanota.com email addresses.
With no way to decrypt the files, WastedLocker Ransomware appears to be secure at this point in time. Its ransom demands range from $500,000 to a million dollars.
To read more, please check eScan Blog






