After its recent awakening, Emotet is now once again installing the TrickBot trojan on infected Windows computers and has started to send spam worldwide.
After nearly five months of inactivity, Emotet botnet appears to have woken up and has started a massive spam campaign pretending to be payment reports, invoices, shipping information, and employment opportunities.
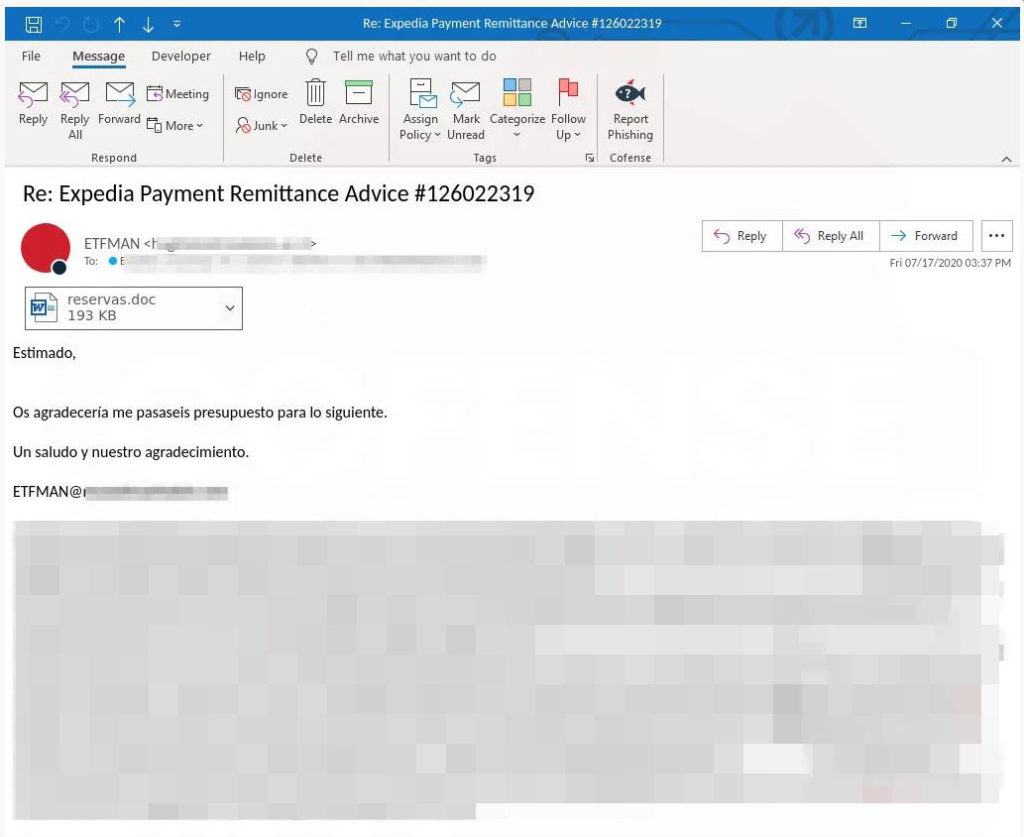
It has been noticed that the latest Emotet campaign has been running since the 17th of July 2020 and it has also been observed to be distributing Trickbot since 20th of July 2020. This has been a massive spam campaign launched by the Emotet operators. According to this campaign, Windows machines are infected with Emotet, which eventually downloads the Trickbot Malware.
TrickBot opens up a reverse shell to the Ryuk and Conti Ransomware actors after harvesting all the valuable data. The collaboration with the Ryuk ransomware actors could allow them to access the network, steal unencrypted files, and encrypt the entire network.
Trickbot has been usually seen targeting enterprise networks.
Some of its malicious activities include –
- Attempting to spread laterally through a network
- Steal Active directory services database
- Harvest login credentials and cookies from browsers
- Steal open SSH keys
- Steal RDP, VNC, and Putty credentials
- Steals banking credentials
Emotet – Trickbot Partnership
Trickbot has been distributed by the Emotet botnet since early October 2018, and it had been operational till the start of the COVID-19 era.
In an attempt to bypass security software that uses artificial intelligence and machine learning to detect malware, the TrickBot and Emotet trojans were found adding text from Coronavirus news stories in March 2020. Earlier in the year, an Emotet SMiShing campaign was also observed using fake bank domains, which is assumed to be a targeted campaign for distributing TrickBot trojan.
The Troika of Terror
In April last year, a unique concoction of Emotet and TrickBot, as well as the nascent Ryuk ransomware was found targeting European and American companies with a one of its kind malicious campaign.
As we have previously mentioned in our blog, Ryuk and Conti share similarities in the malware code. So, it is believed that Conti ransomware is connected to the same Ryuk ransomware developer group based on the code reuse and unique TrickBot distribution.
Expert Advice on the Emotet Trickbot Campaign
Network and security administrators need to be sure users on their network are educated adequately on Emotet spam campaigns and not open any suspicious documents. Furthermore, if a computer becomes infected by Emotet, likely, they are also infected by TrickBot. Hence, a complete investigation should be launched, which includes assessing whether the infections have spread to other computers on the network.
To read more, please check eScan Blog







