A novel phishing toolkit has been developed by a cybercriminal gang that changes logos and text on a phishing page in real-time to adapt to targeted victims.
The phishing tool named LogoKit, is already deployed in the wild according to a team of researchers that has been tracking its evolution. They further added that they have already identified LogoKit installs on more than 300 domains and more than 700 sites over the past few months.
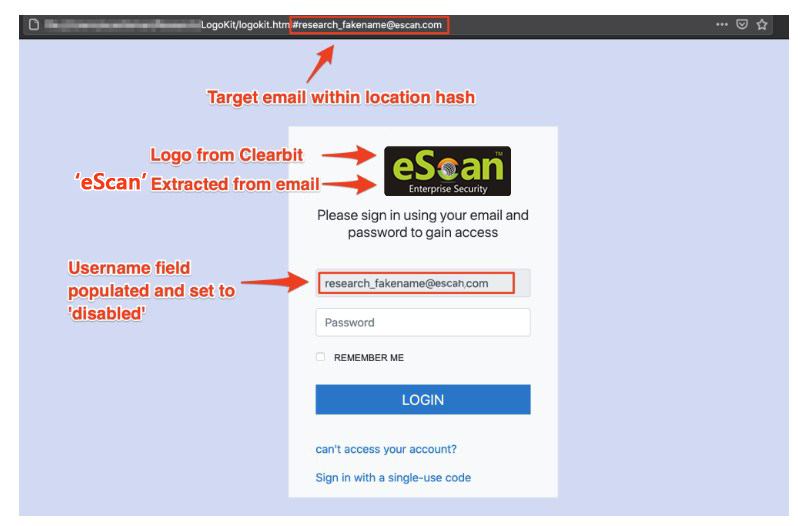
LogoKit relies on sending users phishing links that contain their email addresses.
LogoKit fetches the company logo from a third-party service, such as Clearbit or Google’s favicon database, once the victim navigates to the URL. In an attempt to trick the victims into believing that they have previously logged into the site, the victim’s username or email is auto-filled into the given field.
LogoKit performs an AJAX request, sending the target’s email and password to an external source, should the victim enter their password and then redirects the user to their corporate web site.
<Image>
LogoKit achieves this only with an embeddable set of JavaScript functions.
Standard phishing kits need pixel-perfect templates mimicking a company’s authentication pages which are different from LogoKit’s prowess. The operators of Logokit allow them to target any company they want with very little customization work through the modularity of the kit and hence enable them to mount tens or hundreds of attacks a week against a wide-ranging set of targets.
Researchers have seen LogoKit being used to mimic and create login pages for services ranging from generic login portals to false SharePoint portals, Adobe Document Cloud, OneDrive, Office 365, and several cryptocurrency exchanges.
The phishing kit doesn’t always need its own complex server setup, since it is so small, unlike other phishing kits. For the companies LogoKit operators want to target, the kit needs to be hosted on hacked sites or legitimate pages of those companies.
LogoKit’s resources can also be hosted on public trusted services like Firebase, GitHub, Oracle Cloud, and others since LogoKit is a collection of JavaScript files and most of which will be whitelisted inside corporate environments and trigger little alerts when loaded inside an employee’s browser.
It is believed that the Logo kit improves the chances of a successful phish.
To read more, please check eScan Blog







