CSAM: Vulnerability vs Risk:
Let’s take a review of our online safety practices in this October, which we know as “Cyber Security Awareness Month” (CSAM). Today cybersecurity is a major concern of the entire world and we can secure our digital assets by following some simple basic steps.
1. Protect your accounts’ identity with separate usernames and passwords.
2. Turn on the firewall which is the first line of defense.
3. Use anti-virus software to prevent malware attack and update it regularly.
4. Prevent spyware attacks by installing anti-spyware software.
5. Install the latest OS updates
6. Take your file back-ups regularly
7. Secure your Wi-Fi from intruders
8. Ignore emails from unknown senders and never open those emails
9. Be careful while sharing personal information online
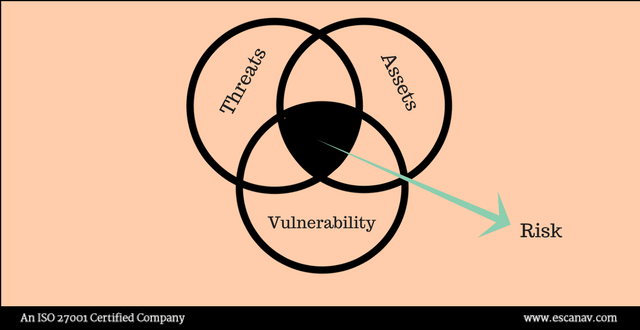
Interestingly, in this (CSAM) awareness month, IT professionals are now brainstorming with a comparative analysis of vulnerability and risk factor in IT security industry. The vulnerability is a weakness in any system/ application which can be violated without any context involved in the impact. On the other hand, a risk is considered as something more than just known vulnerabilities and where any action could result in an impact.
Risk again is independent of vulnerability and enterprises do have risks even if there are no vulnerabilities apparently. If we consider a scenario of a phishing scam, the risk factor lies in opening the spam and the system vulnerability is exploited because of that risk was taken.
Keep fear and emotion aside
We should never forget that security is a service we should be providing, and if any threat snarls, the security professionals should identify the nature and circumstance from where the threat appears. Managing risk is about distinguishing between probability and possibility. Once this distinction is figured out, then actually we can have an itemized list of the risk factors – be it in the network or the system.
Managing Risk
Obviously, there is no golden rule to get through the list of security vulnerabilities, particularly when multiple issues are added to the list before existing ones are resolved. Managing risk is all about being aware of the existing data that you have, why you have it, and how it is stored. Besides, another crucial part of managing risk is to make sure that there is no conversation about risk across the organization.
Lastly, security practitioners should be able to convey the actual risks in such a way that would enable them to build a robust security posture. The data compromise can be inevitable since that is the reality of the digital transformation.
Read more – Blog eScan