Even though Bluetooth is one of the most underrated features of modern-day mobile phones, yet seldom we find a phone that lacks this feature even today. Bluetooth is a short-range wireless connection feature that’s an integral element of modern-day cellphones. However, just like every other evolving cellular technology finds itself in the cybercriminals crosshairs, Bluetooth technology has also been a target of hack attacks every now and then.
Cybercriminals have tried to exploit handheld devices to fulfill their nefarious objectives with attacks like BlueBorne, KNOB, and BadBlueTooth. Another recent Bluetooth vulnerability that can be added to this list is BlueRepli.
At a recent virtual event, two new Bluetooth attacks were revealed by researchers.
One of the attacks is dubbed BlueRepli. According to researchers, an attacker can bypass Bluetooth authentication on Android devices without detection or requiring any user input, with the use of Bluerepli attack. It is possible to steal sensitive data from an Android device, including call records, contacts, and SMS verification codes. Moreover, attackers can send fake SMS messages to the user’s contacts through this attack.
Researchers also demonstrated how attackers can abuse the Bluetooth feature to steal the entire Phone Book and SMS messages from their targeted device. With the help of BlueRepli, attackers can bypass authentication by merely imitating as a device that was previously connected with the targeted device. No permissions from the users are required by this attack for the exploit to work.
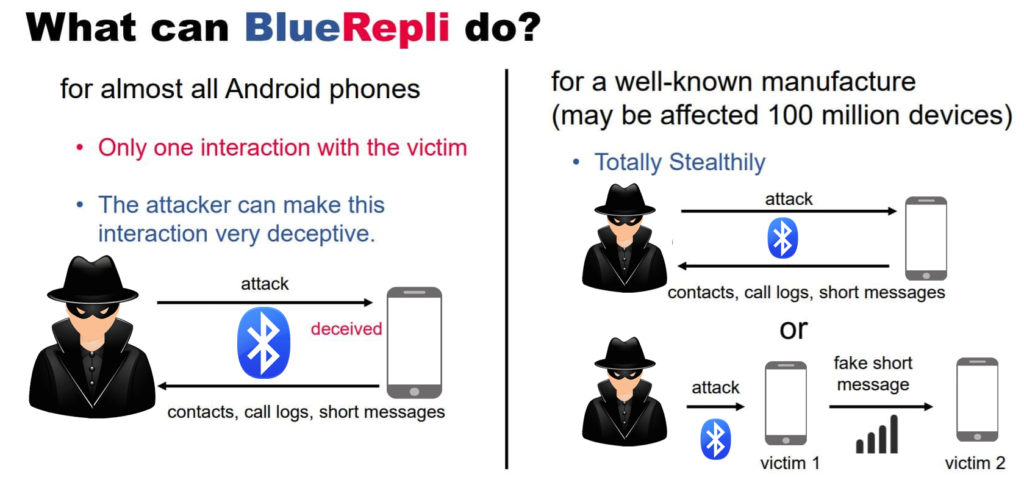
As for the other attack, researchers discovered that attackers have to target Bluetooth protocols. To request permissions that let one Bluetooth device share data with another device, attackers can disguise as a trusted application, such as a vehicle’s infotainment system.
In a scenario where when both the devices have their Bluetooth enabled only then attack can be successful and the victim needs to approve the attacker’s request for privilege escalation.
It is also noted that these attacks do not work on iOS devices. The same set of researchers also revealed that this zero-day vulnerability results from negligence at part of a particular mobile phone manufacturer, which has made around 100 million Android devices and some inherent security risks in the Android Open Source Project (AOSP).
Even after the researchers reported the Bluetooth vulnerability, to both Google and ASOP, yet it surprisingly persists. A spokesperson from Google stated that the company is still developing a patch to fix these issues.
To read more, please check eScan Blog