The future is completely open, and the Internet of Things is no different. Our daily routines and work have been completely digitized thanks to the Internet of Things. The Internet of Things is not just used to entertain us but also to keep track of our workouts and fitness routines. 5G wireless technology is touted as the “next generation” of wireless technology for our homes. In addition to providing a faster connection for IoT devices, 5G wireless technology also introduces new security risks. In this blog, we discuss the vulnerabilities of 5G with IoT devices and how improved cybersecurity can facilitate a safe future for 5G.
What exactly is 5G? What are its Defining Features?
Wireless networks of the 5th generation are designed to integrate machine learning, the internet of things (IoT), and other IoT technologies seamlessly. It is also known as wifi-LTE and has much faster speeds than 4G. As a result of 5G, many new features will be available, including:
- Latency reduction: Providing latency as low as 1 millisecond
- Density of Connections: Allowing 10x more effective networking for IoT devices.
- Throughput: Delivering consistent multi-Gbps peak rates
- Reduced power consumption: Making network operations more efficient in order to maximize energy consumption.
- Greater capacity: Increasing network density by adding more cells everywhere.
Capabilities of 5G
- Sensor technology is being integrated into new machinery to monitor its vital systems, allowing us to slow or stop and restart other potential problems before they occur.
- IoT can be used on farms to increase agricultural yields, reduce pollution, and work more efficiently.
- Vehicle automation systems exchange data between areas to avoid collisions on the road.
- The most successful IoT product will be a seamless combination of sensors that detect natural disasters and can warn users before they happen.
- 5 G-enabled drones are quickly becoming an important tool for providing an extra layer of support for emergency response.
Internet of Things (IoT)
The Internet of Things (IoT) refers to an expanding network of sensors, physical objects, and the technology embedded within them that allows these objects to communicate with one another over the internet. There are high expectations in this area, with no less than 22 billion devices expected by 2025.
Why is IoT so Significant?
IoT has emerged as one of the most significant industries in recent years. Everything, from kitchen appliances to cars to medical instruments, is linked to the internet via embedded devices, which means that business people can communicate seamlessly between people, processes, and things with the assistance of a strong and dependable 5G network
One critical way that IoT assists people is by enabling the seamless connection of everyday objects, people, and processes. Assume you have an app on your phone that is linked to your car’s “black box.” The app may tell you when to get your car serviced or allow you to compare your driving patterns with other similar drivers based on the data recorded by your car’s system.
5G networks are more vulnerable to cyberattacks than previous generations of mobile networks. Here are some of the key factors that could become potential risks:
- IoT device Attack Surface:
Memory, firmware (a tiny computer-within-a-computer), physical interfaces, network interfaces, and even the software installed are common weak points in IoT devices. Devices can also be compromised if their internal contents are out of date.
Attacks may originate in the channels that connect IoT components. Existing network protocol issues, such as DDoS attacks and spoofing, may affect entire IoT systems in their current state.
- Insufficient Secure Authentication in IoT Devices:
The widespread issue is that all devices of a given model are shipped from the factory with the same default user name/password combination. This means that if the consumer does not change their credentials, they will be able to access all devices of that model.
Voice commands and facial recognition can also be spoofing in IoT devices by using recorded/generated voices and images of people.
- Botnet Attacks:
An army of internet-connected devices masquerading as one is typically assembled to carry out attacks or other types of supporting tasks. This type of network is known as a botnet, and IoT devices are constantly vulnerable to botnet attacks due to a lack of secure authentication and encryption.
- Distributed Denial-of-Service (DDoS):
Bots, unlike regular internet devices linked to a web server, can request and gain access to IoT devices on their own or on behalf of others. Attackers can generate more traffic and dominate the targeted machine by flooding a system with multiple bot requests at the same time.
- Man-in-the-Middle (MiTM):
A ‘Man-in-the-Middle’ (MitM) attack occurs when a third party intercepts IoT devices or communication channels. In this attack, an attacker secretly accesses the channel and alternates data between two endpoints without either party being aware. This occurs when IoT devices communicate over unencrypted channels or protocols.
A Summary of the Potential Risks:
- Previously, networks were built using centralised hardware-based switches. They are now built with digital architectures that transfer data between devices. Because there are no choke points in this distributed structure, it is much more difficult to control threats that could previously launch a DDoS attack or cause a network outage.
- The network is a complex interconnected system of devices, software, and services. The new smart home trend and vendors are increasingly moving toward software-based solutions for their physical appliances, resulting in more security holes and cyber vulnerability.
- Regardless of the security of your network, every 5G device is managed by software. This means that, while the devices are vulnerable to a variety of threats, they are also vulnerable to an internal threat – an attacker with control over the software that manages the network!
- The rapid expansion of a network’s ability to carry traffic from heavy user traffic in 5G creates additional attack vectors for hackers to exploit.
The increased visibility provided by the Internet of Things presents a tempting opportunity for hackers to prey on companies that are unable to effectively implement security practises and procedures.
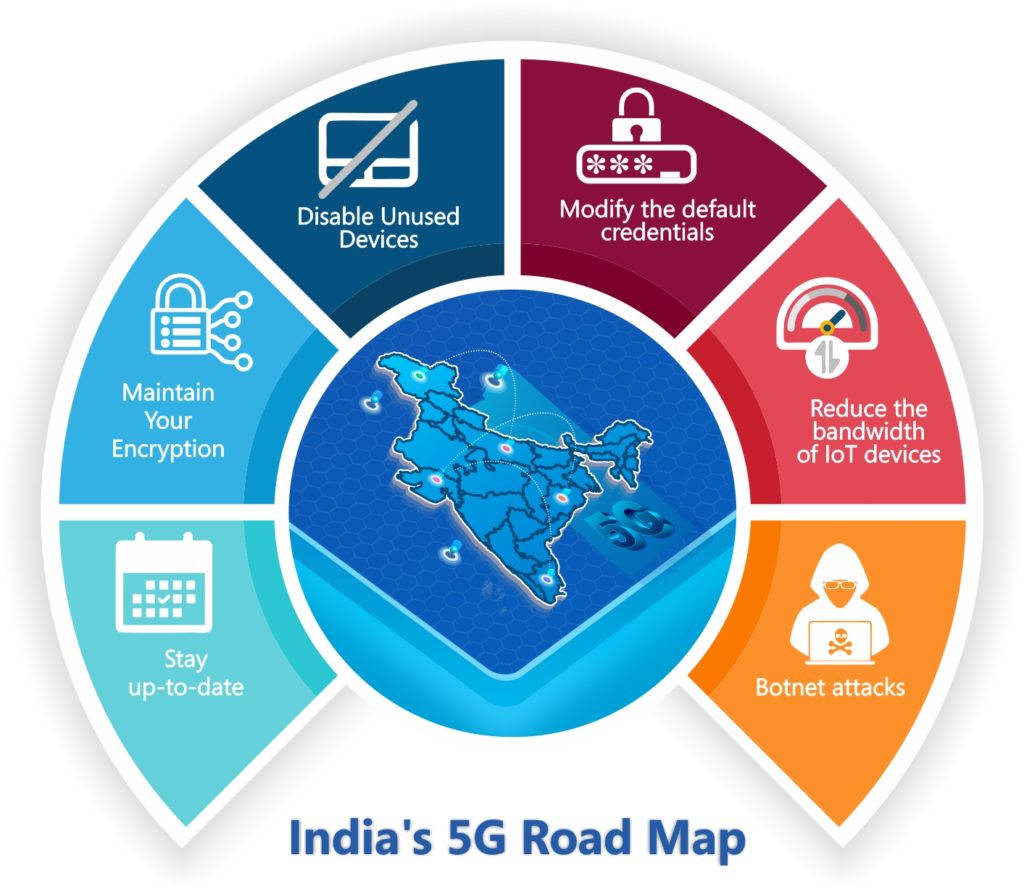
Best Practises for Securing IoT Devices
- Stay up-to-date: We recommend keeping your IoT device(s) updated whenever possible to ensure that they are always up to date with the latest software updates and fixes.
- Maintain Your Encryption: Hackers can use IoT devices to launch attacks. Encrypting your data is one of the most effective ways to safeguard it.
- Disable unused devices: It is critical to reduce the potential attack surface. In other words, new electronic devices and connected home appliances can be ignored all at once while still posing a significant threat. Take the time to identify every piece of network equipment, even if you’ve never used it before, and make sure your network security is tight.
- Modify the default credentials: Users must ensure that they change or create secure passwords for accessing their IoT devices.
- Reduce the bandwidth of IoT devices: When operating Internet of Things (IoT) devices, consider implementing security measures such as limiting the network traffic generated by IoT devices.
5G will be available in the four major cities and other metropolitan areas in 2023, according to the Department of Telecommunications (DoT). Before rolling out 5G across India, the department plans to hold 5G spectrum auctions.
Trials for 5G services have been conducted in several major cities with the assistance of well-known companies such as Bharti Airtel, Reliance Jio, and Vodafone Idea.
To begin, the most important ingredient will be clarity on some regulatory decisions. To make the spectrum legally accessible and initially available for use, it must be licenced to eligible parties. Creating a fair and reasonable process for issuing said licences can contribute to the fundamental building blocks required for the project’s success. There has been a lot of discussion about how expensive it is to gain access to the spectrum.
As soon as the regulatory dust settles, 5G will be available. Smartphones and mobile carriers are both ready to go. Before 5G becomes ubiquitous, specific terms and conditions must be clarified.
The government designated a portion of the spectrum for public and private networks ranging from 526 MHz to 698 MHz, 700 MHz, 800 MHz, 900 MHz, 1800 MHz, 2100 MHz, 2300 MHz, 2500 MHz, 3300-3670 MHz, and 24.25-28.5 GHz. In the Industry 4.0 concept, private 5G networks are reserved for captive use. When introduced to the world, it is billed as a significant application of 5G networks. Not only will public 5G networks serve all telecom users, but private networks will also be integrated into the Internet of Things. With all devices connected to work together via this latest version of the internet, it will be more efficient and safer than ever before.




