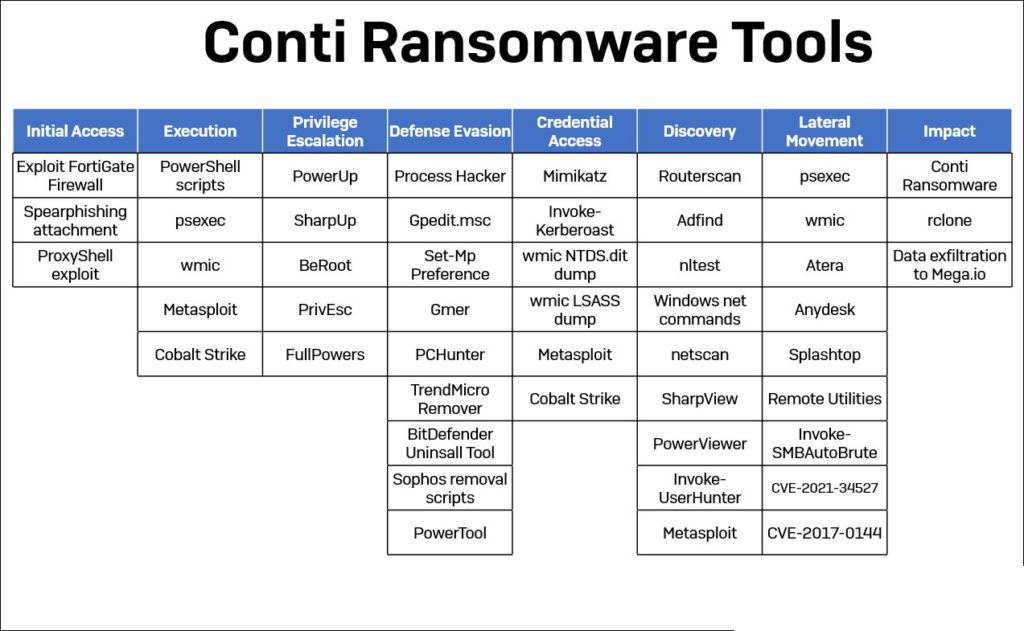
Using previously published ProxyShell vulnerability exploits, the Conti ransomware group is hacking into Microsoft Exchange servers and compromising corporate networks.
ProxyShell is a name for an exploit that uses three chained Microsoft Exchange vulnerabilities (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207) to allow unauthenticated, remote code execution on susceptible servers that haven’t been patched.
These three flaws were found by a Taiwanese student working with a Taiwanese security consultant, who utilized them in the consultant’s hacking contest.
While Microsoft fully addressed these flaws in May 2021, detailed information on how to exploit them was recently revealed, allowing threat actors to begin leveraging them in attacks.
Threat actors have used the ProxyShell vulnerabilities to distribute webshells, backdoors, and the LockFile ransomware so far.
Conti is now breaking into networks with ProxyShell.
A team of researchers from a security firm were recently involved in an incident response case involving the Conti ransomware group encrypting a company.
The threat actors initially penetrated the network utilizing the recently publicized Microsoft Exchange ProxyShell vulnerabilities, the researchers observed after reviewing the attack.
Threat actors, as in most recent Microsoft Exchange attacks, drop web shells that can be used to run commands, download malware, and further compromise the server.
Researchers noticed that once the threat actors had complete control of the server, they swiftly reverted to their regular strategies, which were specified in the previously disclosed Conti training material.
Obtaining lists of domain admins and computers, dumping LSASS to obtain access to administrator credentials, and moving laterally over the network to other servers are all part of this procedure.
Threat actors would hack numerous servers and install multiple tools, such as AnyDesk and Cobalt Strike beacons, to allow remote access to the devices.
The threat actors took unencrypted material and uploaded it to the MEGA file sharing server after acquiring a foothold on the network. They started encrypting devices on the network from a server with no antivirus protection after five days, using the following command:
start C:\x64.exe -m -net -size 10 -nomutex -p \\[computer Active Directory name]\C$
The speed and precision with which the group carried out the attack, which took only 48 hours from the initial breach to the theft of 1 TB of data, made this instance stand out.
“The attackers had exfiltrated around 1 Terabyte of data within 48 hours of acquiring first access. They distributed the Conti ransomware to every system on the network after five days, explicitly targeting individual network shares on each device “in their study, the researchers noted.
“The Conti affiliates placed seven back doors on the network during the intrusion: two web shells, Cobalt Strike, and four commercial remote access programs (AnyDesk, Atera, Splashtop, and Remote Utilities).”
“The early web shells were mostly utilized for initial access; Cobalt Strike and Any Desk were the primary tools they employed for the rest of the attack.”
Now is the time to patch your Exchange servers!
When employing ProxyShell to launch an attack, the threat actors make queries to the auto-discover service that looks like this:
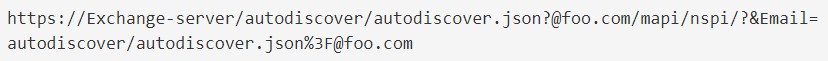
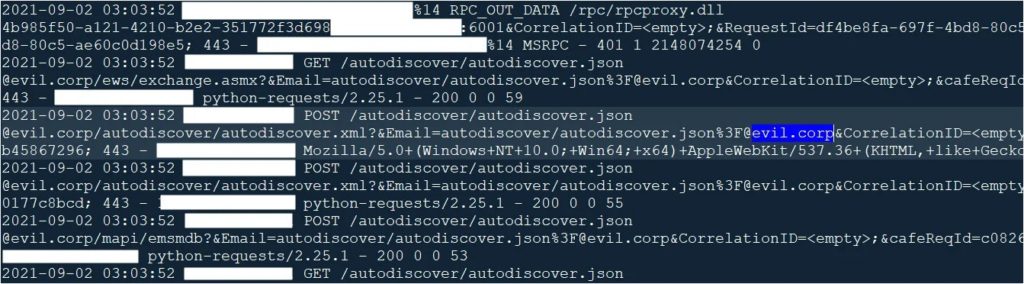
You can examine IIS logs for requests to “/autodiscover/autodiscover.json” with strange or unknown emails, to check if your Exchange Server has been targeted.
The threat actors in the Conti case, according to the researchers, used an email from @evil.corp, which should readily make the exploit attempts stand out.
Without a doubt, the ProxyShell vulnerabilities are currently being exploited by a wide spectrum of threat actors, and all Microsoft Exchange server administrators should install the most recent cumulative patches to stay safe.
Unfortunately, this means that mail will be unavailable while the upgrades are deployed. However, this is preferable to the downtime and costs incurred by a successful ransom attack.
To read more, please check eScan Blog







