Ransomware gang is using a Linux variation to maximize damage on VMware’s virtual machine platform behind the well-popularized attack on CD Projekt Red.
As the organizations advance more and more towards virtual machinery, ransomware gangs develop their strategies to produce Linux encryptors for these servers.
The virtual machine platform VMware ESXi is one of the most popular companies. In the last year, more Ransomware gangs have released Linux encryptors aiming at the platform.
ESXi is not precisely Linux because it utilizes its own client kernel, but has other similar features, including ELF64 Linux.
HelloKitty’s Shift Towards ESXi
A team of security scientists has uncovered many HelloKitty ransomware versions for HelloKitty ELF64, which target ESXi servers and virtual machines.
It is known that HelloKitty uses a Linux encrypter, however, this is the first example to be found publicly by researchers.
The team of researchers provided ransomware samples with an online tech publication, and clearly shows strings referring to ESXi and the Ransomware efforts to shut down virtual machines.
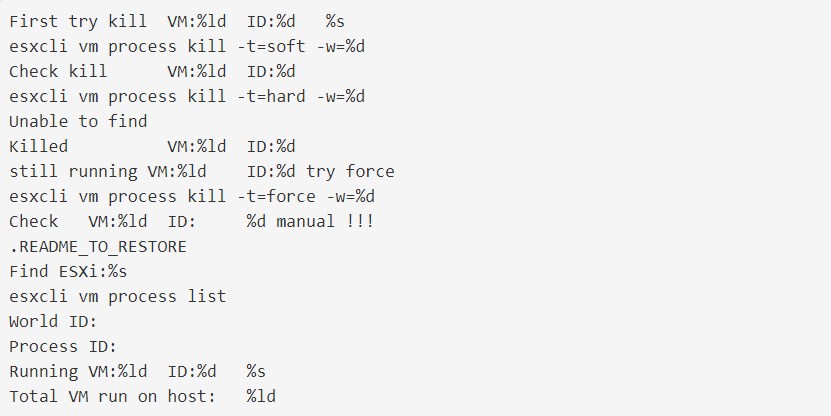
From the debugs, we can observe that the ransomware uses a command-line management tool called esxcli from ESXi to list and then shut down virtual devices that run on the server.
Before encrypting files the ransomware gangs targeting ESXi server would shut down virtual machines to prevent files from being locked and to prevent data corruption.
The Ransomware first tries a graceful shutdown using the ‘soft’ command when it shuts down the virtual machines:

If VMs continue to work, the ‘hard’ command will attempt to stop virtual machines immediately:

Finally, if virtual machines still work, the malware uses the ‘force’ command to powerfully shut down operating VMs.

After shutdowns on the virtual machine, ransomware begins to encrypt files such as .vmdk (virtual hard disk), .vmsd (metadata & snapshot information) and .vmsn (active status of VM) files.
This is a very effective way to encode multiple virtual computers with one command by a ransomware gang.
During the last months, a Linux version of the REvil ransomware was found by the same security research team that targeted ESXi systems and used the command esxcli as part of the encryption process.
Some other active and defunct ransomware had also designed Linux encryptors to target virtual machines for ESXi.
ESXi is specifically being targeted and hence most ransomware groups have implemented Linux-based versions of their ransomware.
HelloKitty
Since November 2020, HelloKity has been in use when the victim first posted the ransomware across online forums.
In comparison with other human-operated ransomware businesses, this specific threat actor has not been especially active since then.
Their most common attack was against CD Project Red where the threat actors threaten to encrypt devices and claimed that Cyberpunk 2077, Witcher 3, Gwent, and more had their source code stolen.
The actors in question afterward said that somebody had bought CD Projekt Red’s data stolen.
This ransomware is used under various names, including DeathRansom and Fivehands.
To read more, please check eScan Blog