A new ransomware is being utilized by threat actors across the world called DearCry or Doejo Crypt. This ransomware is being put to use after the Microsoft Exchange Servers are hacked by using the recently disclosed ProxyLogon Vulnerability.
Since Microsoft’s disclosure of threat actors compromising Microsoft Exchange servers using new zero-day ProxyLogon vulnerabilities, there is a huge amount of concern on how the threat actors would exploit this vulnerability further.
This fear unfurled into reality when the threat actors started using the very vulnerability to install the DearCry Ransomware.
DearCry is not uniquely sophisticated, rather it is crude in nature. It lacks the basic obfuscation techniques that would have made it harder to detect and mitigate. Although, it does encrypt certain kinds of files that makes it harder for the user to use the system.
The ransomware also has some limited similarities with the notorious Wannacry. Both ransomware make copies of a targeted file before overwriting it with visible gibberish. The header also resembles the header used by Wannacry in certain ways.
Let’s understand how DearCry Ransomware encrypts computer
Researchers retrieved 3 samples of this ransomware all of which are MingW-compiled executables. The one that was analyzed included the following PDB path –
C:\Users\john\Documents\Visual Studio 2008\Projects\EncryptFile -svcV2\Release\EncryptFile.exe.pdb
Upon execution of the Dearcry Ransomware, a Windows service named ‘msupdate’ is created, which starts the encryption process. When the encryption process is complete the Windows service is then removed.
The ransomware then encrypts the files with the following extensions, if they are present on the target system –
.TIF .TIFF .PDF .XLS .XLSX .XLTM .PS .PPS .PPT .PPTX .DOC .DOCX .LOG .MSG .RTF .TEX .TXT .CAD .WPS .EML .INI .CSS .HTM .HTML .XHTML .JS .JSP .PHP .KEYCHAIN .PEM .SQL .APK .APP .BAT .CGI .ASPX .CER .CFM .C .CPP .GO .CONFIG .PL .PY .DWG .XML .JPG .BMP .PNG .EXE .DLL .CAD .AVI .H.CSV .DAT .ISO .PST .PGD .7Z .RAR .ZIP .ZIPX .TAR .PDB .BIN .DB .MDB .MDF .BAK .LOG .EDB .STM .DBF .ORA .GPG .EDB .MFS
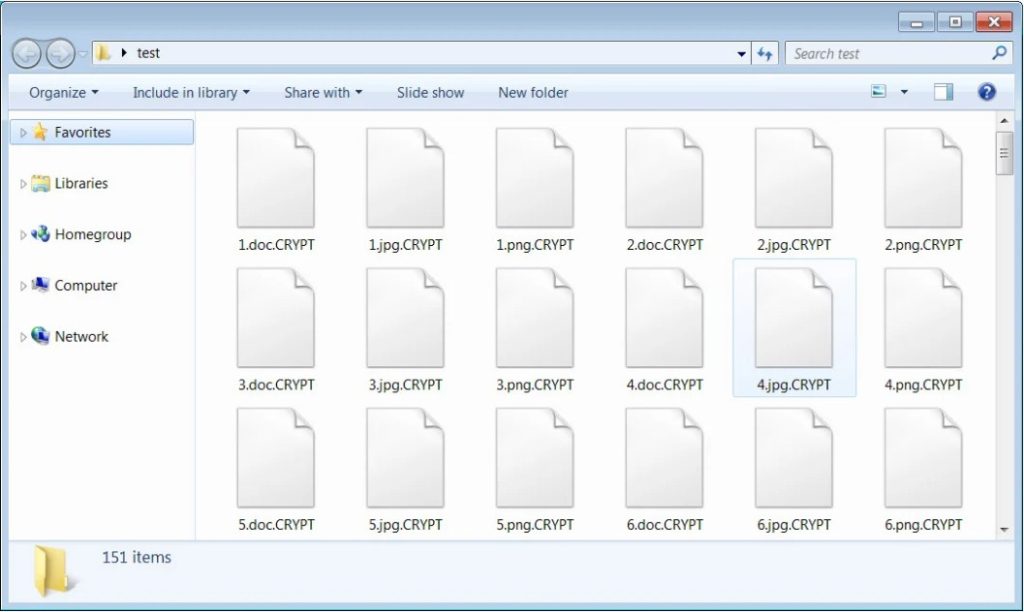
the .CRYPT extension is appended to the files while encryption, as shown below –
A public RSA-2048 key was found to be embedded in each sample of DearCry Ransomware.
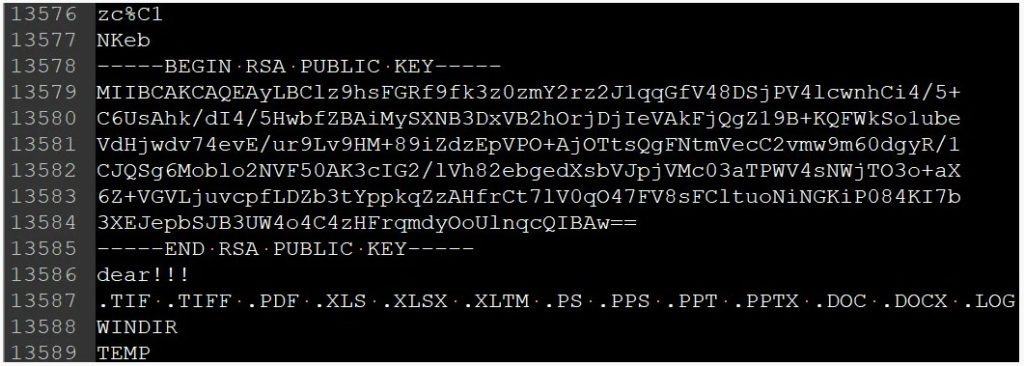
The ransomware uses AES-256 to encrypt the files and the RSA-2048 public key to encrypt the AES key.
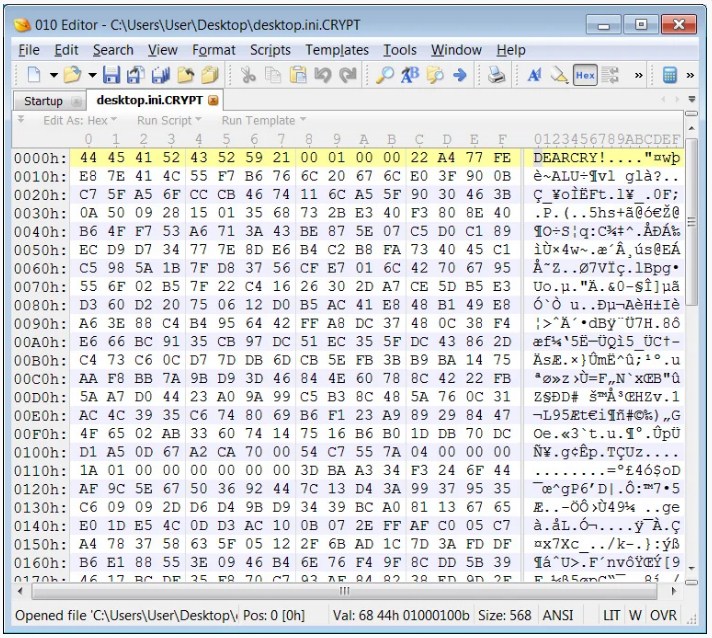
The ‘DEARCRY!’ string is also prepended to the beginning of each encrypted file by the ransomware.
< DEARCRY file marker in encrypted file>
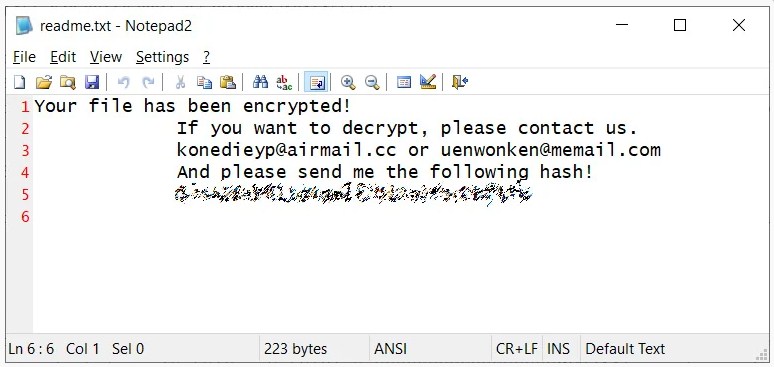
When the process of encrypting files in the computer is done, a simple ransom note is created titled “readme.txt” on the Windows desktop. The ransom note consists of two email addresses for the threat actors and a unique hash which according to researchers is an MD4 hash of the RSA public key embedded in the malware.
<DearCry ransom note>
Currently, the ransomware seems to be void of any weaknesses that would allow victims to recover their files for free.
Our internal experts suggest organizations and security professionals to apply the patches as soon as possible and create offline backups of their Exchange servers to protect their mailboxes from being stolen or encrypted.
Associated DearCry
hashes:
SHA256: 2b9838da7edb0decd32b086e47a31e8f5733b5981ad8247a2f9508e232589bff
SHA256: e044d9f2d0f1260c3f4a543a1e67f33fcac265be114a1b135fd575b860d2b8c6
SHA256: feb3e6d30ba573ba23f3bd1291ca173b7879706d1fe039c34d53a4fdcdf33ede
SHA256: FDEC933CA1DD1387D970EEEA32CE5D1F87940DFB6A403AB5FC149813726CBD65
SHA256: 10BCE0FF6597F347C3CCA8363B7C81A8BFF52D2FF81245CD1E66A6E11AEB25DA
Associated DearCry emails:
konedieyp@airmail.cc
uenwonken@memail.com
DearCry ransom note text:
Your file has been encrypted!
If you want to decrypt, please contact us.
konedieyp@airmail.cc or uenwonken@memail.com
And please send me the following hash!
[Victim ID]
To read more, please check eScan Blog







