Used in recent North Korean attacks against security and vulnerability researchers, An Internet Explorer zero-day vulnerability has been discovered.
Google last month disclosed that the Lazarus group was conducting social engineering attacks against security researchers.
Elaborate online ‘security researcher’ personas were created to perform their attacks. These personas would then use social media to contact well-known security researchers to collaborate on vulnerability and exploit development.
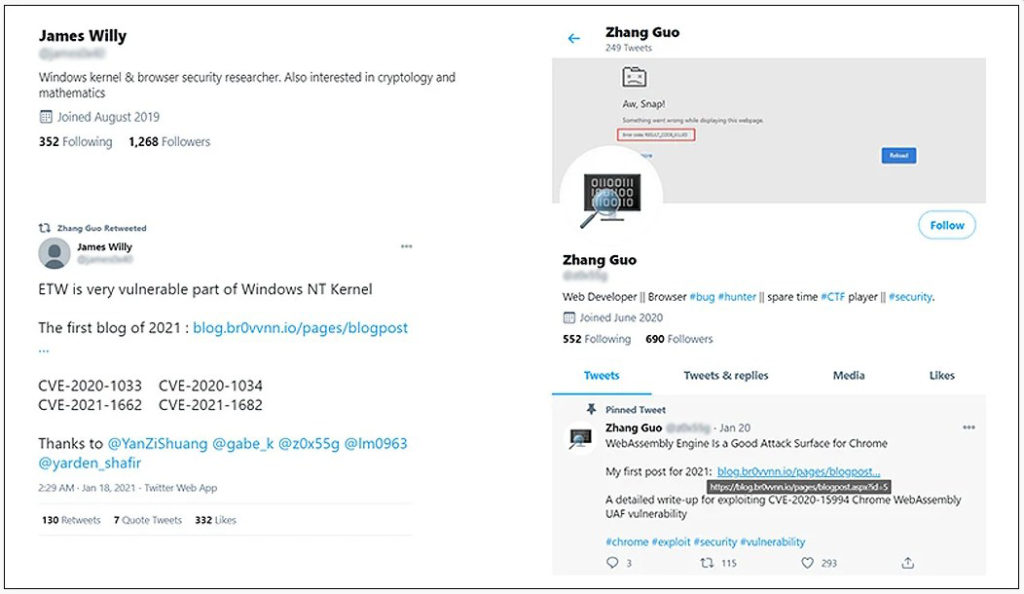
The attackers sent malicious Visual Studio Projects and links to websites hosting exploit kits that would install backdoors on the researcher’s computers, as a part of this collaboration.
The attacks were being tracked by tech giants Microsoft and they had discovered the Lazarus group was sending MHTML files to the researchers with a malicious javascript. During the course of the investigation, Microsoft could not investigate further payloads since the command and control server was down.
Recently, a South-Korean security firm also reported that Lazarus targeted security researchers on their team with MHTML files in this social engineering campaign.
They claimed the attacks had failed but they managed to analyze the payloads downloaded by the MHT file and discovered it contained an exploit for an Internet Explorer zero-day vulnerability.
Otherwise known as MIME HTML, an MHT/MHTML file is a special file format used by Internet Explorer to store a web page and its resources in a single archive file.
The MHT file sent to ENKI researchers contained what was allegedly a Chrome 85 RCE exploit and was named ‘Chrome_85_RCE_Full_Exploit_Code.mht.’
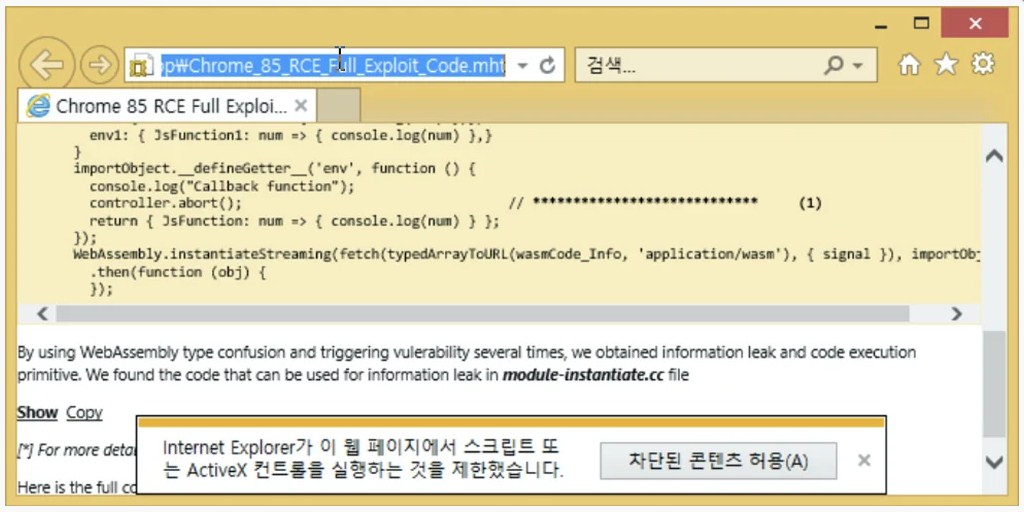
Internet Explorer automatically launched to display the contents of the MHT file as soon as the MHT/MHTML file was opened. If script execution is allowed, then malicious javascript would download two payloads, with one containing a zero-day against Internet Explorer.
A double-free bug in IE 11 is abused by this exploit allowing the attackers to upload a list of the running process, screen captures, and network information to their command and control server. For further execution, it would then download and execute additional malicious code from the C2 server.
It is believed that other security researchers have knowledge of this IE 11 zero-day, based on the tweets from them.
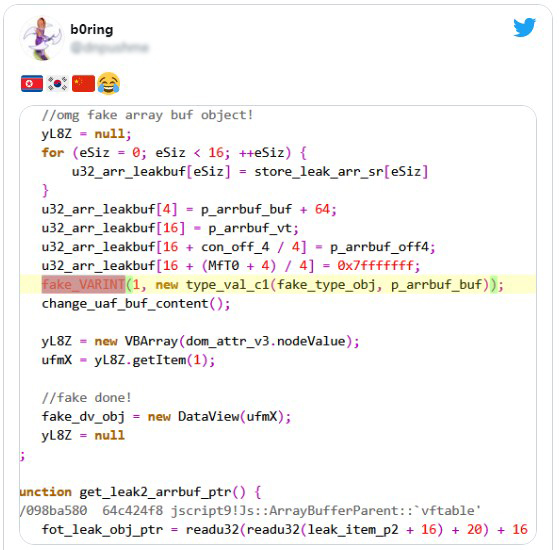
Microsoft has promised an update in the near future after investigating every report they have received on this subject.
To read more, please check eScan Blog







